Using Threat Intelligence to Defend Against 0day Vulnerabilities
POSTED BY YANN LEBORGNELast month, a new 0day (CVE 2017-0199) was reported in the news. It was publicized in conjunction with a well-known malware which was dormant for a good number of months. As it is not common to have 0days reported in cybercrime operations (they are much more famous in the targeted attack world) I decided to apply a threat intelligence analysis to this specific problem.
As a security professional, I am always amused by the reaction to 0day announcements. On one hand, there is always a strong interest in technically understanding the vulnerability and how it is exploited. On the other hand, the market always tries to use this opportunity to position “The New Magic Solution” to fix the problem.
To be clear, there is no magic solution to 0days, nor to 100% security. It is and has always been a combination of good practices, efficient and robust processes, HUMANS, and some tools to support HUMANS.
The objective of this post is to investigate how the bad guys are using 0day vulnerabilities and what a threat intelligence program can bring to a security team to help improve vulnerability management.
Part I: Linking Campaigns
Let’s start with some incidents that were reported in March and April of this year. As a threat intelligence feed provider, inThreat has been pivotal to my analysis. Special credit to David Bizeul who authorized me to use these data in this blog.
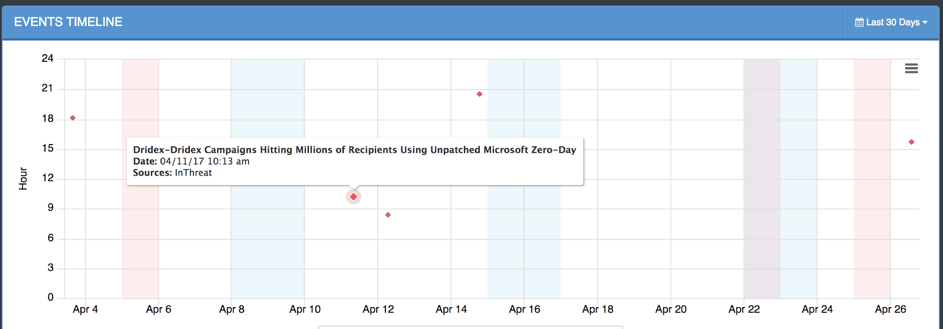
Figure 1 : Timeline of incidents
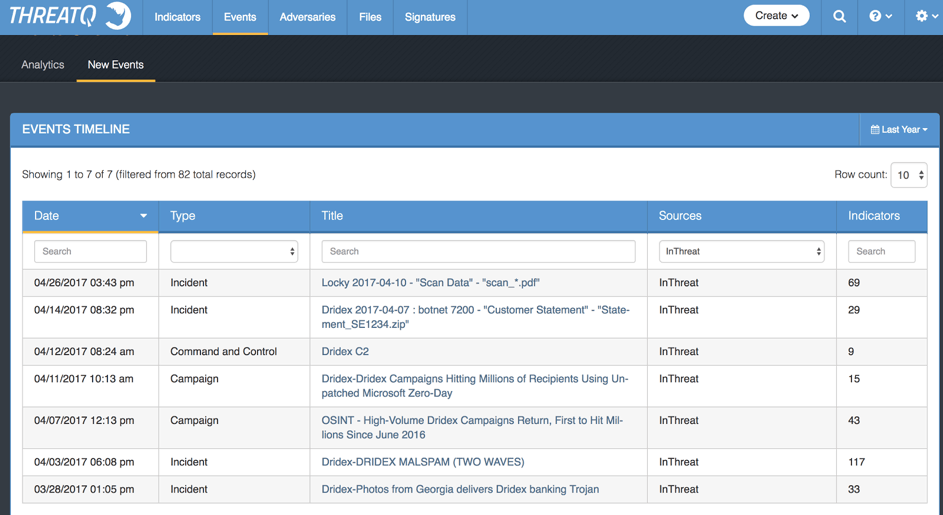
Figure 2 : Events by category
As you can see in Figure 1, the first incident was reported at end of March. It looks like an isolated attack, both from a geographical and a volume perspective. Then, in Figure 2, you can see the next big waves reported as an incident and a full campaign on April 3rd and 7th. I will come back to them, but this is the wave that used the double-zipped, PDF-embedded technique.
On April 11th, the first report on the use of the Microsoft 0day is made by inThreat. The following events are the aftermath of the campaign that were reported as an incident within the infrastructure.
