ThreatQ and Phantom: Injecting Contextual Threat Intel into Security Automation and Orchestration
POSTED BY JULIAN DEFRONZOThe emergence of automation and orchestration tools in the security space has helped enhance security analyst and incident response workflows. These solutions allow you to automate most, if not all, of your existing processes and procedures.
The basic incident response workflow that most of us are familiar with is made-up of four steps: Preparation; Detection and Analysis; Containment, Eradication, and Recovery; and the Post-Incident Activity.
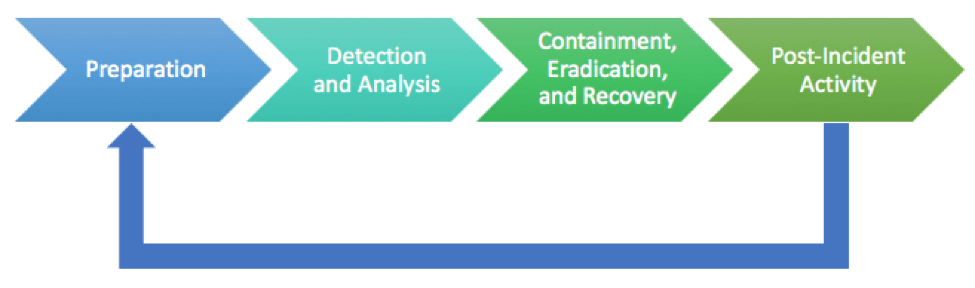
Security automation and orchestration platforms provide automation for these processes end-to-end. Work that was once performed across multiple tools and teams manually can now be unified into a single system.
A common example is the response to a malware alert in your environment. Below is a basic approach to automating the “Detection and Analysis” and “Containment, Eradication, and Recovery” phases.
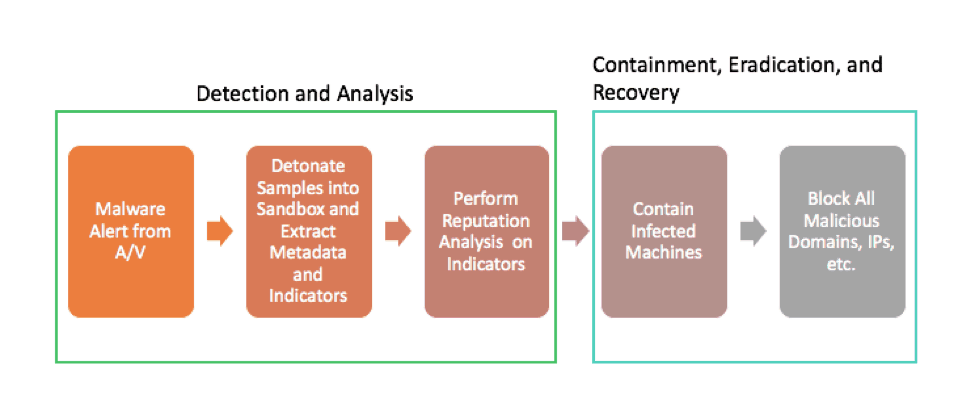
This is a common process that incident response teams will follow each time there is a malware alert, making it a prime candidate for automation. Through automation, we go from a complex process to a streamlined, automated workflow that will be completed significantly faster than if it were performed manually, allowing analysts to focus on critical decision-making and analysis.
ThreatQ and Phantom Together
ThreatQuotient has partnered with Phantom to develop a Phantom App that integrates seamlessly into existing Phantom Playbooks. Many of the actions that you can do within the ThreatQ threat intelligence platform have also been integrated as Actions, allowing Phantom to pull in enrichment from the ThreatQ Threat Library into Playbooks and create new indicators, events, adversaries, and files within the ThreatQ Threat Library. As you will see the combination of the ThreatQ Threat Library and the Phantom Platform is extremely powerful within incident response as well as a company’s entire threat operations.
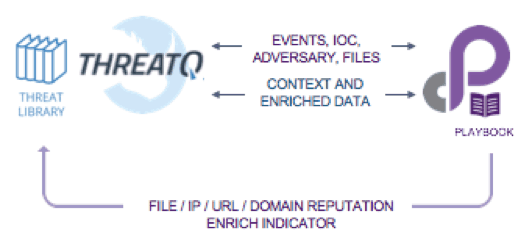
The Phantom App for ThreatQ provides the Phantom Platform with enrichment data from the ThreatQ Threat Library within the “Detection and Analysis” phase of the incident response workflow enabling contextual decision-making based on the results. Instead of blocking any and all IP addresses, you now have curated data from your ThreatQ platform to make more granular and selective blocking decisions.
