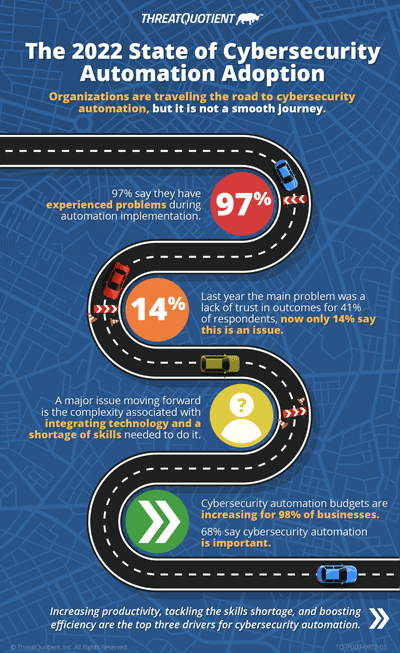
Organizations are traveling the road to cybersecurity automation, but it is not a smooth journey
Marc SolomonOur latest industry research – ‘The 2022 State of Cybersecurity Automation Adoption’ – which we have undertaken for the second year running and expanded into other regions including the UK, USA and Australia, shows strong signs that cybersecurity automation adoption is advancing, but 97% of respondents say they have experienced problems during implementation. These problems range from technology issues and lack of budget to skills shortage and gaining management understanding/buy-in. However, where last year (and I realize that we only did this in the UK) the main problem was a lack of trust in outcomes for 41% of respondents, now only 17% collectively say this is an issue. This indicates that organizations have become more confident in automation itself, despite struggling with the more practical aspects of its implementation and ongoing maintenance.
This also correlates with last year’s figures showing that while 37% had already automated key cybersecurity processes, 45% were planning to do so. Now that far more organizations have implemented automation it is likely that challenges have moved from theoretical trust-based concerns to practical issues like the complexity of the technology and staffing people with the skills to address it.
Worker well-being forms part of ROI for automation
As the skills shortage and employee churn continue to bite, our research shows that businesses are now seeking ROI of cybersecurity automation in terms of both hard metrics and soft metrics around employee well-being.
A recent SANS CTI survey found that assessing ROI was one of the chief challenges when building the case for automation. We asked our survey cohort of 750 senior cybersecurity professionals what primary methods they used to monitor ROI.
42% of respondents said they analyze how well they are managing resources such as staff, efficiency, and budget, while 39% said they look at how well they are managing the team in terms of employee satisfaction and retention. Interestingly, hard metrics on how well the job is actually being done, in terms of mean time to detection and mean time to resolution, were only the third most important factor (chosen by 37%).
Using automation to do the heavy lifting and cut through the noise is vital to helping cybersecurity teams thrive under pressure. Retaining employees by making their work more rewarding avoids excessive recruitment costs and the issues that arise when corporate knowledge walks out of the door with dissatisfied or distressed employees.
Key drivers for cybersecurity automation
As we continue through uncertain economic waters, the three main reasons for organizations to adopt more cybersecurity automation are to improve efficiency (29%); to protect themselves against ever-growing cyberattacks (29%) and to comply with escalating compliance and regulation requirements (29%). That said, automation is also seen as an important tool for addressing the skills shortage and making teams more efficient. These issues will become increasingly important in an uncertain business environment, meaning automation providers must make sure their products deliver genuine benefits. The advantages of utilizing tools such as no-code and solutions that simplify the complexity introduced by traditional automation tools while allowing teams to focus on higher value cybersecurity activities will be important messages to communicate to customers.
Other key findings in our research include:
- Cybersecurity automation budgets are increasing for 98% of businesses
- 68% say cybersecurity automation is important
- The top cybersecurity processes/use cases automated by organizations overall are threat intelligence management and incident response with 27% each
The above provides a sneak preview of our findings; the full research report will be released at the beginning of November. Do check it out, there are some fascinating insights around how senior cybersecurity professionals are approaching the challenge of securing the extended enterprise in an intense and complex threat and operational environment. We explore common use cases, typical challenges, barriers to adoption, cybersecurity maturity and more.
To receive a copy of our research the moment it is published, sign up below and we will notify you.

0 Comments