Let’s start with the oldest information we have here, and focus on the IP addresses that were reported [Figure 3].
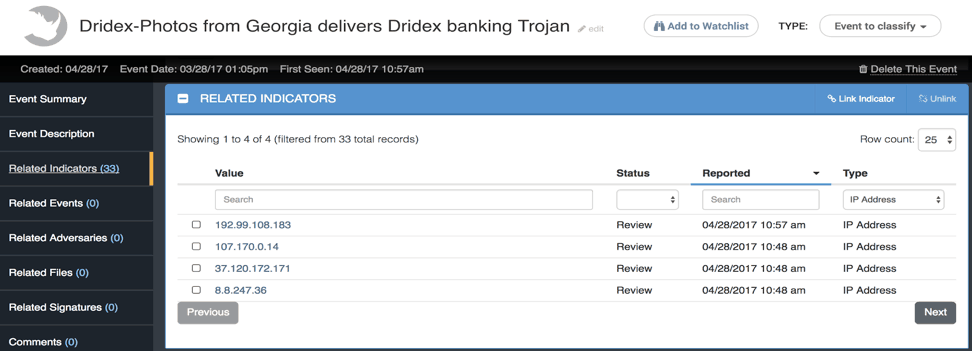
Figure 3 : Indicator of compromise for first reported incident
As shown in Figure 4, with the ThreatQ threat intelligence platform I have the ability to run enrichment operations on indicators such as IP addresses. Below is information about 8.8.247.26 from VirusTotal which is integrated into the ThreatQ threat intelligence platform:
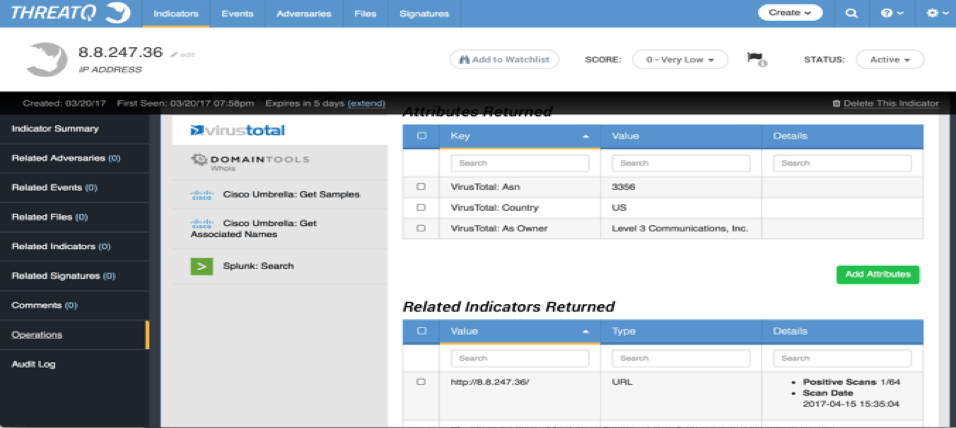
Figure 4: VirusTotal enrichment of C2 IP address
The IP is located in the US and part of Level 3, but we can see in Figure 5 some positive matches on VirusTotal as soon as March 29th, the day after the report by our source:
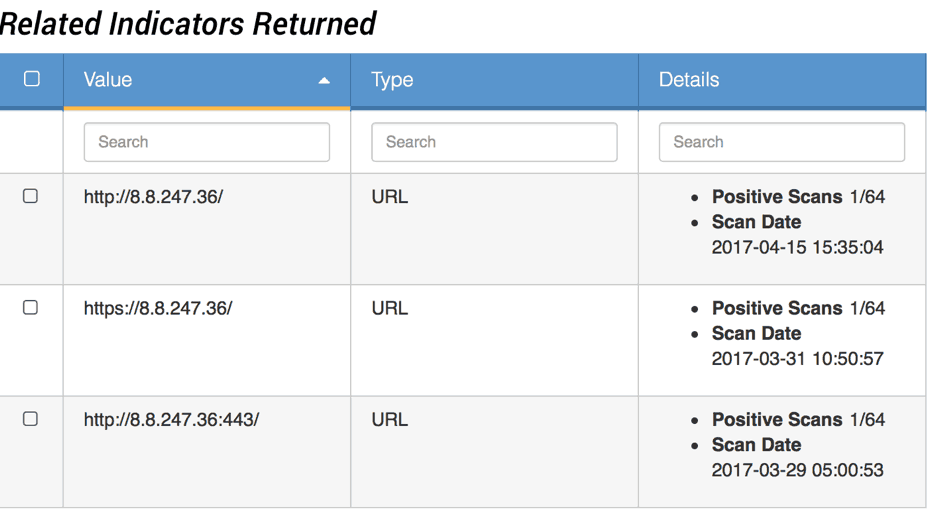
Figure 5: VirusTotal enrichment of C2 IP address
Based on this investigation, the indicator is interesting to me. The source is trusted, part of a big block on the Internet, and positive detections are reported after my initial report.
