One of These Things Is Not Like the Other - Defending Against Homograph Attacks
POSTED BY JULIAN DEFRONZORecently there has been an increase in homograph attacks. These attacks take advantage of certain Unicode characters that look very similar to certain ASCII characters and use a similar-looking name to a more established domain to fool a user. For example, аpple.com is a proof of concept domain where the Latin “a” is replaced with the Cyrillic “a”. Most recently we saw a malware sinkhole targeting WhatsApp users: шһатѕарр.com. At a quick glance, the domain appears normal but when looking closer, we notice that Latin characters have been replaced with Cyrillic characters.
While most modern browsers have protections against homograph attacks, the use of Punycode makes it possible to register domains with foreign characters using only ASCII characters in an alternative format (xn--pple-43d.com = аpple.com). This bypasses many browser protections if every character is replaced with one from a foreign language (xn--80aa2cah8a7f73b.com = шһатѕарр.com. When a user navigates to the Punycode domain, the browser “translates” it to the Unicode representation and makes it extremely difficult for unaware users to distinguish from the legitimate domain [Figure 1].
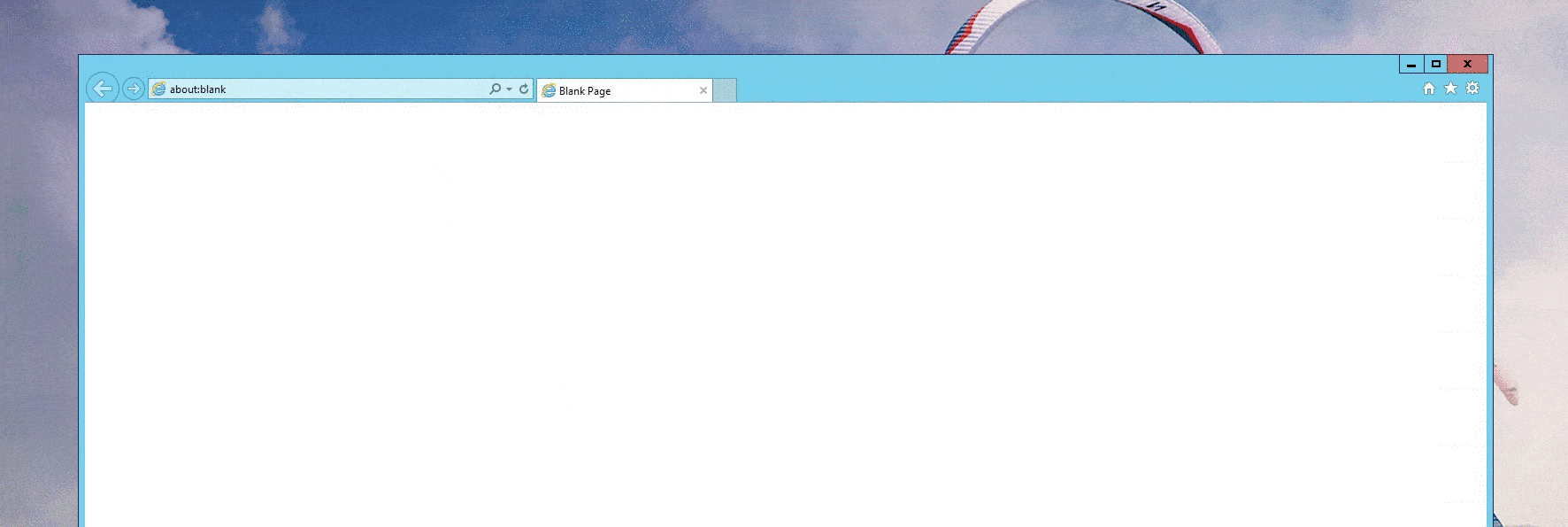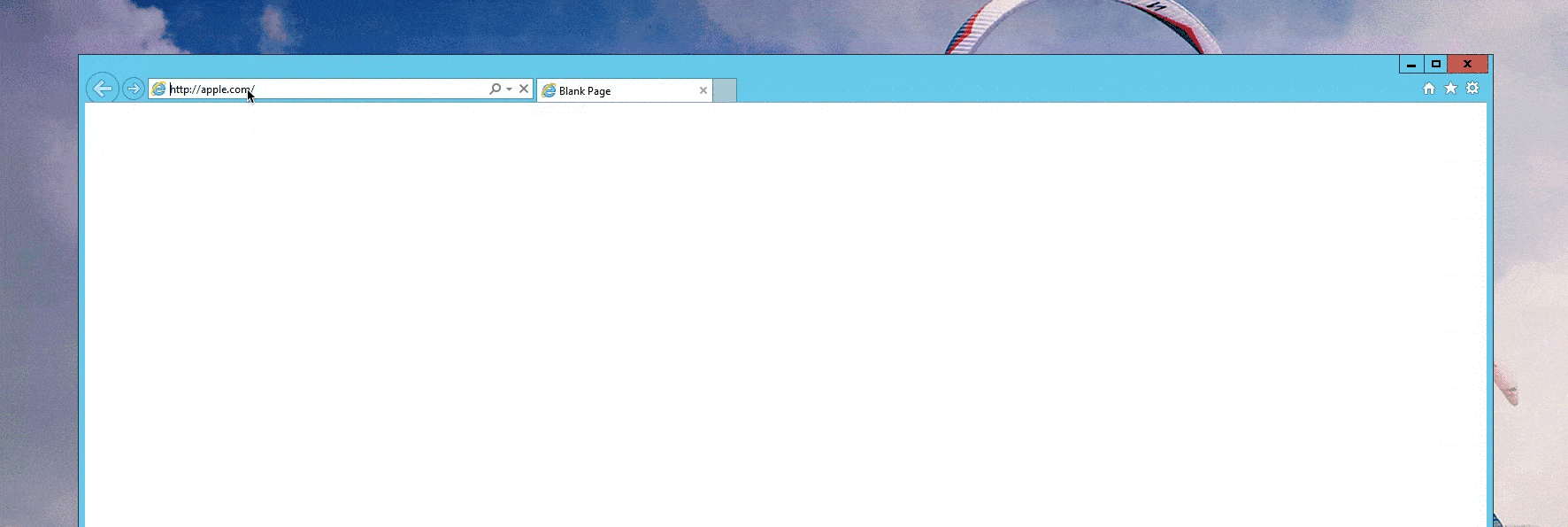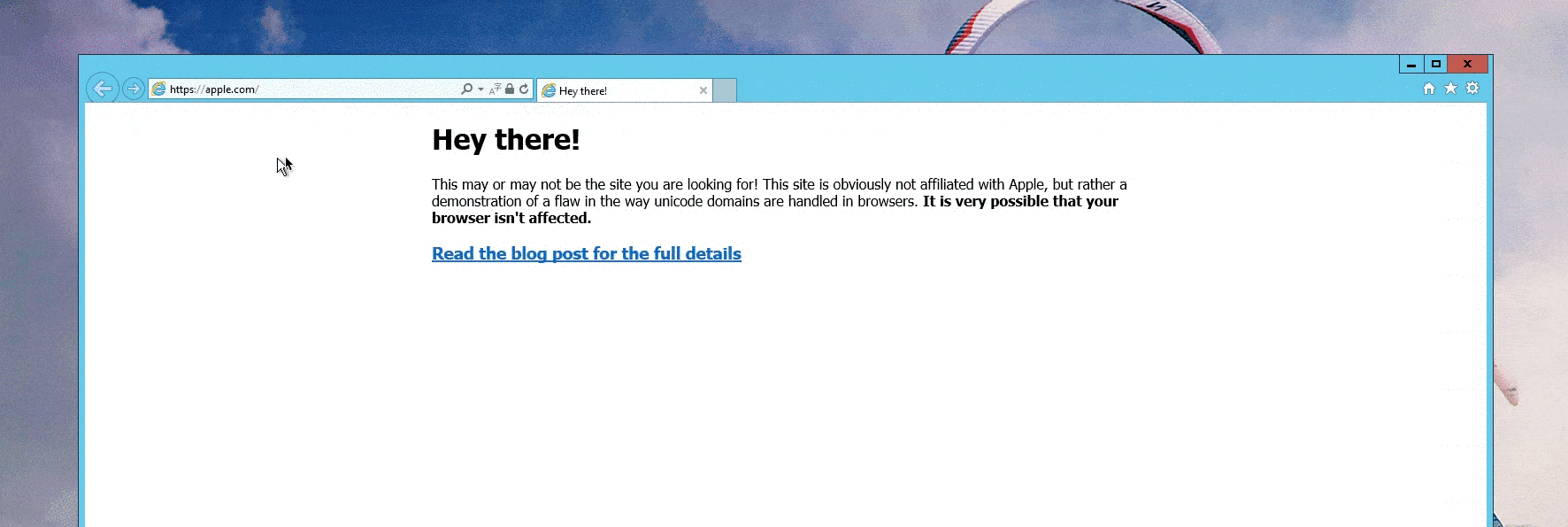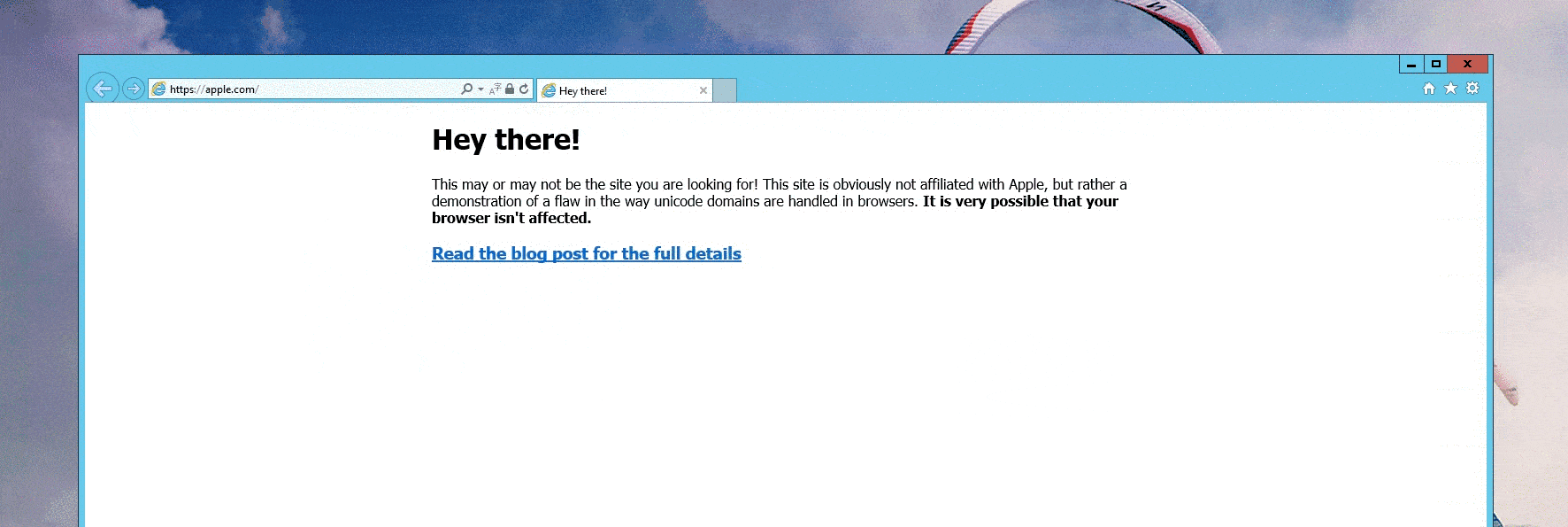
Figure 1: Proof-of-Concept Homograph Attack
The ThreatQ platform is flexible enough to support curation of these type of domains. Using the WhatsApp campaign from above, we can demonstrate how to add the Punycode representation of шһатѕарр.com to our Threat Library [Figure 2].
