THREATQ™
Threat Intelligence Platform
To understand and stop threats more effectively and efficiently your existing security infrastructure and people need to work smarter, not harder. ThreatQ is a data-driven threat intelligence platform that allows you to automate the intelligence lifecycle, quickly understand threats, make better decisions and accelerate threat detection, investigation and response.
GAIN MORE FROM YOUR EXISTING SECURITY INVESTMENTS –
PEOPLE AND TECHNOLOGIES

HOW THREATQ WORKS:
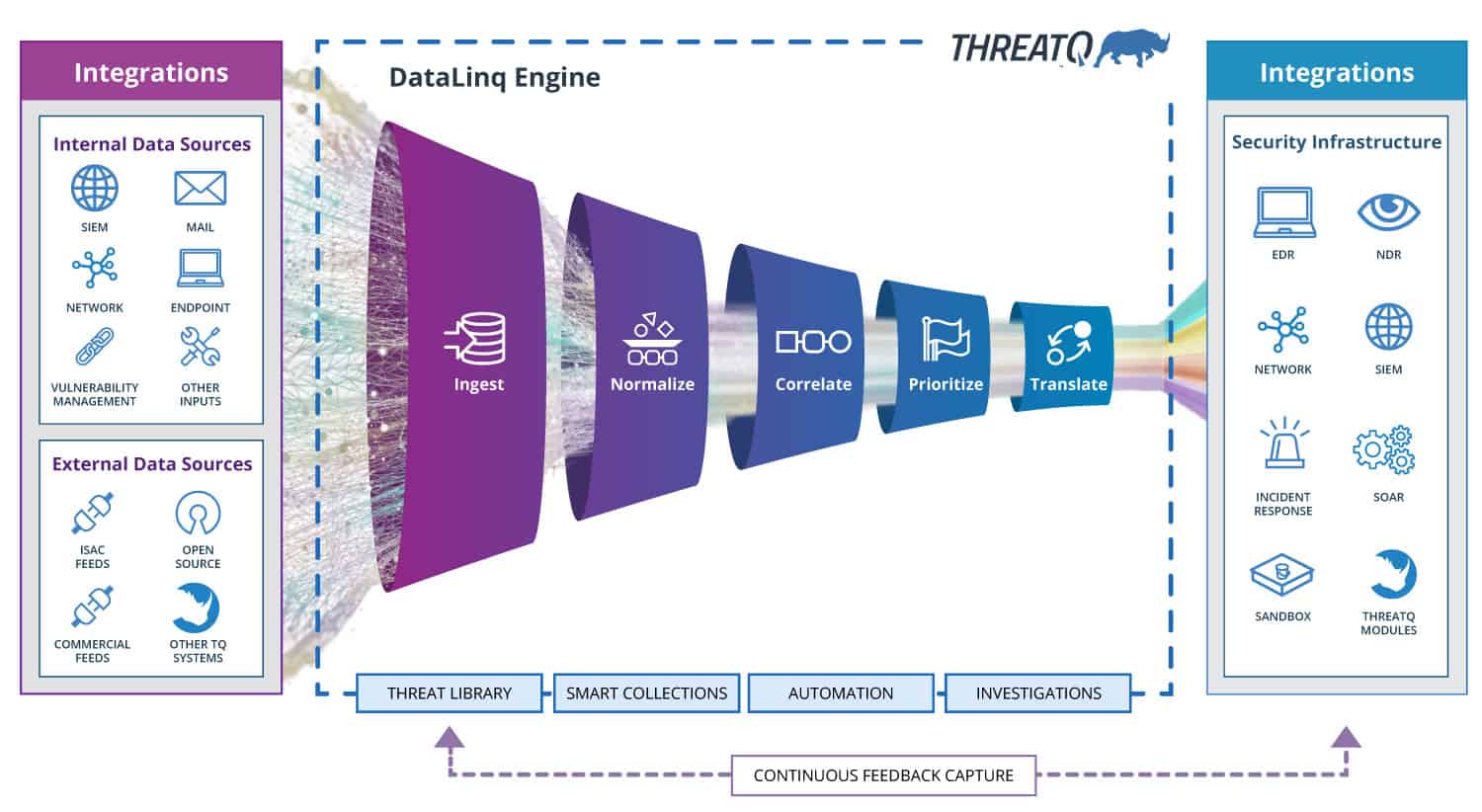
DATALINQ ENGINE™
Combine Threat Data From Any Source, Internal And External
Connecting disparate systems and sources, this adaptive data engine imports and aggregates external and internal data; curates and analyzes data for decision making and action; and exports the right intelligence to the right tools at the right time to accelerate threat detection, investigation and response (TDIR).
