Enhancing Your Threat Intelligence Platform with Comprehensive Visibility
Ed YoungWithin the realm of security operations, teams face an array of hurdles, with resource limitations standing out as a significant obstacle. At ThreatQuotient, we empathize with these challenges, and our ethos revolves around a data-driven approach to threat intelligence management. Our primary aim is to channel the precise data to the appropriate systems and teams, precisely when needed, amplifying the efficiency and efficacy of security operations to tackle these challenges head-on.
Visibility
The foundation of any strategy to secure the enterprise begins with visibility. Knowing what devices are communicating on your network is vital to accessing any risk that needs to be monitored or mitigated. Servers, desktops, laptops and personal devices all represent an entry point for an attacker to gain access or retrieve information.
Network infrastructure devices like routers and firewalls can provide the visibility of what is protected but more importantly what is not and the risk that is exposed to the organization. By ingesting these devices from sources like Jamf, Tenable or an excel import and storing them as assets in the ThreatQ Library, customers can filter on attributes like operating systems, subnet or apply tags to identify critical infrastructure.
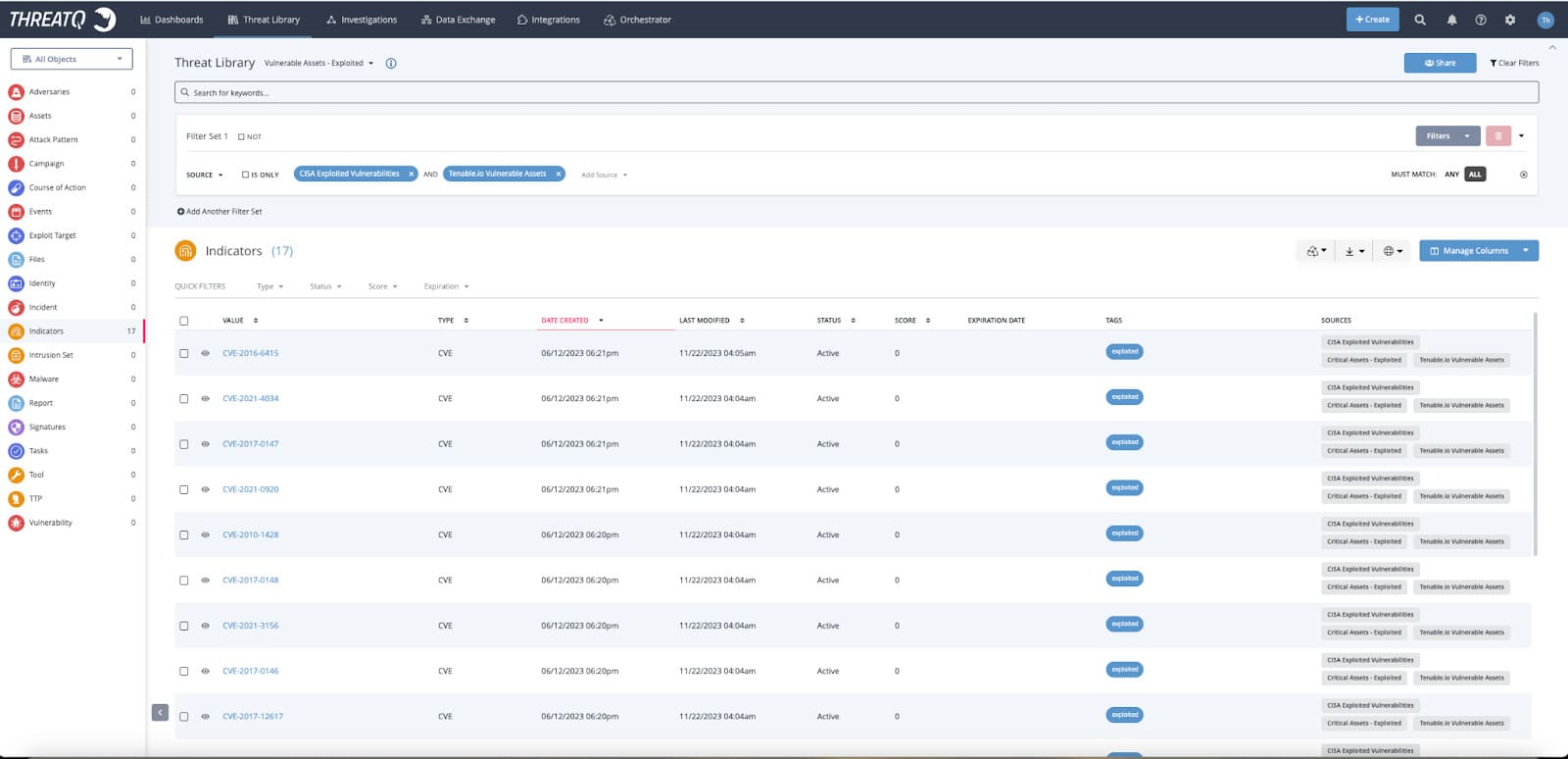
Vulnerability Data
There are many sources of vulnerability data available to security professionals, both structured and unstructured. Open source can provide valuable information of the active threats that are being exploited in the wild. Having this information will allow a customer to filter down to the data that pertains to their industry, region, etc. Further prioritization can be achieved using provider information from CISA, NVD, FIRST EPSS like the CVSS Score, Exploit Prediction Score, exploitability or focusing on a specific CVE that is most urgent in your environment.
Vulnerability Scanners
Vulnerability risk assessment can be enhanced by using scanners to identify risks to your organization. Scans are run against the network assets to identify vulnerabilities and suggest remediation steps for the known vulnerabilities that are found. Scanning tools like Tenable, Qualys or Rapid7 store device responses from the network to provide valuable information that could include the operating system, patch level and any risk to specific vulnerabilities known to the scan tool.
