What is a Threat Library?
A customized threat library aggregates into a central repository the millions of threat-focused data points security teams are bombarded with every day. It augments and enriches that global threat data with internal threat and event data from the company’s own tools, including the security information and event management (SIEM) system, log management repository and case management systems. This provides context for automatic scoring and prioritization of threat intelligence based on parameters that the teams set and is an important component of threat intelligence management. By removing the noise and reducing the risk of false positives, users can focus on the data that really matters to their organization.
How does a Threat Library work?
A threat library should do three things:

Organize
Serve as an organized, indexed and searchable location for structured and unstructured security information from external and internal sources.
Data collected into the threat library needs to be personalized and context-specific to the company or network it is being used to protect.

Accommodate
Be easily accessible not only from a native interface, web or otherwise, but it should also provide enterprise-wide systems with access to the data through APIs or other easily accessible means.
Users must be able to access the data from whatever tool they are using as part of their current workflow without having to stop what they are doing and access another interface.

Aggregate
Automatically aggregate and normalize data while maintaining a consistent trail of information on what has been added or modified, by whom and when.
A threat library should maintain an audit history so that users can ensure the right feeds are on, the right enrichment is occurring and the right scoring policy is in place.
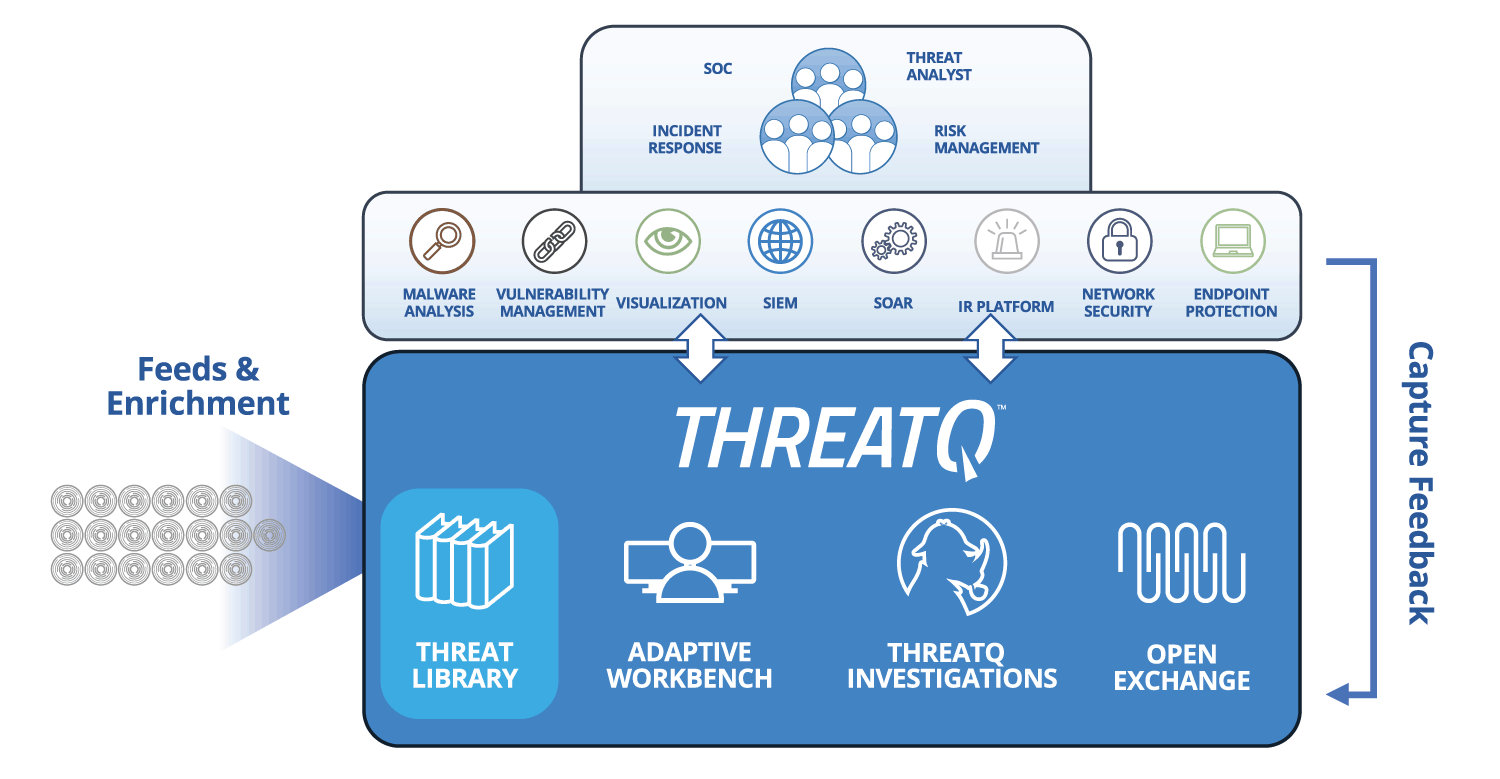
The ThreatQ open and extensible platform integrates disparate security technologies into a single security infrastructure, automating actions and workflows so that tools and people can work in unison.
LET’S GET STARTED!
“ThreatQ automatically associates indicators to an event so we can quickly pivot and determine the right priority. Instead of wasting time on what ends up being ‘meh’, we’re focused on what matters. ThreatQ has saved us a lot of time – and that’s incredibly valuable as a threat intel analyst.”
Global Hospitality and Entertainment Company
What is the value of a Threat Library?
A threat library is the heart of security operations. It allows users to handle integrations from any source – structured or unstructured, internal or external. They can validate how the threat data is scored and prioritized to ensure they aren’t missing valuable context. And because threat intelligence is being catalogued, the entire security operations team can understand the context to use it more effectively.
