The butler didn’t do it, so who did?
POSTED BY LIZ BUSHIf you’re anything like me, then you’re going to love this cyber investigation challenge we’ve put together for you. You see, when I was a kid, I wanted to be a detective. Part of that was the influence of shows like Moonlighting, Magnum P.I. and Hill Street Blues but part of it was because I loved gathering clues to solve mysteries.
In college I worked as a criminal investigator. As part of an investigative team, I would assign tasks for a particular case, gather evidence, and determine a timeline of events in order present a complete picture of the incident.
In hindsight, I was laying the foundation for a career in cybersecurity. I love helping others find out “whodunit” and how to stop it. At ThreatQuotient, we have built a product that helps security operations teams investigate a suspicious event or incident and determine how to remediate it. ThreatQ Investigations is a cybersecurity situation room where teams collaborate and coordinate response. They can visualize and document an incident together, allowing them to take action based on evidence much more quickly and with greater confidence.
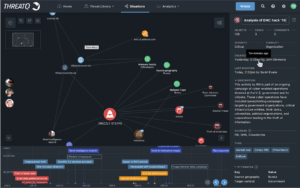
ThreatQ Investigations User Interface
Going back to the detective show reference, I compare ThreatQ Investigation to those detective shows where multiple detectives work a case, all following clues and then coming together to add the relevant information to the evidence board and creating a timeline of the events. Based on the evidence board and timeline, the head detective then assigns additional tasks for the detectives to pursue. As more information comes in, it is either thrown out if irrelevant or added to the board and timeline to complete the picture with the ultimate goal of finding out who did it. In cybersecurity, we take it one step further and not only want to find out who did it, but how to stop it or prevent it in the future.
Like most products, it helps to see it and be able to interact with it to understand how it works. To demonstrate ThreatQ Investigations, we have put together a hands-on challenge where you can see the platform at work and test your cybersecurity investigation skills. Maybe even win a prize while you’re at it!
Up to the challenge?
Sign up to access ThreatQ Investigations and put on your detective hat!

0 Comments