Integrating Wapack Labs CTAC with ThreatQ
POSTED BY MIKE CLARKThe Cyber Threat Analysis Center (CTAC) from Wapack Labs is an interesting offering. What makes this service special among Threat Intelligence providers is the level of access given to customers. Most threat intelligence providers just offer curated intelligence, meaning threat data that has gone through an analytical process to decide what should or shouldn’t be sent to customers. In contrast, the CTAC gives you direct access to the raw data which allows analysts a lot of flexibility.
Using the ThreatQ Open Exchange API and the CTAC data, we have a lot of possibilities for integrations. In this post, I will show two examples. The first is a simple monitor for CTAC’s sinkhole data. The second is the CTAC and TQ integration focusing on CTAC’s keylogger information.
CTAC Sinkhole Monitor
A sinkhole is a DNS server with known malicious domains registered, so when infected systems reach out to it their information can be recorded. Our integration will periodically check CTAC’s data for any hits on CIDR Blocks we are monitoring. Once the CTAC Sinkhole integration is installed, we just have to enter our credentials and the CIDR Blocks we are interested in. This can be a comma separated list in cases when you need to watch for multiple subnets. The integration, once added to Cron, will reach out and check for any new information involving the specified CIDR Blocks.
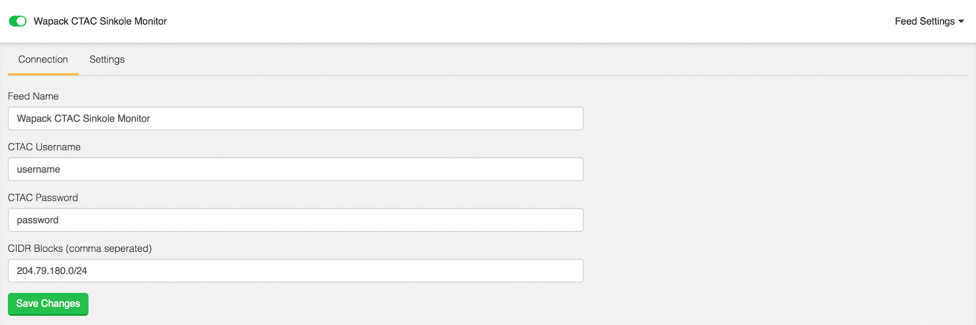
Figure 1: Configuration
Once run, any data that matches the given CIDR Blocks will create an Event in the ThreatQ threat intelligence platform. The Indicator data derived from CTAC is also automatically related to the new TQ Event to allow for easy pivoting. As we can see below, we captured the IP addresses involved, URLs used, and User Agents strings.
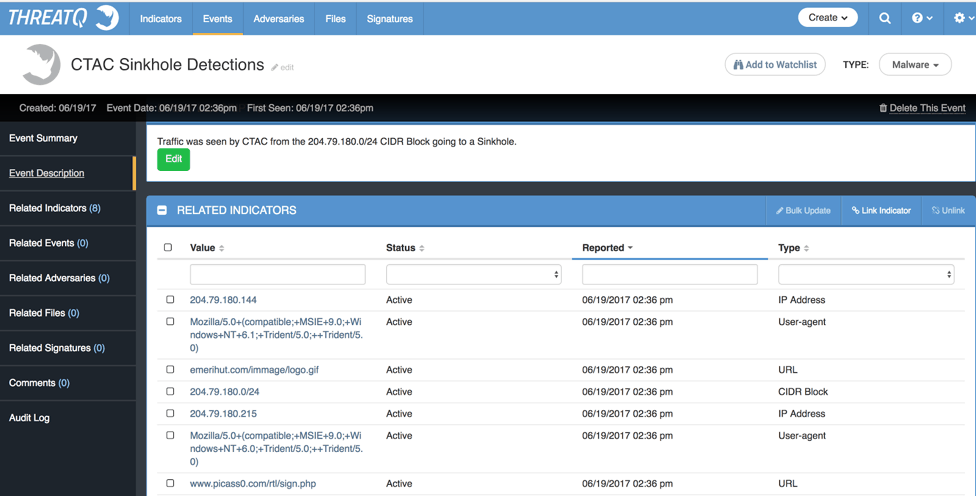
Figure 2: Example Event in ThreatQ
If we drill down to one of the URLs, we can get other valuable information such as the Malware Family involved. This can give your Incident Response team a nice head start in what to look for if there is a match from your network in the CTAC data.
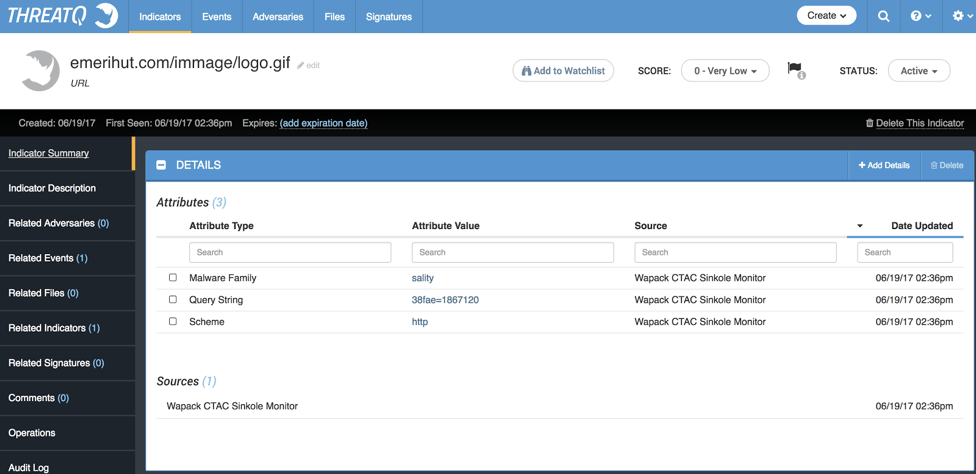
Figure 3: Indicator Details
CTAC Keylogger Monitor
The team at Wapack Labs captures the results of keyloggers and makes them available through their database. This includes the victim email addresses and the specific keylogger used, however, the passwords are redacted to protect the victim’s privacy. This is a great place to look for your organization’s data. The ThreatQ threat intelligence platform offers an integration to do this as well.
