Attack Attribution
POSTED BY RYAN TROSTThis is the third and final blog in my series on victimology. Let’s return to our previous investigation of the robertwanger [at] aol.com spear phish attacks. Now that we have a relatively decent baseline, we can start to compare other spear phish attacks to these to see if we’ve been targeted previously by this attacker.
Let’s build on the same logical workflow to conduct related analysis:
- create a hypothesis
- how to carve out the data
- now what to do, given the results
Hypothesis – I bet this isn’t the first time this adversary has targeted us.I can probably find additional attacks being sent from other misused email addresses – aol, gmail, hotmail, msn, etc.
In this example, another suspicious email [fw: why.man.die.younger?] is targeting the same financial employees, as well as, some non-financial employees so I decide to investigate it closer to determine if it could be the same adversary. There are numerous ways to try and tease out possible previous campaigns including correlating downstream IP address, message-IDs, transposing common characters of the sender’s email address, or taking the core email address [i.e. robert.wanger] and attaching it the other popular free email providers.
How to? We already performed the following activities for an attack that we think may be related:
- import the suspicious email into the TIP [“fw: why.man.die.younger?”]
- correlate it against existing internal/external intelligence
- associate the email to the recipient’s identity
In this case, since I’m capitalizing on a previous investigation, I just need to:
- import the email into our investigation
- right click Expand -> Identities to display the recipients
- right click Expand -> Tag to display any additional data points to help qualify or disqualify a relationship across victims
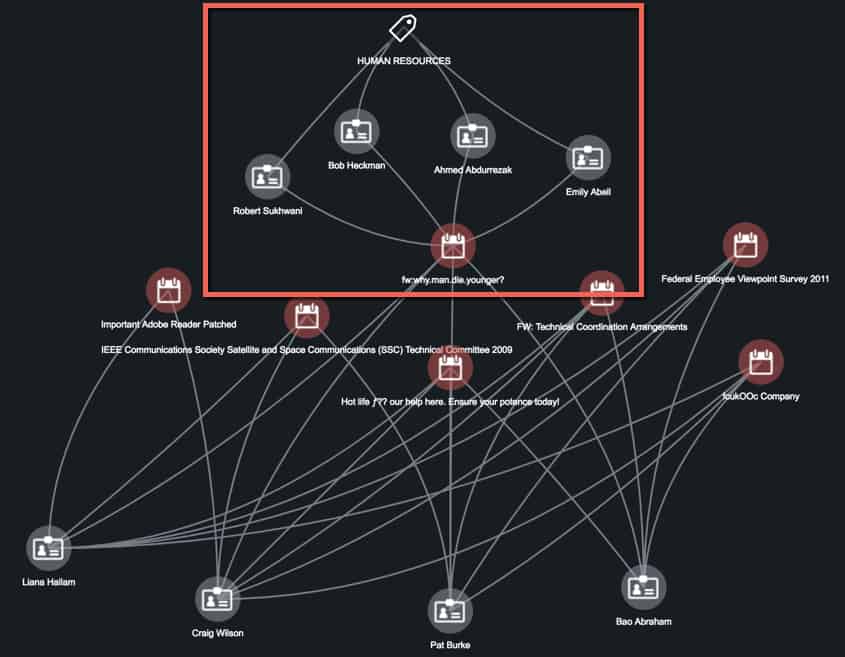
Figure 1: ThreatQ Investigations Evidence Board
The graphic above shows that from a pure victimology standpoint, this additional email could support a shift in their targeting to include the Human Resources department, but alone that is a bit of a stretch. If there were additional overlapping traits across the attacks, for instance, C2 or email sender, etc. it would help qualify the hypothesis.
Now what? Using victimology along with several other traits allows us to determine this suspicious email cannot be attributed to our previous adversary – at least not beyond a shadow of a doubt. However, if I were able to make a couple of solid, additional associations/connections across traits it would be exciting, as the shift in targeting opens up a lot of new research possibilities.
In summary, across this three-part blog series on victimology we’ve analyzed clues in a series of spear phish attacks to identify a trend in types of targets and attributes of the attacks. We’ve used these findings to raise awareness and educate employees. This analysis can also help us to better understand the objectives of the attackers and their TTPs and, when combined with information about the targets, allows us to take steps to mitigate risk by hardening defenses.
Hopefully this victimology blog series has inspired some new ways of thinking, but more so a capability to help you actually do it. Although it requires a bit of legwork to gather the internal data points, victimology can be an absolute treasure trove for intelligence-driven defense.
Once again…happy hunting!

0 Comments