Threat Intelligence
Threat intelligence will provide the added context needed to make critical decisions on prioritizing the vulnerability risk in your environment. Data sharing sources such as AlienVault OTX will highlight threats to be prioritized and MITRE ATT&CK can help with knowing adversary tactics and techniques.
Remediation
- Ticketing – Putting details into a ticket is still the most widely used method for sharing remediation data. Additional resources and teams can refer to ServiceNow, Jira or The Hive for tickets to take action or collaborate on a plan. Historical data is preserved for tracking and training of lessons learned for the next time the remediation plan is executed.
- Blocking and Quarantine – Once the automated workflow has been properly vetted and the proper process is in place, some customers would want to use tools like Azure Sentinel or SentinelOne to automate simple tasks at the endpoint or firewall. Organizations understand the need to free up security analysts for more detailed work.
- Reporting and Alerting – Automatically generating a report or alerting another team that further actions are needed removes manual steps. Following the process, upon completion the automated workflow will provide the necessary next steps eliminating human error.
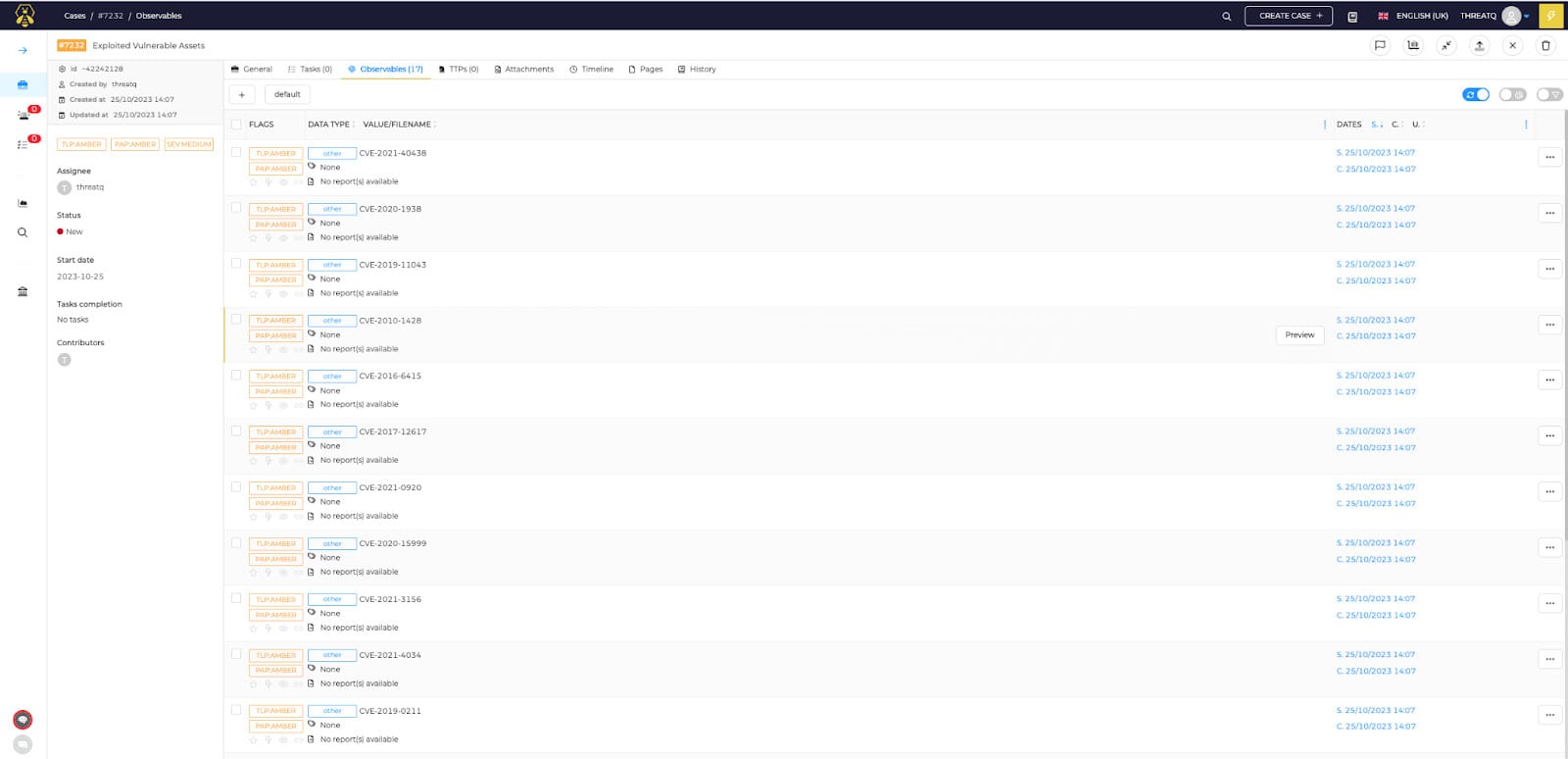
The critical role of visibility in securing an enterprise’s network infrastructure highlights the importance of understanding device communication, utilizing vulnerability data sources, employing scanners for risk assessment, integrating threat intelligence, and implementing diverse remediation strategies.
ThreatQuotient’s data-driven approach to threat intelligence management aids security teams in surmounting resource limitations. Prioritizing visibility, diverse vulnerability data, scanners for risk assessment, integrated threat intelligence, and varied remediation strategies fortify defenses, proactively guarding against evolving digital threats. To learn more, schedule a live demo.

0 Comments