THREATQ INVESTIGATIONS
The industry’s first cybersecurity situation room for threat detection, investigation and response.
TAKE THE RIGHT ACTIONS, FASTER
The industry’s first cybersecurity situation room designed for collaborative threat analysis, shared understanding and coordinated response. ThreatQ Investigations embeds visualization and documentation in a shared environment for a greater understanding and focus throughout the analysis process.

Accelerate Understanding

Improve Collaboration

Coordinate Action
ThreatQ Investigations Product Brief
Learn how ThreatQ Investigations provides a unique window into the chaotic world of threats

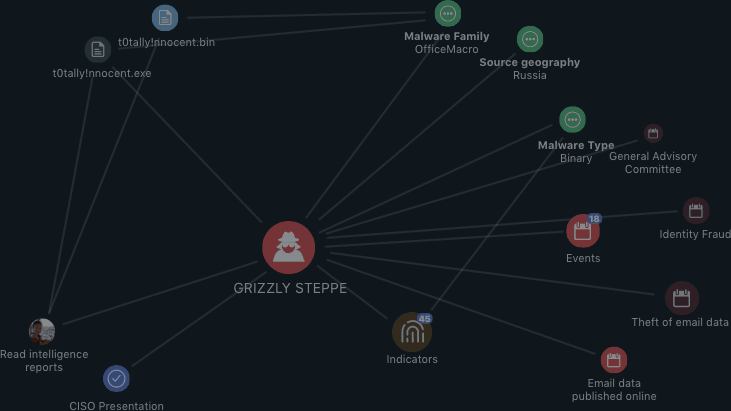
VISUALIZE DATA & RELATIONSHIPS
- Fuse together threat data, evidence and users
- Accelerate investigation, analysis and understanding of threats in order to update your defense posture proactively
- Drive down mean time to detect (MTTD) and mean time to respond (MTTR)
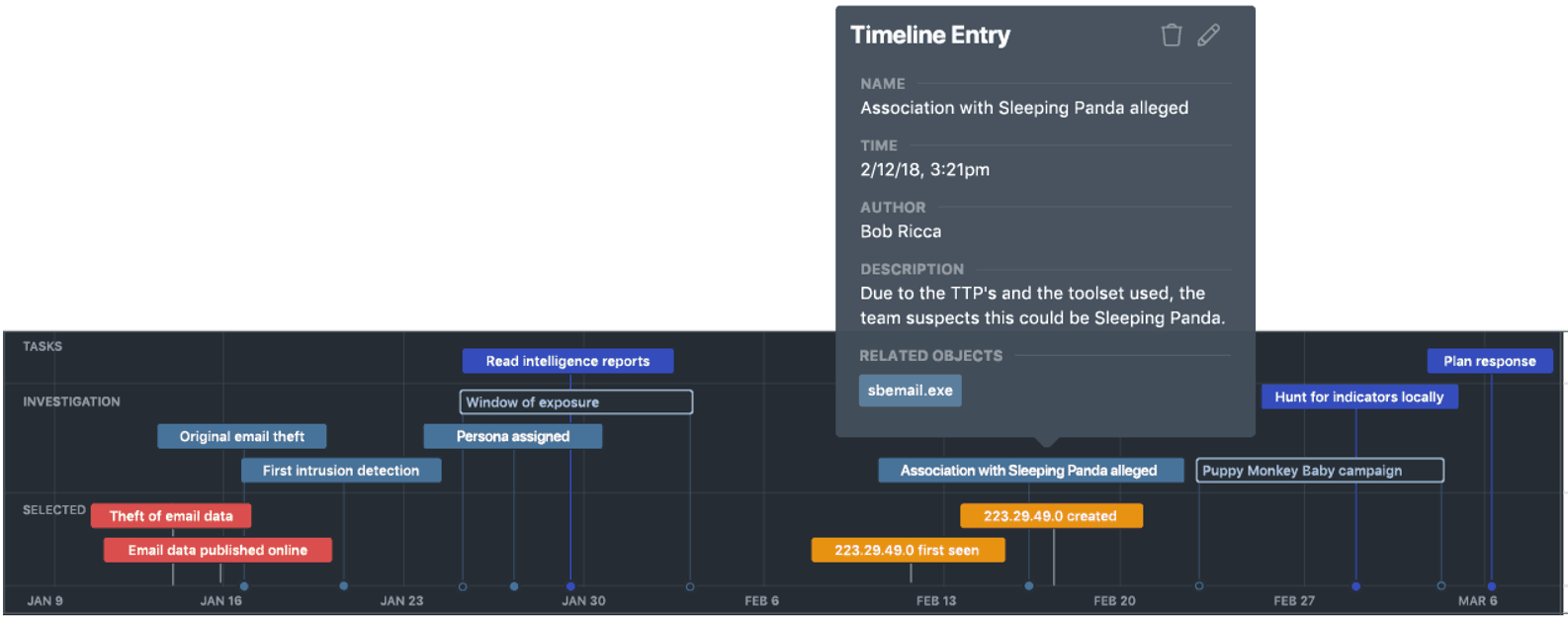
UNDERSTAND TIMELINES
- Build incident, adversary and campaign timelines
- See who was working on what and when
- Understand how the response unfolded
TAKE ACTION
- Bring order to the chaos of incident response and threat investigations
- See how the work of others impacts and extends on your own
- Incident handlers, malware researchers, SOC analysts and investigation leads gain more control, and are able to take the right steps at the right time