How to Leverage the ThreatQ Threat Library Using Carbon Black
POSTED BY KEVIN LIBBYYou’ve got mail.
This is not only a title to a movie that I’d prefer not to ever watch again. It’s also the tip of the spear of what could be a greater campaign by an adversary targeting your organization.
It’s been stated that as much of 91% of data breaches come from phishing attacks*. In fact, The Anti-Phishing Working Group (APWG) shared that more phishing attacks were observed during the first quarter of last year than in any other quarter since they began tracking**. More recently, Cisco reported that Spam accounts for nearly two-thirds of total email volume, with much of it potentially malicious***.
That’s a lot of potential malware. How is your organization handling this onslaught?
The ThreatQ threat intelligence platform is all about helping you get the most value from threat intelligence and streamlining threat operations. One example is how ThreatQ provides the ability to automatically parse email content. This allows users to accelerate analysis and decrease response time to malicious phishing events. Once those spear phishing related indicators are stored in ThreatQ’s Threat Library, analysts can rest assured that they’ve been made available to the network and host controls automatically, if desired.
Using the Exports section of ThreatQ, analysts are able to make data available to the team or tool that needs to consume the critical threat data using the Carbon Black integration.
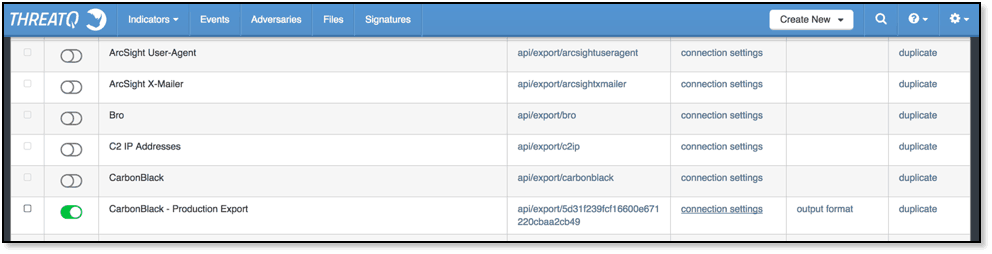
Figure 1 ThreatQ Exports
In my example, I’ve setup an Export to enable Active IP Addresses, FQDNs, and MD5s available for Carbon Black in a format that it expects (JSON and certain required entries which are referenced here —-> https://developer.carbonblack.com/reference/enterprise-response/5.1/threat-intelligence-feeds/).
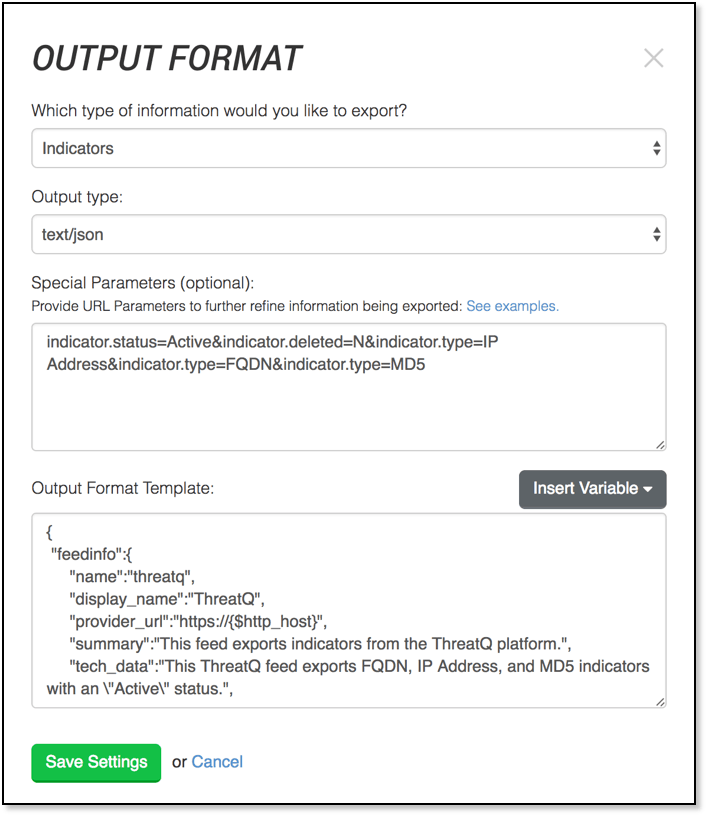
Figure 2 Carbon Black Export Output Format within the ThreatQ User Interface
The full output format is available from support@threatq.com anytime.
Once logged into the Carbon Black console, you are able to see the ThreatQ feed. This tells me that Carbon Black is now able to leverage the data curated within ThreatQ’s Threat Library.
In fact, should they wish to view more context around any indicator, they’re able to look directly back into
ThreatQ by clicking on the link provided in each indicator report.
