What is MITRE ATT&CK?
MITRE ATT&CK
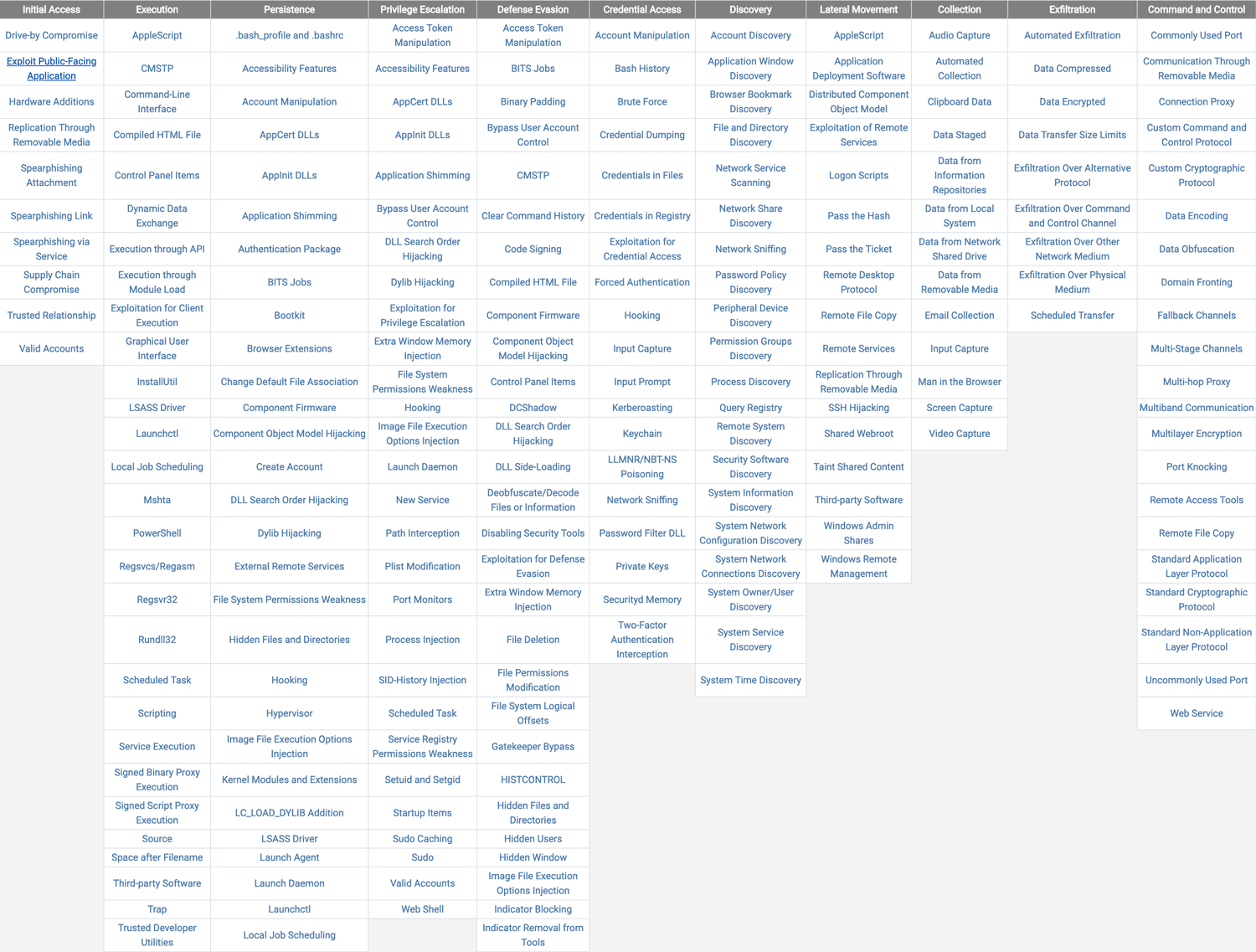
MITRE ATT&CK™ (Adversarial Tactics, Techniques & Common Knowledge) is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community. (1)
MITRE ATT&CK consists of 3 matrices; Pre-Att&CK, Enterprise Att&CK and mobile. Together, they comprise an end to end attack chain that dives deep into adversaries’ actions to help security analysts accelerate detection and response. At each step of the way, threat data informs the chain – real threat reports, not speculation – with the focus being on adversaries’ behavior, not the tools they use.