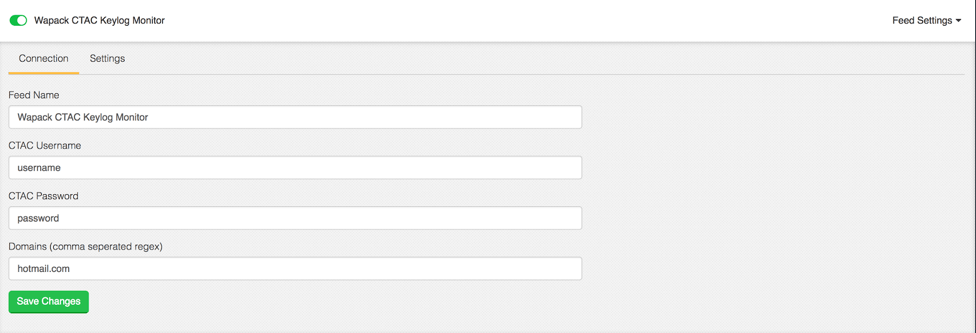
Figure 4: Configuration
As you can see in Figure 4, we set up this integration just like in our previous example, except we can include a list of domains we want to monitor for. If one of our domains is seen in the CTAC data, an Event is created in ThreatQ.
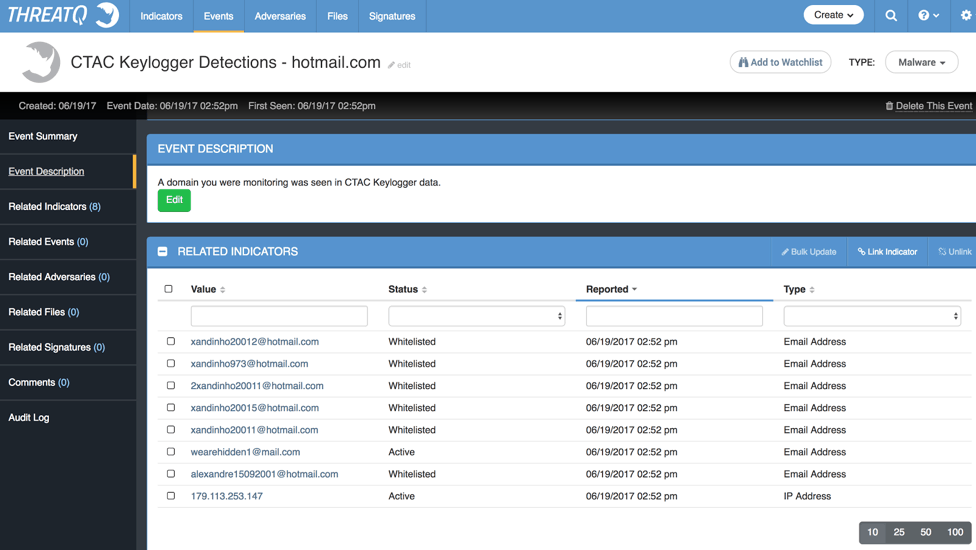
Figure 5: Example Event in ThreatQ
We have records for our domain in CTAC, as seen above. The Email Addresses we captured were Whitelisted automatically because in most situations we do not want to send our organization’s email addresses to any blocking security systems. This can be changed to fit your security policy.
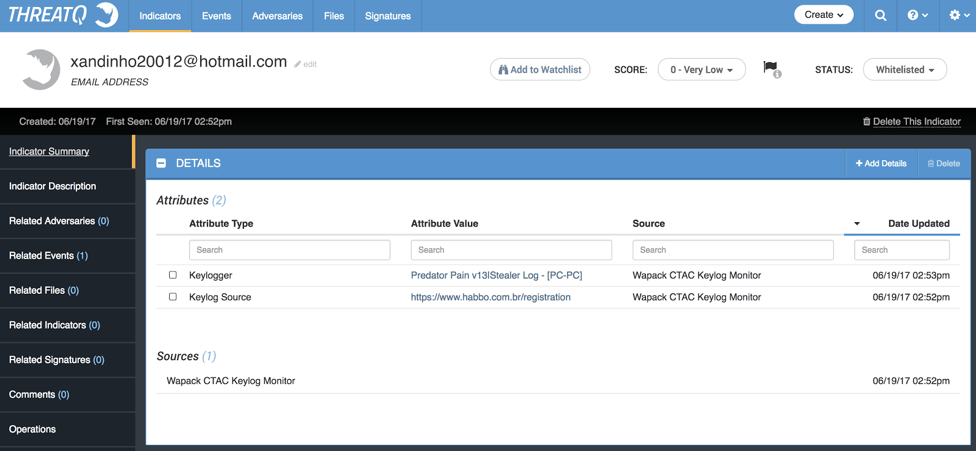
Figure 6: Example Indicator
If we drill down into the Email Address, we can see where the leak occurred and which technology was responsible. Only records that have an associated password are reported, so your organization can decide whether or not to issue a password reset for the involved account.
These are just two examples of integrations between Wapack Labs CTAC and the ThreatQ threat intelligence platform. With access to raw data and the simplicity of the ThreatQ Open Exchange, almost anything is possible.

0 Comments
Trackbacks/Pingbacks