I want more “Stuff.”
POSTED BY KEVIN LIBBY“Everybody’s gotta have a little place for their stuff. That’s all life is about. Trying to find a place for your stuff.” — George Carlin
Among some of the more memorable nuggets from George Carlin that fed my brain during my youth was his perspective on “stuff.” Perhaps that’s why I seem to have spent a large part of my lifetime trying my best not to acquire stuff. I’ve always preferred to maintain a minimalistic, less-is-more type environment in the various homes I’ve occupied over the years. In short: I don’t like clutter.
But when it comes to collecting data while building better situational awareness against cyber attacks, it turns out I’m a hoarder. If I’m able to acquire malware samples, packet captures, threat intelligence reports, and any other potential evidence or data points to associate with the external and internal adversaries I’m tracking then in my view, the more “stuff” I have the better. And I bet most analysts feel the same.
To help you deal with this overload of stuff, the ThreatQ threat intelligence platform is comprised of three key pillars to streamline threat operations and management: the Threat Library, Adaptive Workbench and Open Exchange.
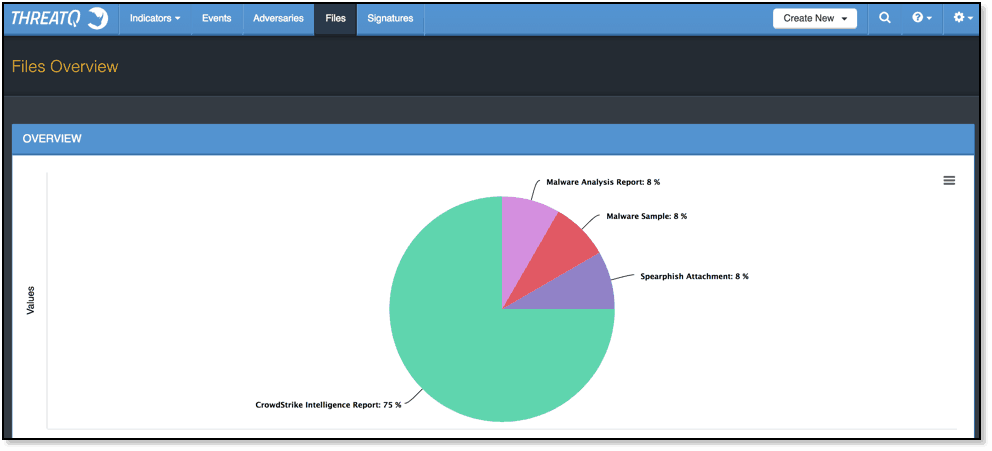
ThreatQ’s Threat Library is where I can house all the data I’ve been gathering. The best part is much of this populates without any hands-on effort. For example, files are received from various cyber threat intelligence providers and contain information on indicators and adversaries. This data is automatically parsed out and related to the original file source.
To add to the mix, my ThreatQ appliance integrates with Cisco ThreatGrid and LastLine. Thanks to ThreatQ’s Open Exchange, it doesn’t matter what sandbox environments I use. If the tool has an accessible API, then it’s normally fairly trivial to push data back and forth. I could integrate additional sandbox environments from other vendors anytime I want.
Thanks to the Adaptive Workbench, whenever I, or someone on my team, uploads potentially malicious files for analysis, I don’t spend time moving the files over from one environment to another or ensuring that every indicator has been copied and pasted into my Threat Intelligence Platform (TIP). ThreatQ reaches into my sandbox environment and ingests this data automatically.
Within the ThreatQ threat intelligence platform, I’m able to immediately find out if malware is associated with indicators and/or adversaries I’m already tracking by simply pivoting off the file within ThreatQ or looking for Related Files as I glance over events, signatures, and indicator or adversary overviews. Of course, if I want to read the original reports then I’m able to on-demand via ThreatQ.
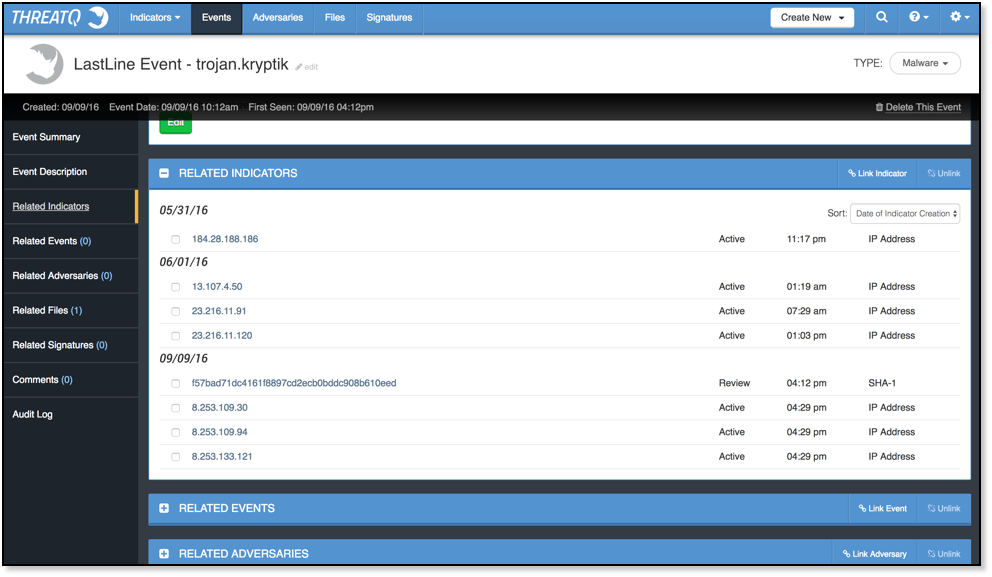
Finally, I’ve found a place for my stuff. George Carlin would be pleased.

0 Comments