New indicators created in ThreatQ originating from malware samples detonated in a sandbox is another example of this automation. This creates a feedback loop of updated information as the data is brought back into Phantom through enrichment.
Below are the supported actions that are included in the App:
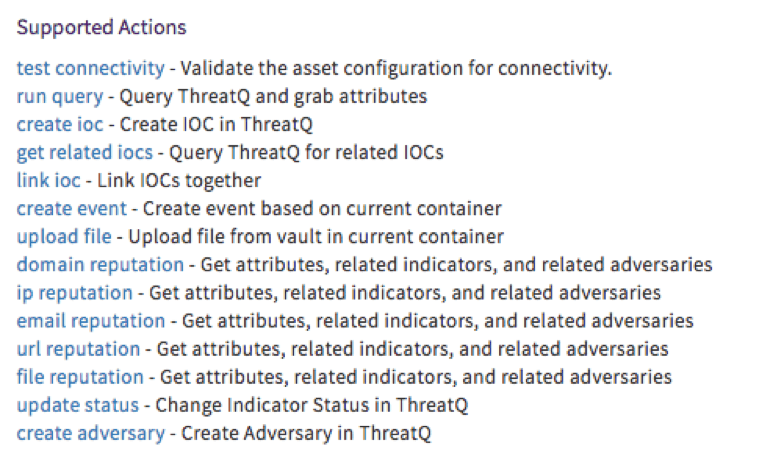
This extensive set of actions provided by the Phantom App enables a highly effective interaction between the Phantom and ThreatQ platforms.
Malware Response Playbook
Continuing to work through our “Malware Alert” example, below is a Phantom Playbook that uses the ThreatQ threat intelligence platform to inject contextual data which allows for better decision-making. In the interest of simplicity, the playbook is focused on actions against IP addresses, but can be expanded to include other IOC types and actions.
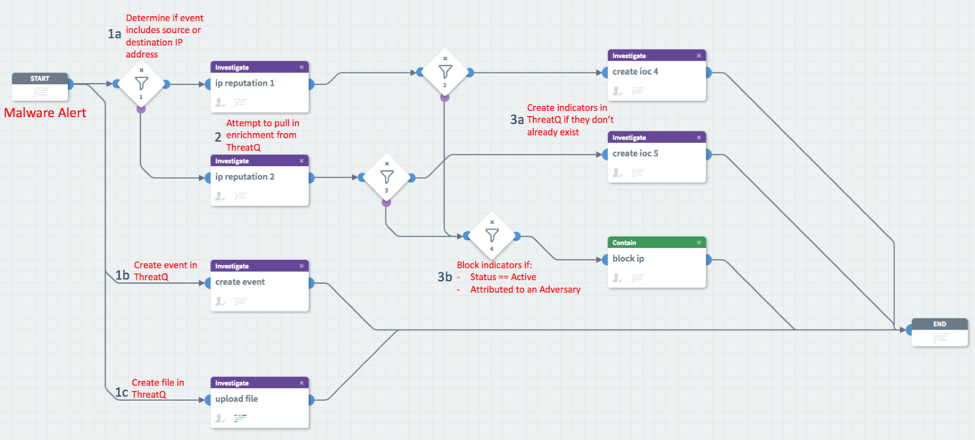
The playbook starts with a malware alert and ends with potentially blocking an IP address. You can see that it will leverage ThreatQ to provide enrichment of the indicator to determine if IP address should be blocked. The playbook will also automatically create new indicators, events, and files within the ThreatQ platform (which can be used for future analysis).
Step 1a is a decision step that determines the directionality of the event (source or destination IP address). The steps following are the same for each path, but it’s crucial to determine which fields to parse and pass along to future steps.
Steps 1b and 1c create an event and upload any files into ThreatQ respectively. The newly created event will include complete details from the original incident, including sensitivity and severity. From the Phantom web interface, you will see that the actions provide links back to the ThreatQ UI.
