How to Use ThreatQ to Defend Against Ransomware
POSTED BY MIKE CLARKRansomware is still a major money maker for cyber criminals and victims are all over the board, ranging from individuals to major corporations. The attack isn’t complex and revolves around a very simple concept – encrypt the victim’s files and hold the files hostage until the victim pays a ransom in order to decrypt them. This forces the victim to really put a price on their data – family albums, historical tax files, databases of customer contact information, or worse, customer credit cards or health records. Backing-up your data in a secure remote location allows you to quickly recover from an attack and, of course, is a much better strategy than trusting the attacker to decrypt the files after payment. But blocking ransomware from ever reaching your valuable data is the ultimate win. In this post, we will show how you can use ThreatQ’s Threat Library to help defend against ransomware.
In order to defend against ransomware, we need to know where its weaknesses are. Luckily, most ransomware families work pretty much the same way: they execute on the target, encrypt the data, communicate with a C2 server and notify the user of their predicament. Those are the points we want to look into to see how we can dismantle this threat. To do this, we will map these to the Intrusion Kill Chain [Figure 1].
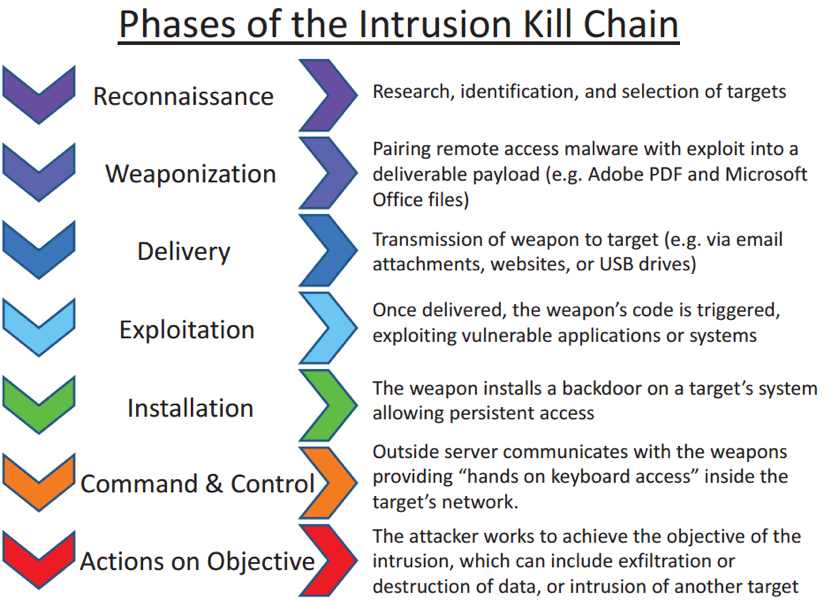
Figure 1.1 – LMCO’s Kill Chain
We will jump immediately to the Delivery step of the kill chain, since the first two phases focus on situational understanding and profiling the attacker over time. The Delivery stage is where we start to gain an understanding of the tactics, techniques and procedures (TTPs) that will allow us to detect and thwart the attack. Ransomware is delivered in a variety of ways: including exploit kits and spear phishing campaigns. Often, the ransomware payload is one of many delivered through these attack vectors. Stopping the ransomware at the Delivery stage of the Intrusion Kill Chain is an ideal way of preventing the threat.
Exploit Kits (EKs)
Exploit kits are a common vector to deliver ransomware. The user visits a site, an exploit runs, then the malicious payload is delivered. There are a number of FREE resources available which the ThreatQ threat intelligence platform supports to stop the threat at this point.
- Malware Domain List ( https://www.malwaredomainlist.com/ )
- DNS-BH ( http://www.malwaredomains.com/ )
- Ransomware Tracker by Abuse.ch ( https://ransomwaretracker.abuse.ch )
- X-Force Exchange ( https://exchange.xforce.ibmcloud.com/ )
- AlienVault OTX Pulse ( https://otx.alienvault.com/ )
The above resources supply URLs and IP addresses of sites hosting exploit kits which can be automatically ingested by ThreatQ. Having them in the system is nice, but that alone will not prevent the attack. Since TQ is not a detection sensor but rather the “conductor of the orchestra” we need to distribute the threat data to the necessary tools. ThreatQ’s threat intelligence platform provides over 40 export options [Figure 2] by default, with the ability to create as many custom exports as needed.