Benefits of the MITRE ATT&CK framework:
- Structures/organizes adversary techniques, tools and protocols (TTPs) analysis
- Actor-centric description
- Roadmap to simulate ‘real-world’ adversary attacks
- Provides an initial attempt re: how vendor technology defends against attacks
- Kickstart red/blue/purple teams and hunting efforts
- Part of an 8 framework ‘bigger picture’ roadmap from Mitre
Example use cases for the ATT&CK framework:
- Gap analysis of current defenses to improve security posture
- Detection of heavily used techniques so analysts can prioritize what to look for
- Information sharing of observed behaviors on the network among security teams
- Mapping of tactics and techniques to related data within the environment for threat hunting
- Tracking the evolution of tactics, techniques, and procedures (TTP) over time and building adversary profiles
- Adversary emulation for red team/blue team exercises
THREATQ AND MITRE ATT&CK
ThreatQ’s deep integration with MITRE ATT&CK is designed to automate the creation of relationships between inbound data in the ThreatQ platform and MITRE ATT&CK Techniques. It is a flexible integration that enables a user to map external sources of data to individual MITRE ATT&CK techniques. Once mapped, ThreatQ will automatically associate both events and indicators to the assigned Techniques. A user may then leverage ThreatQ Investigations and use the relevant MITRE ATT&CK Technique as the starting point for the investigation. Learn More.
The reality is that breaches happen. The key is responding to them quickly and effectively. Many businesses are very reactive when responding to threats. It is, however, possible to start being proactive with the ThreatQ and MITRE ATT&CK™ integration. There are several use cases for this integration. Threat hunting is just one example.
Security teams can leverage the MITRE ATT&CK framework to assist with hunting activities in multiple ways:
- Enable investigations that originate with components from the MITRE ATT&CK framework such as Techniques.
- Automatically build relationships between MITRE ATT&CK data and other useful pieces of threat data.
- Automatically map threat data from internal sources (e.g. SIEM, Ticketing, Email Gateway) with MITRE ATT&CK techniques (where appropriate).
- Automatically map threat data from external sources (e.g. Feeds) with MITRE ATT&CK techniques (where appropriate).
- Keep historical threat hunting investigations and automatically associate these with related components of the MITRE ATT&CK framework.
A Phased Approach to Threat Hunting using MITRE ATT&CK and ThreatQ
Every organization can derive value from the MITRE ATT&CK framework, but in different ways based on the capabilities of their security operations. For the greatest success, organizations should map the framework to their stage of maturity. As their desire and capabilities to use the data evolve and grow, they’ll be able to dig deeper into the framework and gain even greater value.
Here’s how organizations would evolve and use the integration of ThreatQ and MITRE ATT&CK to their advantage:
Stage 1
Reference and Data Enrichment
Aggregate the data from the framework into ThreatQ and search for adversary profiles to get answers to questions like: Who is this adversary? What techniques and tactics are they using? What mitigations can I apply? Security analysts can use the data from the framework as a detailed source of reference to manually enrich their analysis of events and alerts, inform their investigations and determine the best actions to take depending on relevance and sightings within their environment.
Stage 2
Indicator or Event-driven Response
Use the ThreatQ platform to automatically correlate indicators from the MITRE ATT&CK framework with events and associated indicators from inside the organization’s environment, without having to form those relationships manually. Security analysts can then automatically prioritize based on relevance to their organization and determine high-risk indicators of compromise (IOCs) to investigate within the environment. With the ability to use ATT&CK data in a more simple and automated manner, security teams can investigate and respond to incidents and push threat intelligence to sensors for detection and hunt for threats more effectively.
Stage 3
Proactive Tactic or Technique-driven Threat Hunting
Pivot from searching for indicators to taking advantage of the full breadth of ATT&CK data. Threat hunting teams can take a proactive approach, beginning with the organization’s risk profile, mapping those risks to specific adversaries and their tactics, drilling down to techniques those adversaries are using and then investigating if related data have been identified in the environment. For example, they may be concerned with APT28 and can quickly answer questions including: What techniques do they apply? Have I seen potential IOCs or possible related system events in my organization? Are my endpoint technologies detecting those techniques?