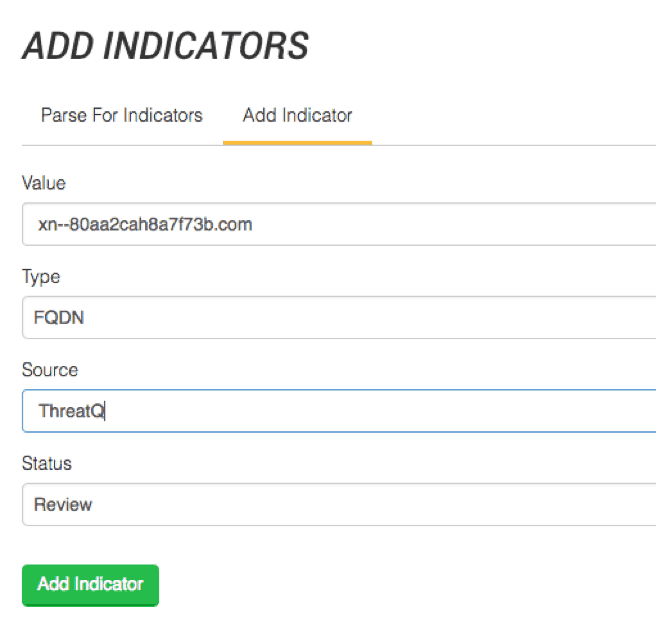
Figure 2: Adding Punycode Representation of шһатѕарр.com
From there we can create an Operation that leverages Python’s native support to decode the Internationalized Domain Names in Applications (IDNA) specification and add relevant attributes to the indicator [Figure 3 and Figure 4].
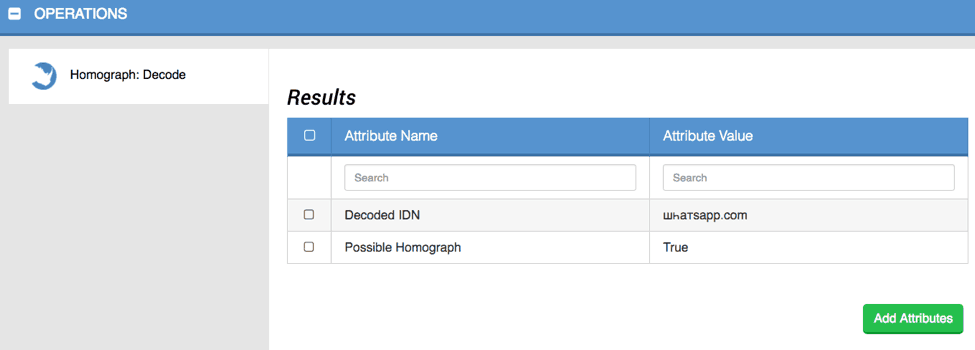
Figure 3: Decoding Punycode IDNA
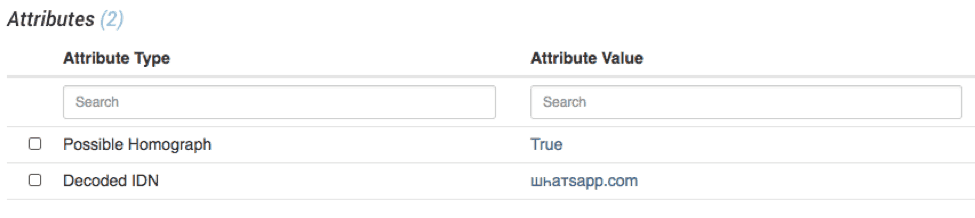
Figure 4: Added Attributes
This operation also leverages the confusable homoglyphs Python library to determine if the decoded domain includes confusable Unicode characters and could be considered a possible Homograph attack domain.
With that information we can use other Operations to perform routine enrichment and analysis activities to get a better understanding of the domain in question, see if it’s part of an ongoing campaign, and provide additional context for scoring. We can also leverage Exports to pay special attention to Possible Homograph domains and automatically add them to the DNS blacklist or proxy block list.
With ThreatQ and just a few simple steps you can more effectively detect and defend against the surge in homograph attacks.

0 Comments