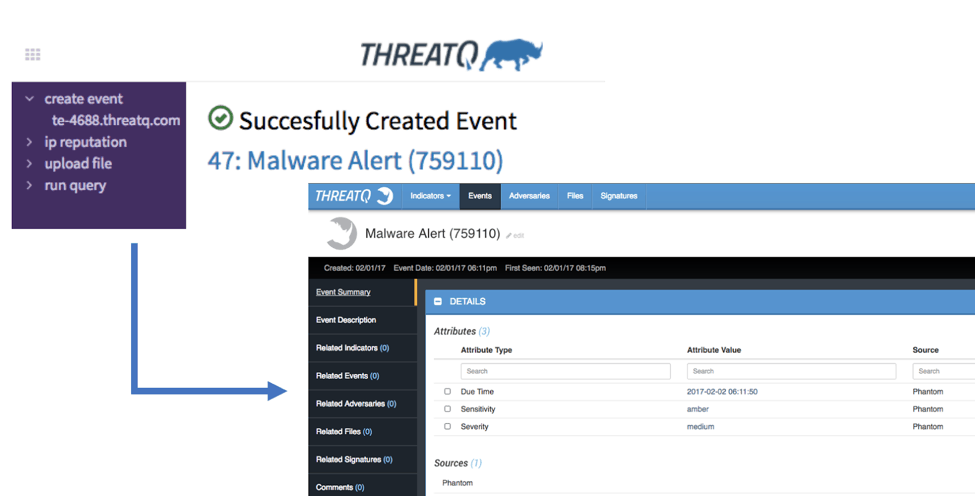
Newly Created Event
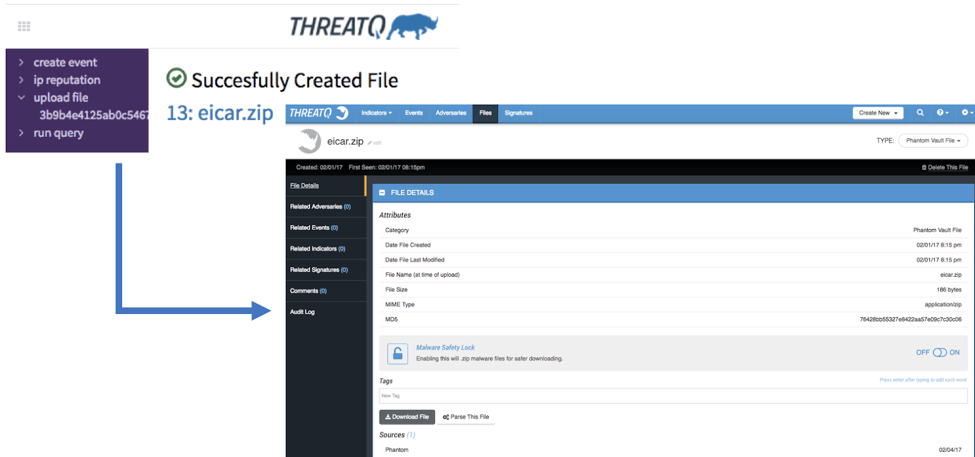
Newly Created File
In step 2 we perform the “ip reputation” action on the IP address artifacts. This action will pull in all the relevant information from the ThreatQ Threat Library on the IP address, including but not limited to the status of the indicator, any attributes, any related indicators, and if the indicator has been attributed to an adversary. For example, we have a screenshot of the completed action as initiated from the Phantom UI.
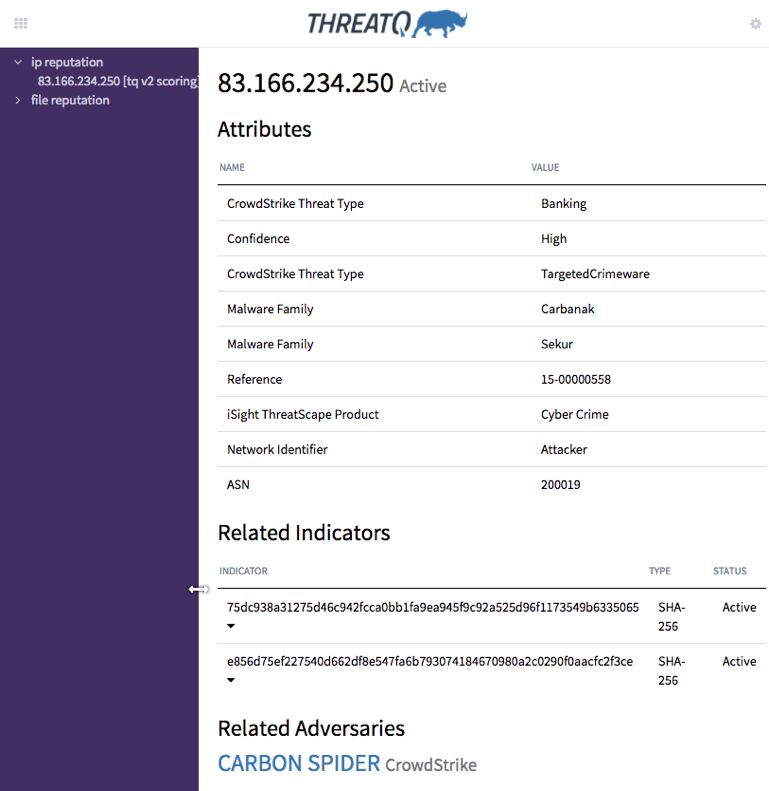
In this example, we see that the IP address has a lot of data associated with it. The data provided by this step allows us to inject curated and correlated data on indicators from ThreatQ threat intelligence platform into any future actions and decisions throughout the later stages of the playbook, thus utilizing intelligence in the incident response workflow.
