Timeline Analysis to Identify Campaign Attacks
POSTED BY RYAN TROSTBuilding from our previous spearphish investigation, let’s continue to dissect the robertwanger [at] aol.com spearphish attacks.
Hypothesis – The six targeted spearphish attacks are split into several orchestrated campaigns.
How to? Displaying the spearphish events in chronological order is helpful but a bit too high-level to really perform a useful timeline analysis. Let’s turn our attention to the timeline graph at the bottom of the graphic below.
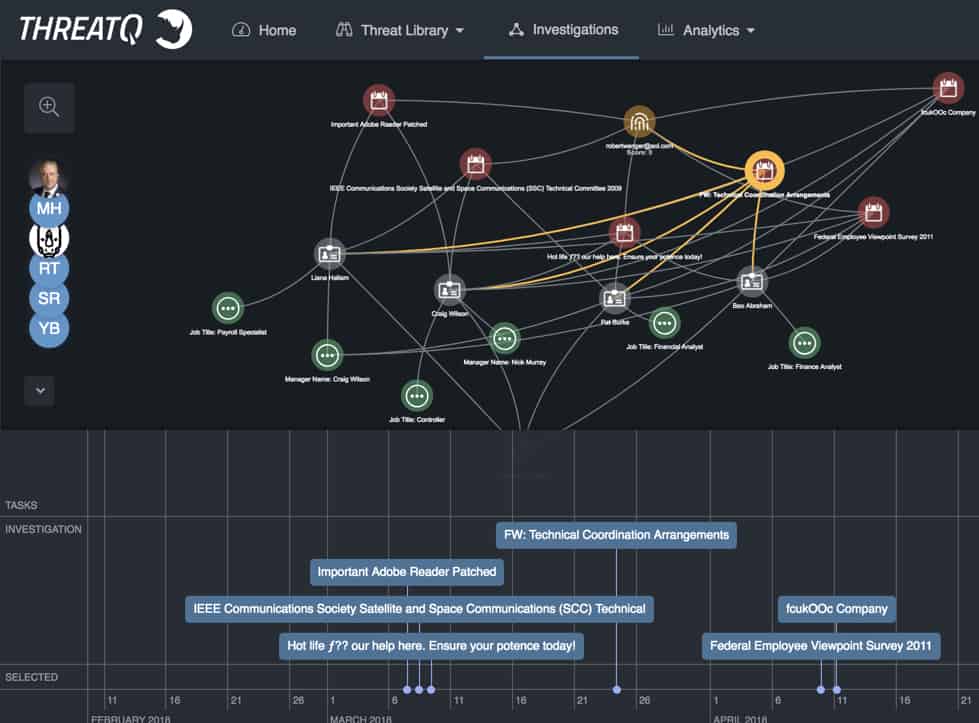
Figure 1: ThreatQ Investigations interface
So, it looks like the spearphish attacks encompass about 45 days and are actually broken up into three individual attack campaigns – nothing truly actionable but somewhat interesting. Next, let’s look at individual timestamps to see if there’s a pattern – were all the emails sent at approximately the same time, maybe the exact time which points to a lazy script, or ranging outside the normal business hours which could lead to geographical timezone conclusions? Unfortunately, I see nothing out of the ordinary.
Let’s take a step back and analyze the various campaigns:
| Campaign 1-A
To: craig@xxxxxx.com,liana@xxxxxx.com Subject: Important Adobe Reader Patched Date: 7 March 2018 www.sucecorp.com |
| Campaign 1-A
To: craig@xxxxxx.com,liana@xxxxxx.com,pat@xxxxxx.com Subject: IEEE Communications Society Satellite and Space Communications (SSC) Technical Committee 2009 Date: 8 March 2018 Content-Disposition: attachment; filename=”Inmarsat Management Team Fact Update.docx” |
| Campaign 1-A
To: craig@xxxxxx.com,liana@xxxxxx.com,pat@xxxxxx.com Subject: Hot life ƒ?? our help here. Ensure your potence today! Date: 9 March 2018 Content-Disposition: attachment; filename=”INDEMNIFICATION-AGREEMENT.docx” |
We see a mix of embedded URLs and attachments – beyond a deeper malware analysis, there’s nothing really analytically actionable. But circling back to the victimology aspect, it is interesting that Pat wasn’t included in the first email but appeared in the second and third emails which were both sent within 24 hours, respectively. A deeper internal look at Pat’s employee information reveals that his first day with the company was earlier that week. We might draw the conclusion that the first spearphish attack was sent without doing additional due diligence on the target(s).
The short timespan between emails could also tell us quite a bit about the adversary, specifically when comparing the malware delivered could point to either smaller or more extensive teams. In my experience, attackers typically do not deviate ‘drastically’ in malware tooling within such a short timespan. However, sequential attacks using new command and control infrastructure across attacks could point to a more sophisticated and organized team. Another possible conclusion is if multiple attack teams were involved, the reuse of the ‘robertwanger’ email address points to a lack of coordination. Welcome to the battlefield of “what-ifs.”
This same victimology analysis highlights an identical tactic for a fourth spearphish as Bao is now being targeted. Time to dive into the employee information to try and identify how or why he’s been added to the targeting list.
| Campaign 2-A
To: craig@xxxxxx.com,liana@xxxxxx.com,pat@xxxxxx.com,bao@xxxxxx.com Subject: FW: Technical Coordination Arrangements Date: 24 March 2018 Content-Disposition: attachment; filename=”Gadaad ornuudiin emegtei daichid.docx” |
Unfortunately, the third attack campaign doesn’t provide any fruitful leads. Yeah it happens.
Now what? This aspect of the attack helps frame the adversary’s dossier as it speaks to their targeting proficiency. It is always fascinating to analyze the delta between when a new employee starts at a company and when he/she starts being targeted – days, weeks, months? The smaller the delta, the more diligent the adversary. The other often overlooked aspect of this attack is the sequence of the recipients. If they are in the exact order every single time – it leads us to believe it’s a script which again, speaks to the adversary. Although this example might not be ideal because the sample size of four sequential recipients isn’t too irrefutable, it is a powerful search signature for larger recipient lists.
If the recipient list is too small because too many false positives are returned (small recipient list from the same department is a recipe for lots of legitimate emails), try and combine those with an additional parameter from the attacks – for instance, downstream IP address, C2 infrastructure hits, subject trends, etc.

0 Comments