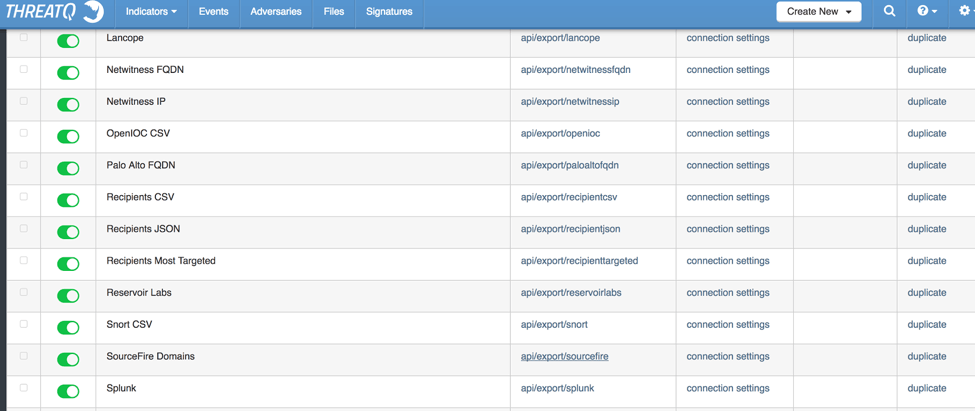
Figure 2. Export options in ThreatQ
These exports allow you to populate your security infrastructure with the relevant data you have ingested. For example, if you have Sourcefire/Snort IPS systems, the ThreatQ export system will automatically generate Snort rules to block the DNS requests for the domains hosting ransomware content [as seen below in Figure 3] and the same goes for Palo Alto devices. If you have a DNS Sinkhole or a cloud-based service such as OpenDNS this information could be sent over to those tools as well. With our custom export feature we can integrate with nearly any security product.
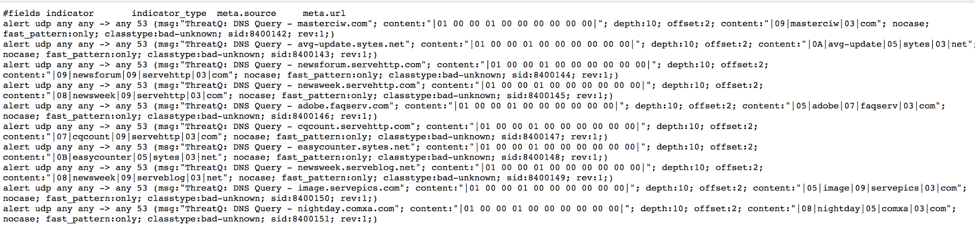
Figure 3. DNS requests for domains hosting ransomware
Spear phishing
Spear phish emails are another vector to deliver ransomware. Locky ransomware especially makes use of this attack vector. A malicious document that uses obfuscated macros to download the payload is the primary method of infection. It is a relatively simple but still effective way of getting the malware onto the system.
Blocking access to the download server, much like exploit kits above, is one way to stop the ransomware portion of the attack from ever executing. As spear phish attacks target specific people or organizations, many of the spear phish specific indicators never make it to OSINT sources. Only a small handful of commercial vendors provide email-related indicators that intersect with ransomware attacks. These vendors include PhishMe’s Malcovery, FireEye’s iSight Partners and Crowdstrike.
The ThreatQ threat intelligence platform can facilitate actions such as blocking on spear phish indicators at several layers. As mentioned before, indicators can be sent to IPS systems and DNS Sinkholes in case any users click on the malicious content. If an organization has an e-mail protection system then indicators such as Email Subject, Email Addresses and Attachment information (aka Filename) can be sent to those sensors to proactively block the attempt.
By using freely available indicators and ThreatQ, your team can aggregate ransomware information and disseminate it to your security infrastructure. You can block ransomware before it can run on your systems so you don’t have to resort backups or, far worse, pay the ransom and “trust” the attacker to decrypt the files.

0 Comments