In step 3a we create a decision step that will determine if the previous “ip reputation” action returned with any data. If we have data from the previous step, we will move on to the next decision step (step 3b) to determine if we should block the IP address. If we have no data from the previous step, meaning the indicator does not exist in ThreatQ, we go ahead and create it in ThreatQ.
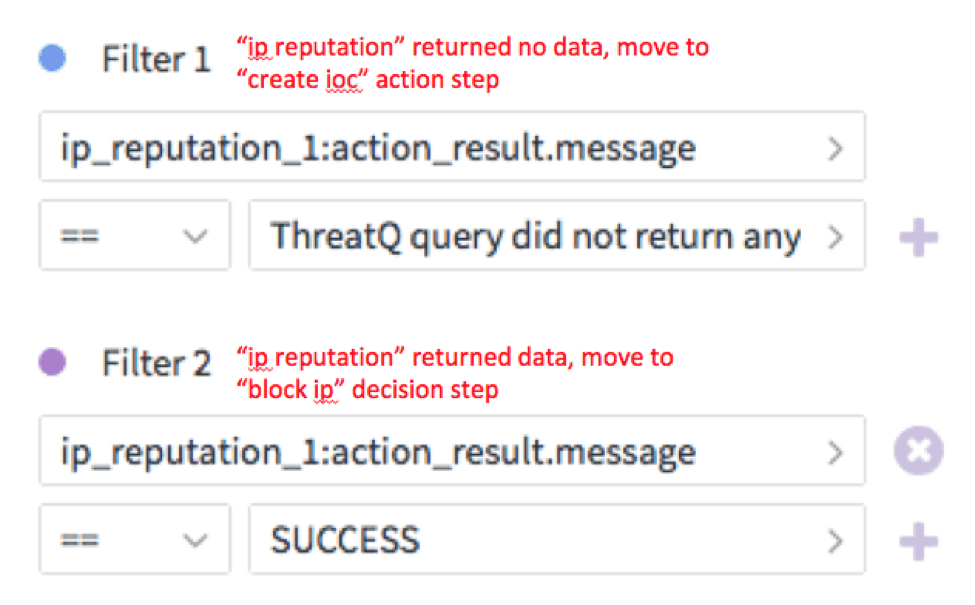
After this decision, we move to step 3b which is a decision step:
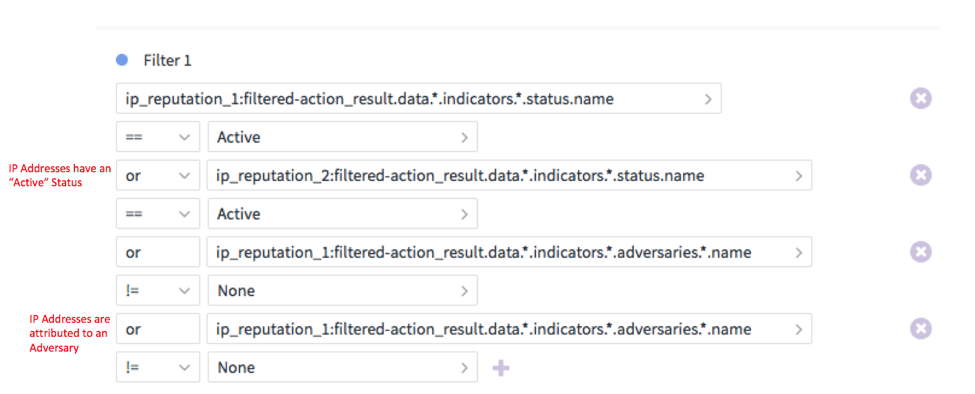
This step checks to see the status of the indicators being passed to it and the presence of any adversaries. If any of these checks pass, we will block the IP address at our firewall using the “block ip” action. This playbook can be expanded to include reputation actions for files, URLs, domains, and hashes which can feed into this decision step and result in the blocking of those indicators as well.
As you can see, we’ve now fully automated the end-to-end response to a malware alert. While many existing playbooks already use reputation actions that utilize open-source intelligence, by integrating with the ThreatQ threat intelligence platform you are provided with contextual data that allows for better, more informed decision making before taking further action and automatically blocking the IP address at the firewall. In addition, by automatically creating newly seen indicators, events, and files, we provide a feedback loop that further enhances the ThreatQ Threat Library to provide more contextual data for future analysis in ThreatQ and playbooks run by Phantom.

0 Comments