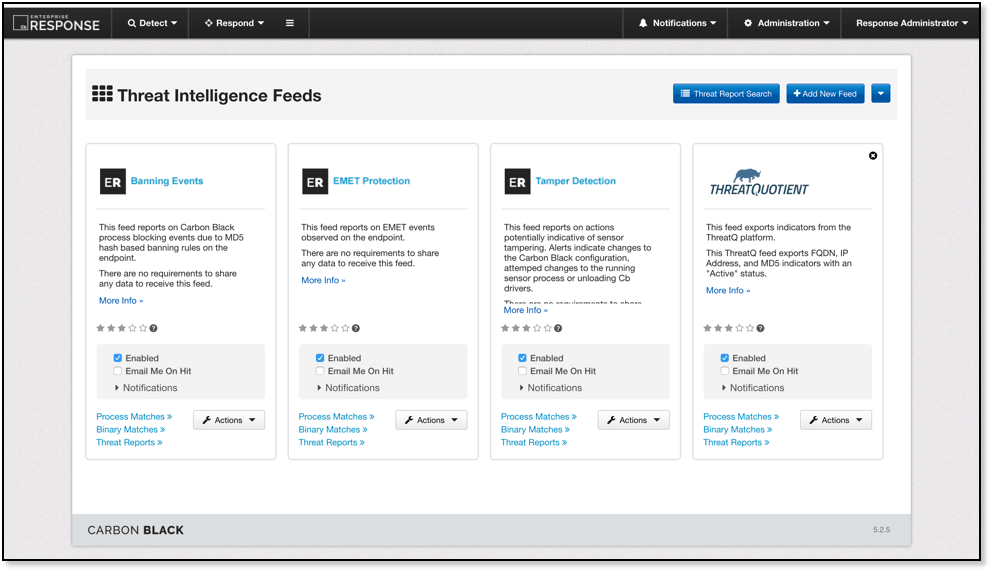
Figure 3 Carbon Black Console
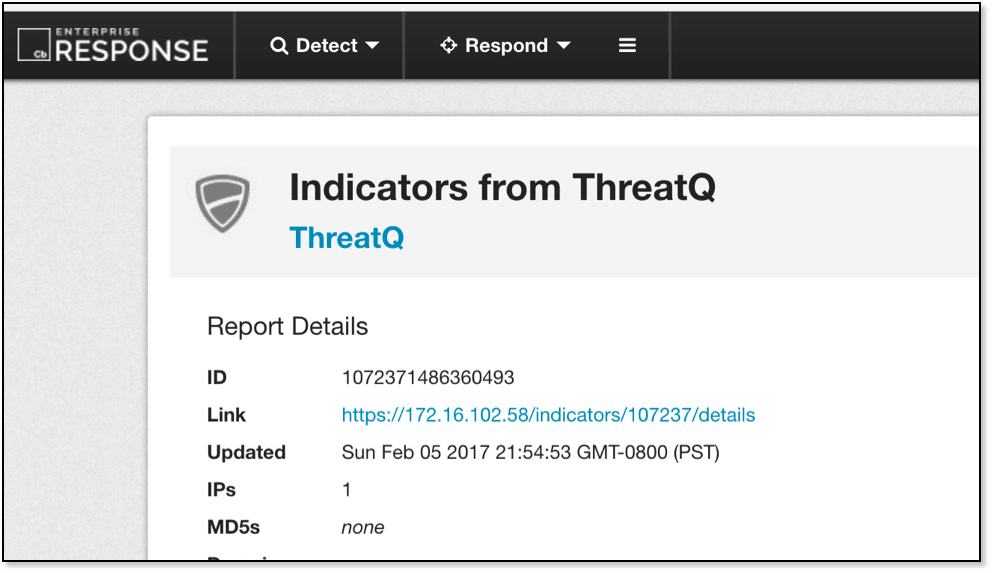
Figure 4 Indicator sourced from ThreatQ within the Carbon Black Console
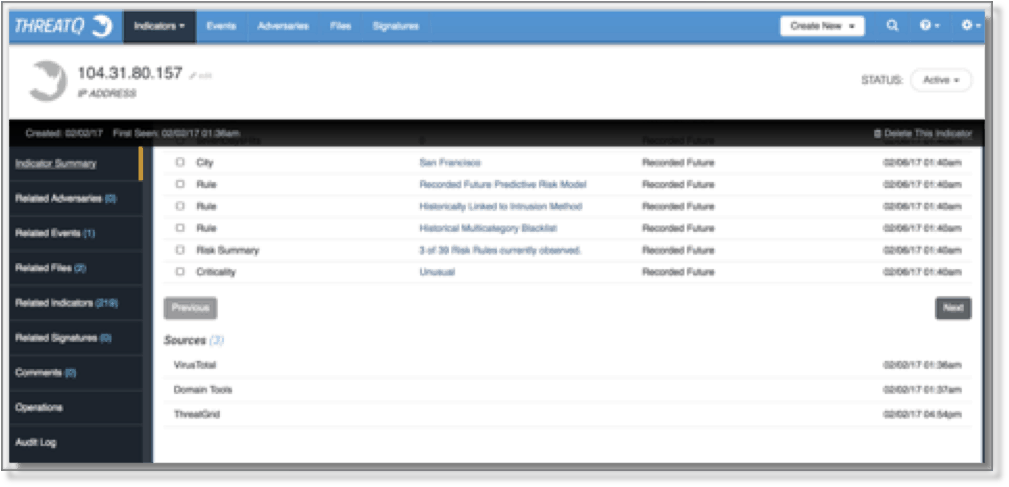
Figure 5 Indicator Summary within the ThreatQ threat intelligence platform User Interface
Would your organization benefit from viewing instant relevant contextual information around indicators they’re investigating?
Sources:
* https://digitalguardian.com/blog/social-engineering-attacks-common-techniques-how-prevent-attack
** https://www.scmagazine.com/apwg-report-phishing-surges-by-250-percent-in-q1-2016/article/528186/
*** Cisco Annual Cybersecurity Report – 2017

0 Comments