Spear Phishing Triage Using ThreatQ and TDR Orchestrator
Ed YoungAccording to Proofpoint’s 2021 State of the Phish Report, more than 80% of organizations fell victim to a phishing attack last year. Another report from PhishMe found that 91% of cyberattacks start with a phish, and the top reasons people are duped by phishing emails are curiosity (13.7%), fear (13.4%), and urgency (13.2%), followed by reward/recognition, social, entertainment, and opportunity.
Spear Phishing attacks are social engineering cyberattack methods that target specific individuals or groups with the goal of stealing sensitive information such as login credentials or infecting the targets’ device with malware. Concentrating on a more informed targeting method, attackers identify the individuals to target instead of a mass mail approach.
The attacks target specific individuals or organizations typically through malicious emails. Attackers will research their target, so the attack appears to be coming from a trusted source. Using a targeted campaign this information is used to invite the victim to click on a malicious link or attachment. After the victim clicks the link, the attacker can steal the needed credentials and enter the network undetected.
Ways to reduce the threat posed from human error include cyber security training to defend against the attack by teaching employees how to recognize a malicious link, attachment, or phishing campaign. Coupled with email security products, the right training can empower your teams to report on suspicious activity and can provide the strategy needed for protecting your attack surface.
Identifying and Prioritizing Threat Data
The ThreatQ Platform and product suite are built to empower teams to work more collaboratively and efficiently. The ThreatQ DataLinq Engine automatically correlates the data to expose the threats that need to be prioritized by filtering on events with a common email subject, identical attachments or maybe a common target user group. Capturing and storing data related to sightings, campaigns, investigations and resolutions, ThreatQ provides a continuous source of information to be used for learning and improvement to your security process.
ThreatQ customers benefit from the unique capabilities provided through the information stored in the Threat Library with the ability to identify trends and campaigns using historical data that is continually updated with new threat intelligence.
Focusing on tactical data that can link spear phishing events to a target user group, an indicator that is linked to the same malware family or an indicator that is linked to the same attack pattern enables security teams to identify trends. Using ThreatQ’s Smart Collections and custom scoring enables teams to prioritize and respond to threats quickly, reducing dwell time.
Data-driven workflows based on the trend identified can be used for simple automation or more complex orchestration with the ability to initiate a process based on criteria that is important to you.
Automating Your Spear Phish Triage Using the Best of Breed XDR solution
ThreatQ and TDR Orchestrator can automate the repetitive process of analyzing spear phishing emails that has consumed valuable analyst time that is better applied elsewhere. ThreatQ’s extensive integration capabilities, combined with TDR Orchestrator, greatly reduces the time, effort, and cost when triaging an incident.
ThreatQuotient customers populate and update their data by ingesting threat intelligence information from internal or external sources. The data is normalized and correlated to be available from a central location, the Threat Library. When a suspected spear phish attack is detected the email and any attachments contained with it can be ingested through a bi-directional integrations, direct API access or manual import.
Using the data already in the Threat Library as well as other integrated solutions within your security stack will reduce the time and manual effort that is needed to triage the event. Whether it is automatically enriching the data through normalized threat intelligence contained in the Threat Library or sending the attachment to a sandbox for analysis, the automated process will save time and provide focus to a prioritized set of data for remediation.
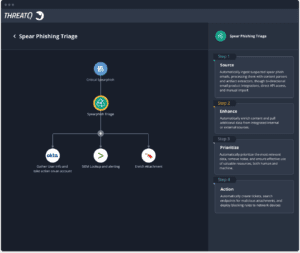
Smart Collections and Threat Library searches provide additional clarity based on what type of indicators are contained in the spear phish event and how frequently it has occurred in your environment. Are there indicators linked to a specific malware family? Does the event target a specific user group? Your Threat Library search has results of events that target members of the company’s Human Resources Department and has increased over the last 48 hours. Attackers are trying to obtain sensitive information about our employees.
We have identified an event that is trending, and we know the targets. This is the priority for my team to focus on and remediation is needed. ThreatQ TDR Orchestrator can automate the response action to work within the security process already established and allow teams to update their process based on what is learned.
A task or ticket can be generated to open an investigation so a Threat Analyst can do a deeper dive into the event. A search can be performed against your EDR system to gather data about the infected file from the attachment and how far it has propagated, or you could suspend the user accounts of the team members who were targeted. The automation workflows can be simple or a more comprehensive XDR solution and allow security teams to easily build repeatable remediation steps.
The workflows can be simple or complex but the creation process does not need to be. The ThreatQ Platform and TDR Orchestrator can reduce the number of manual clicks needed to drill down to the most important data. The context that is contained in the Threat Library provides the lessons learned that can be drawn upon to improve security operations. ThreatQ’s data-driven workflows identify the tactical or strategic meaning of the spear phish campaign, allowing teams to anticipate the possibility of a threat and be proactive in defending against it.
To see the ThreatQ Platform and TDR Orchestrator in action, please visit: https://www.threatq.com/threatq-online-experience-registration/

0 Comments