Using ThreatQuotient to Discover and Prevent POS Malware
POSTED BY MIKE CLARKEddie Bauer is just the latest victim in a spate of malware attacks on Point of Sale (POS) devices which are proving to be high value targets for cyber criminals. These devices contain very valuable information in the way of credit card information and are difficult to secure due to their ubiquitous nature. They often run on old operating systems, are difficult to patch, and use outdated software. If an intruder is able to gain access, they can run their malicious payload undetected for long stretches of time.
Many retailers do not include Anti-Virus (AV) or other security software on POS devices. And even if they do, relying on AV alone is not enough to counter the threat of POS malware.
Threat intelligence can strengthen a retailer’s ability to detect the presence of POS malware operating in the network. But making this intelligence actionable is a dilemma that security analysts can struggle with.
To bridge the gap between threat intelligence information and operational security devices, the ThreatQ, threat intelligence platform can be used. The following end-to-end example using a popular malware intelligence service shows how to do this.
Threat Intelligence
VirusTotal offers a commercial subscription based service called VirusTotal Malware Intelligence Service (VTMIS) which provides a wealth of information about malware. In particular, it allows users to upload YARA rules which are compared against community-uploaded suspicious malware samples. If the YARA rule comes up with a match, it notifies you, provides the standard VirusTotal information about the sample, and allows you to download the sample for further investigation.

Virus Total Intelligence notification page
YARA rules can be thought of as binary and string matching mechanisms that allow you to flag files as possibly malicious. There are a number of community YARA repositories containing rules, for example, which have been developed to identify possible POS malware. By putting these in VTMIS (being mindful of subscription limitations), we are able to see new samples which are likely malware. VirusTotal also does behavioral analysis on the samples which can provide further information, such as command and control (C2) infrastructure including IP address and/or FQDNs. These are extremely valuable indicators of compromise (IOCs).
ThreatQ Threat Intelligence Platform
So how do you get this valuable information from VirusTotal Intelligence to the security devices? ThreatQ provides a robust API which easily allows integrations to a wide range of security devices. We currently provide a SDK which simplifies the process for use with Python. In a short amount of time, you can create a script to pull down samples matched by your YARA rules from VirusTotal, create IOCs in ThreatQ, and then automatically deploy these to your sensor grid.
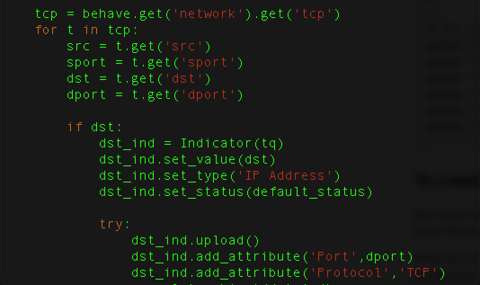
Example usage of ThreatQ SDK for Python
In the screen shot above, you can see an IP address being used by the POS sample and added to ThreatQ. An attribute, which in ThreatQ is an additional piece of information, is also added to include the port and protocol. We can repeat this effort for process and filesystem information as well. Using the Python SDK, the script will integrate with the ThreatQ UI allowing for simple management.

The custom script can be controlled through the ThreatQ UI
In addition to ingesting the relevant indicators to ThreatQ, the malware sample itself can be downloaded from VTMIS and stored in ThreatQ – compressed and password-protected – to prevent accidental execution. As you can see below, the stored malware sample is related to all of the indicators uploaded.


An uploaded malware sample in ThreatQ with related indicators
In addition to downloading the malware sample and creating indicators, you can also create an event which will hold import metadata. An event in ThreatQ is any noteworthy occurrence defined by the organization – it is not limited to only incidents or only cyber efforts. In the event, you can also selectively limit what information is included. For instance, if your team is leveraging McAfee as your AV vendor you would focus on that information and how McAfee labeled it. Using an event will also allow for keeping a timeline of samples which in turn can offer interesting and graphing capabilities down the road.

An Event in ThreatQ for the newly discovered malware
As can be seen in the screenshot above, associated indicators and files are also linked from the event. When configuring the Connector, you have the ability to specify AV engines that you are interested in. For this example, McAfee is selected. ThreatQ will automatically make an attribute specifying whether or not McAfee detected the threat. This is very helpful in answering the age old question, “Would we detect this?”
Operational
Now that all this data is inside of ThreatQ, you can start using it in your security infrastructure and making it actionable. In this example, the information is sent to a Splunk SIEM for correlation against logs. ThreatQ supports exports in nearly any format and to a large number of security products. For Splunk specifically, we offer an app which integrates into the Splunk UI.
Once installed, the ThreatQ Splunk app will automatically pull down the latest indicators from a ThreatQ instance. Using the Common Information Model, the app can then look for any correlations in the Splunk data.

The ThreatQ App Dashboard in Splunk
Conclusion
In this post, we covered an end-to-end example of using ThreatQ to retrieve intelligence, manage it, and operationalize it by sending it to a Splunk SIEM where POS malware infections can be discovered. This is just one scenario; the ThreatQ platform is extremely flexible allowing integration with numerous data sources and security devices, while providing a place for analysts to research and track security threats. But that’s a topic for another blog.

0 Comments