An advantage of having a place to manage your threat intelligence, such as ThreatQ, is that you can cross-validate information. This particular IP is also referenced in another incident that occurred in early April.
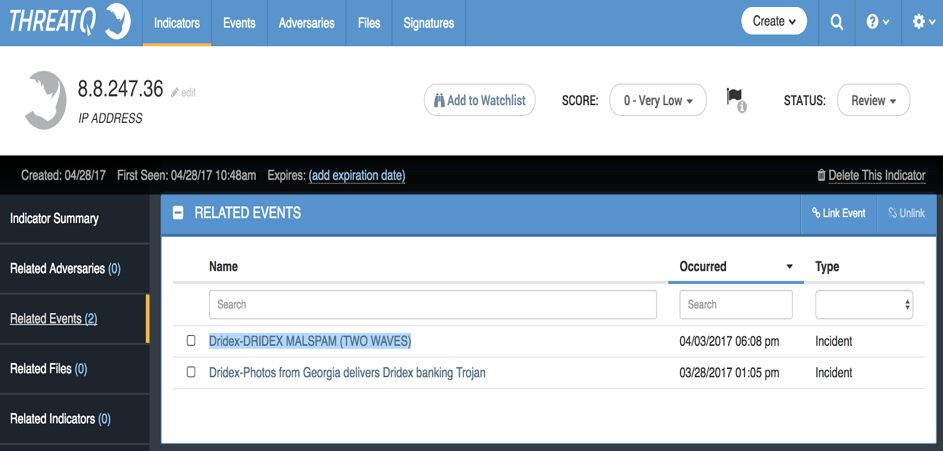
Figure 6 : Related events to C2 IP address
Figure 6 depicts the first two waves of a high volume Dridex distribution that have targeted Australia and the UK. These attacks are also very well detailed in a proofpoint report.
This campaign is using double-zipped executables or VB scripts that are distributed via spearphishing with themes around “Bookings.” The attachment names contain Documentation (random digit) or P(random digit).JPG.zip.
Let’s look at what we have in the ThreatQ threat intelligence platform about these incidents reported by inThreat [Figure 7]:
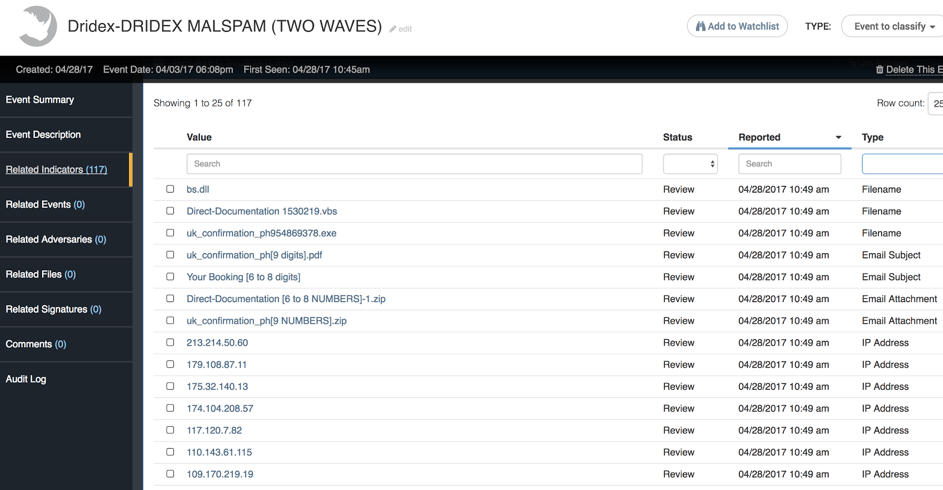
Figure 7 : Indicator view for main campaign report
We can find the expected email subject or attachment names as indicators, but my purpose is to investigate the infrastructure aspect, so let’s focus on the IPs. In Figure 8 we see an example of what a threat intel analyst would consider to be a very interesting indicator: 23.95.23.219
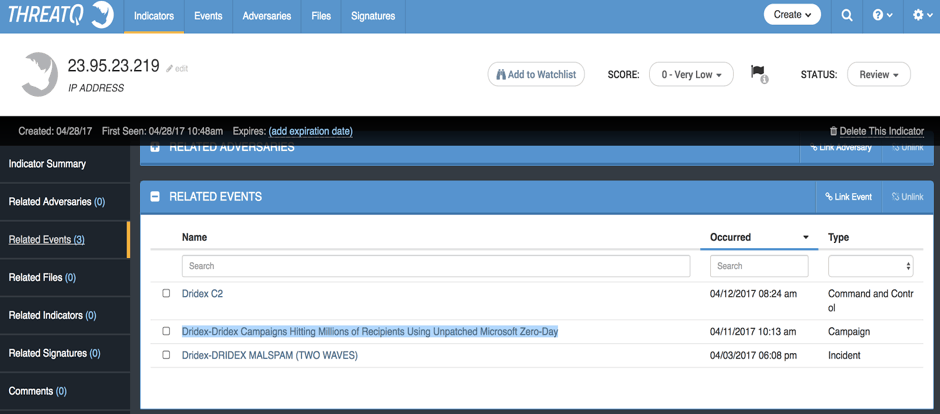
Figure 8 : Key indicator relating campaign to 0Day report