- INGEST and aggregate structured and unstructured data via Marketplace apps and an open API
- NORMALIZE automatically from different sources, formats and languages into a single object
- CORRELATE across atomic pieces of data to identify relationships and provide a unified view
- PRIORITIZE via customer controlled, dynamic scoring to ensure relevance and filter noise
- TRANSLATE data into the format and language necessary for consumption across systems
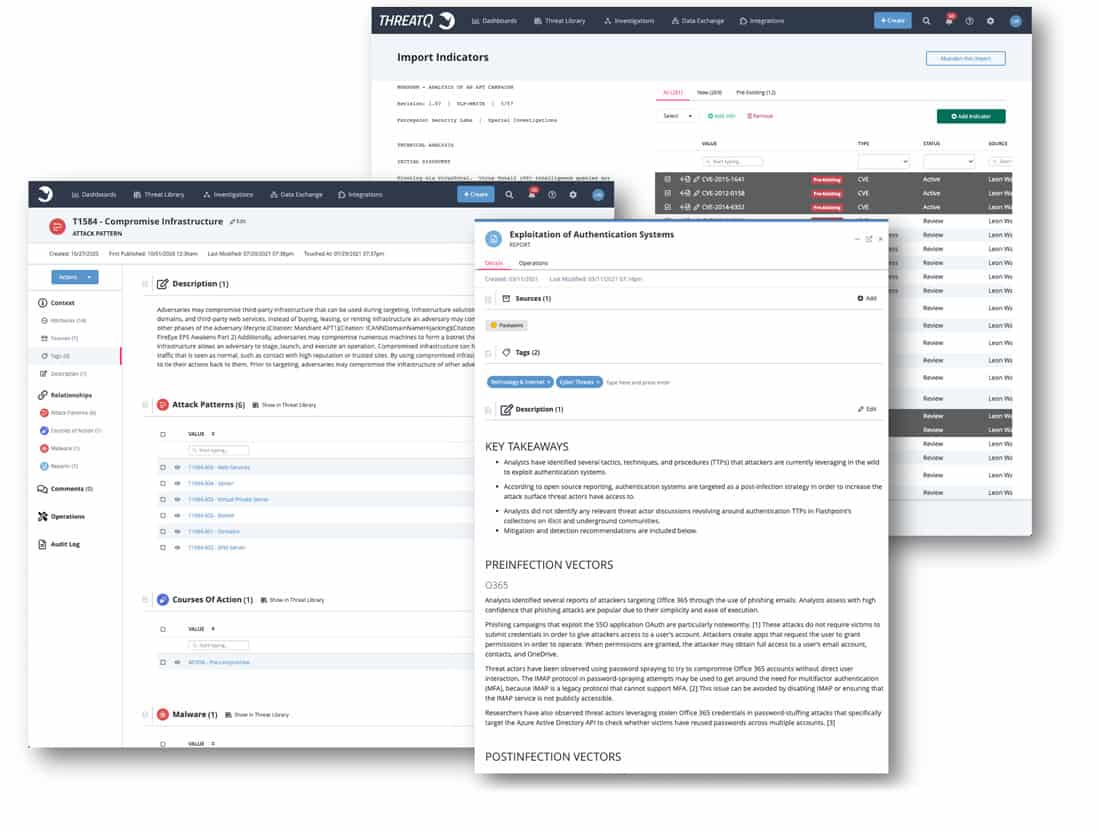
THREAT LIBRARY
Shared Contextual Intelligence
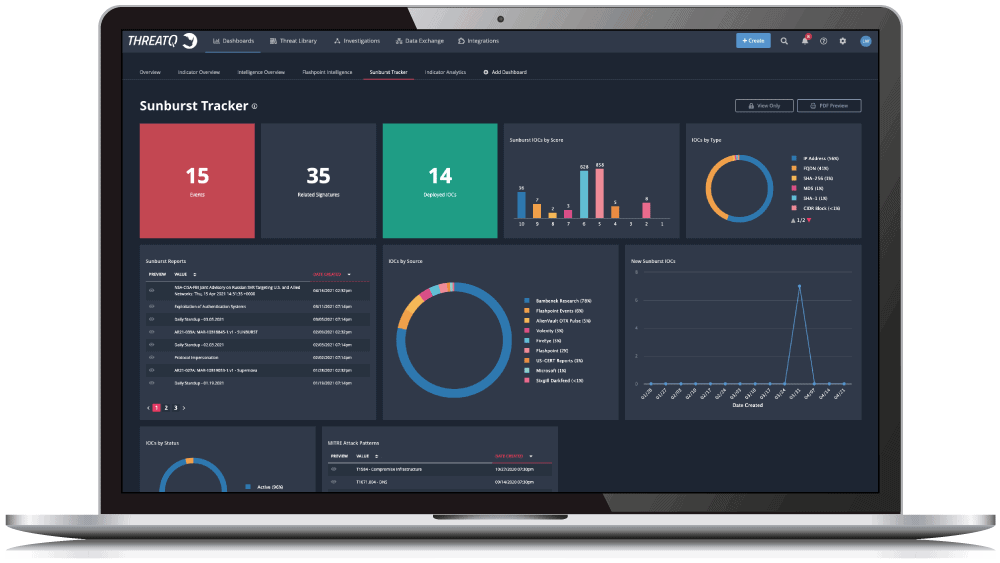
Using ThreatQ as a threat intelligence platform equips you with a threat library that automatically scores and prioritizes intelligence based on parameters you set. Prioritization is calculated across many sources, both external and internal, to deliver a single source of truth using aggregated context. This removes noise, reduces false positives and enables users to focus on the data that really matters.
- Extensible Data Model
- Consolidated view, unified opinion
- Automatically prioritize based on all sources
- Custom enrichment source for existing systems
- Define Smart Collections for workflows and automation
THREATQ TDR ORCHESTRATOR
Data-drive, no-code/low-code automation
ThreatQ TDR Orchestrator simplifies orchestration and automation through a no-code/low-code, data-driven approach which “puts the smarts into the platform.” ThreatQ does this through data curation and extracts much of the complexity of process-driven playbooks. Update the platform once vs having to update dozens of playbooks.
- Easy to set-up and maintain
- Reduce playbook runs by 80%
- Ensure output is relevant and high priority
- Learn from the actions taken, and improve over time
- Harness Generative AI and Natural Language Processing (NLP)
THREATQ INVESTIGATIONS
The industry’s first cybersecurity situation room
