Threat Hunting Using ThreatQ and MITRE ATT&CK
POSTED BY STEVE RIVERS AND NIR YOSHAThe reality is that breaches happen. The key is responding to them quickly and effectively. Many businesses are very reactive when responding to threats. It is, however, possible to start being proactive with the ThreatQ and MITRE Enterprise ATT&CK integration.
MITRE ATT&CK
MITRE ATT&CK provides a structured way to describe adversary TTPs and behaviors. A threat hunting starts with intelligence, and ATT&CK provides the basis for hunters to build their own hypotheses and search for threats.
For demonstration purposes, we’ll use ThreatQ Investigations to look at APT28 and commonly used techniques. We take into account the motivation for an adversary to target your business based on your industry, assets or proprietary information. By using ATT&CK with the indicators and sightings in your network, cyber threat analysts can successfully hunt for unknown threats.
Step 1 – Have we been breached?
ThreatQ Investigations helps connect the dots between adversaries’ behavioral attributes and indicators of compromise. Furthermore, ThreatQ Investigations helps with sightings of malicious activities within the network by cross-correlating IOCs with log entries in the SIEM. As an example (see figure 1), a sighting from the SIEM alerts the analyst on a potential breach by linking a malicious URL to APT28.
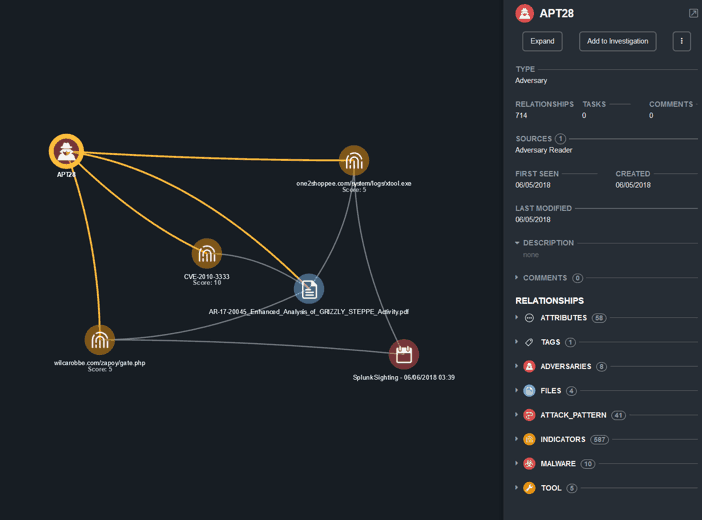
Figure 1 – Sighting of access to malicious URL that is linked to APT28
Step 2 – Understanding the threat
While IOC’s can help with the scoping and initial detection, they can easily be changed by the threat actors. MITRE ATT&CK offers detailed information on tactics, techniques and procedures (TTPs). TTPs are much harder for a threat actor to bypass, therefore providing a stronger defense against any malicious activity that they may choose to engage in. MITRE ATT&CK also offers mitigations that may be used to deploy proactive defenses as well.
ThreatQ Investigations helps a user visually identify TTPs and associated mitigations that may be related to a particular threat. In our example (see figure 2), you can see an investigation opened into APT28. In this case, we see that “Exploitation of remote service” is a common technique used by the “Flame” malware. With that, the IR team can now look into the relevant actions for mitigation provided by ATT&CK.
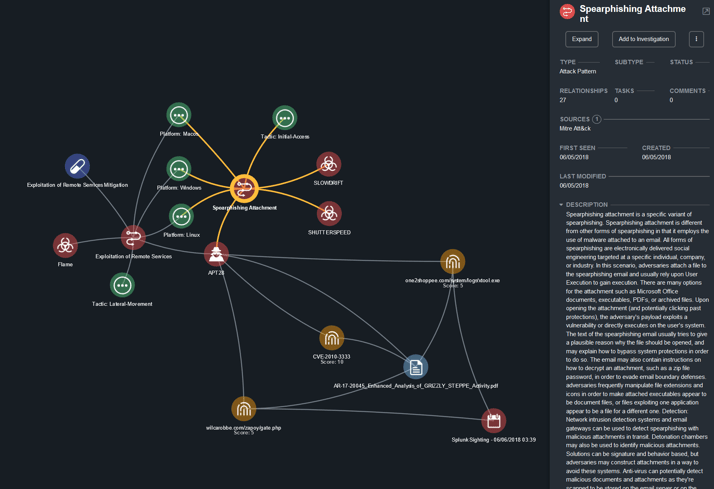
Figure 2 – “Exploitation of remote service” is a common technique used by the “Flame” malware
Step 3 – Preparing the defense
Once we know how a threat actor targets a business, it is possible to start preparing appropriate defenses to identify, mitigate and ultimately prevent them from impacting you. ThreatQ is core to achieving this by centrally coordinating and ensuring consistency of available intelligence across all security tools in the environment.
The ThreatQ Open Exchange enables integrations with key security tooling within the business. These integrations may be leveraged to deploy a range of proactive and reactive countermeasures. These include:
- Creating and deploying rules and signatures to network detection and prevention technologies (i.e. NGFW) (See figure 3).
- Quarantining files on endpoints to prevent the spread of malware.
- Updating reputational scoring systems (such as McAfee TIE) to improve the automated and coordinated response to current or future threats.
- Coordinating security teams via ticketing systems and ThreatQ Investigation’s collaboration features.
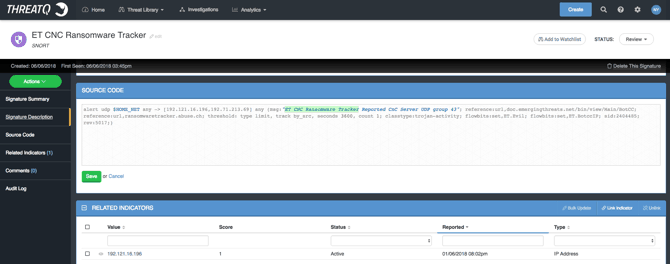
Figure 3 – Snort signature based on malicious IP address to detect CNC Ransomware connection
Step 4 – Staying Vigilant
Threat actor behaviors and tactics change on a regular basis. Many threat actors shift behaviors and attack techniques as existing methods become less effective (through detection and enforcement). MITRE are constantly streamlining and improving their knowledge base of data to handle this challenge. ThreatQ aligns with this approach by treating the ATT&CK data as a feed. This ensures that ThreatQ will automatically update when MITRE does, thus ensuring that you always have the latest information available to respond effectively.
Once you know of a risk from a threat actor, it is important to stay vigilant. This can be a challenging task in a landscape of increasing threats. There is no replacement for human knowledge and analysis when threat hunting, but we can certainly make it easier by providing current, detailed and accurate information to enable more informed judgements and quicker responses!

0 Comments