This particular IP is also part of the campaign that was carrying the 0day vulnerability.
This IP is the link between the first two waves that were carrying a “standard” dropper for Dridex and the following campaign where the bad actors have changed their weaponization to use this Microsoft 0day.
The take-away from this part of the analysis is that the actors have changed the weaponization to include this 0day. In part II we will discuss how the actors change the delivery method but keep the command and control (C2) infrastructure.
Part II: The Delivery
Let’s have a quick look at this particular incident embedding the 0day. Of course we can see in Figure 9 below the infrastructure part of the indicators, with the IP address that has been carried over the different campaign waves. But I have also retrieved from other sources some spear phishing emails that I have imported to ThreatQ for the purpose of this demonstration.
The spear phishing email is included here as a new event, “Scan Data”.
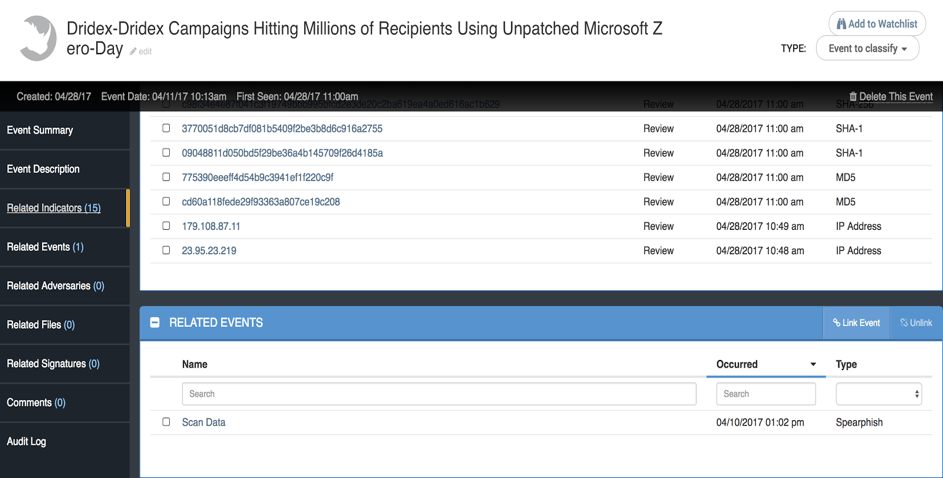
Figure 9 : Detailed view of 0day weapon campaign
As you can see, the delivery method has changed a bit from the previous waves in early April. We still see the use of random digits in the attachment name and the “from” field (hidden here), but it is now using a different prefix.