ThreatQ Investigations removes the collaboration and coordination inefficiencies that exist across security operations to accelerate detection and response. As the first cybersecurity situation room, it streamlines investigations and improves active collaboration among and across teams. Team leaders can direct actions, assign tasks and see the results unfold in near real time.
- Fuse together threat data, actions, and users
- Combine automation and human intelligence
- Accelerate investigation, understanding and response to threats
- Build incident, adversary and campaign timelines
- Drive down mean time to detect (MTTD) and mean time to respond (MTTR)
MARKETPLACE
Open and Extensible Architecture Enables Robust Ecosystem
Get more from your existing security investments by integrating your tools, teams and workflows through standard interfaces and an SDK/API for customization.
- Bring your own connectors and tools
- SDK / API for customization
- Standard STIX/TAXII support
THREATQ SOLUTION ARCHITECTURE
ThreatQ, used as a threat intelligence platform, supports both standard and custom integrations with feeds and security systems. Through these integrations the platform automates the aggregation, operationalization and use of threat intelligence across the entire security infrastructure, supporting multiple use cases, increasing security effectiveness and accelerating security operations.
LET’S GET STARTED!
FLEXIBLE DEPLOYMENT OPTIONS
TO FIT YOUR NETWORK DESIGN
On-Premises
For maximum security, ThreatQ can be deployed solely on-premise, providing you complete control over your data.
Cloud-Based
ThreatQ can be deployed in various cloud-based environments.
Air-Gapped
ThreatQ can be deployed in a secure, air-gapped environment to protect your systems and data as well as meeting any compliance requirements.
THREATQ MARKETPLACE
Integrate your existing security solutions within a data-driven threat intelligence platform. ThreatQ supports an ecosystem of over 450 product and feed integrations, provides the ThreatQ Integration Framework including easy-to-use tools for custom integrations, streamlining threat detection, investigation and response across your security infrastructure.