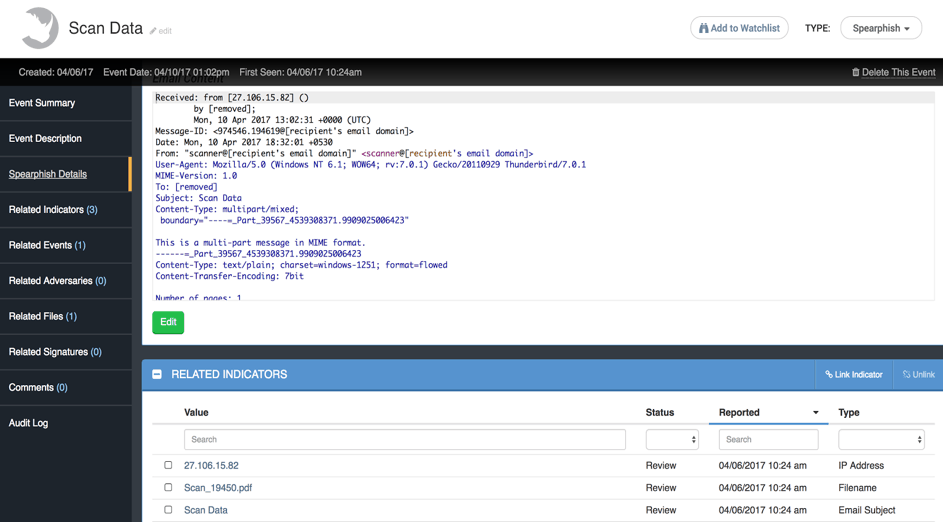
Figure 10 : Spear phishing event of the 0day delivery
My ThreatQ threat intelligence platform is integrated with sandboxing technology from Cisco so I have uploaded the PDF document for detonation [Figure 10].
As expected, new indicators are appearing. We have new domains registered, but also we can see the weaponization details. In fact, the PDF document embeds the Word document that contains the 0day exploit.
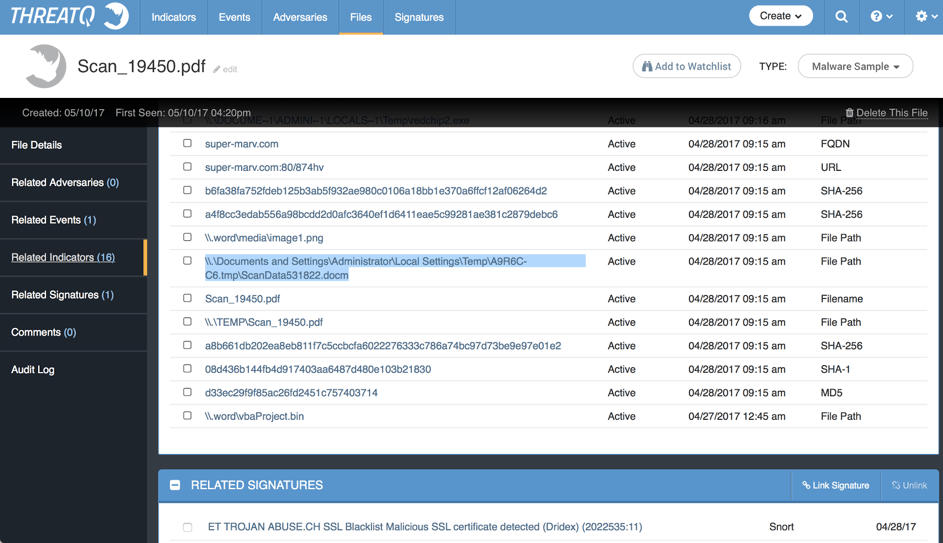
Figure 11 : Technical report from ThreatGrid on the PDF file
Finally, as you can see from Figure 11, I have linked a pre-existing Emerging Threats (ET) signature to the previous file. The C2 infrastructure used a certificate that could be detected using some previously available ET rules.
Conclusion:
Of course this is a post campaign analysis, and it is always easier to find something when you know what you are looking for. But what we can learn from this is that while bad guys can change things easily, including the use of a 0day for vulnerability management, it is very hard and expensive for them to change everything (remember the pyramid of pain).
The process of threat intelligence analysis is to collect and organize information about the actors that are targeting us, finding the tactics they change, but also what they re-use. This allows us to build defenses to protect existing vectors, but also deploy the appropriate countermeasures to anticipate a certain amount of change.
There will always be a way for the bad actors to infiltrate our information systems. But collecting information both from external AND internal sources, enriching this information and making it actionable can certainly raise the bar for adversaries and make your jobs easier.

0 Comments