It’s Time to Think Differently about Threat Operations
POSTED BY THREATQCan you really “manage” threats? Is that even a worthwhile goal? And how do you define a threat?
New research by Securosis explores why the current approach of treating every attack as an independent event and defaulting to the traditional threat management cycle – prevent, detect, investigate and remediate – simply hasn’t worked.
Organizations need a way to learn from attacks in the wild, understand the actual risk they face from specific attacks, and make better use of limited resources.
This new report, Introduction to Threat Operations, explains the issues that make dealing with attacks so challenging. More importantly, it provides fresh thinking into how to gain more from your existing resources, including:
- harnessing threat intelligence from potentially hundreds of data sources,
- enriching alerts so you can validate and assess criticality, and
- creating an inclusive process based on trustworthy automation.
Finally, through an example of threat operations in action you’ll see how shifting your approach to threat intelligence helps you break the relentless cycle of attack, respond, clean up, repeat. With a threat operations mindset you can prioritize and take action to more effectively mitigate risk with your existing tools and talent.
Learn more. Download the white paper now and register for the webinar.
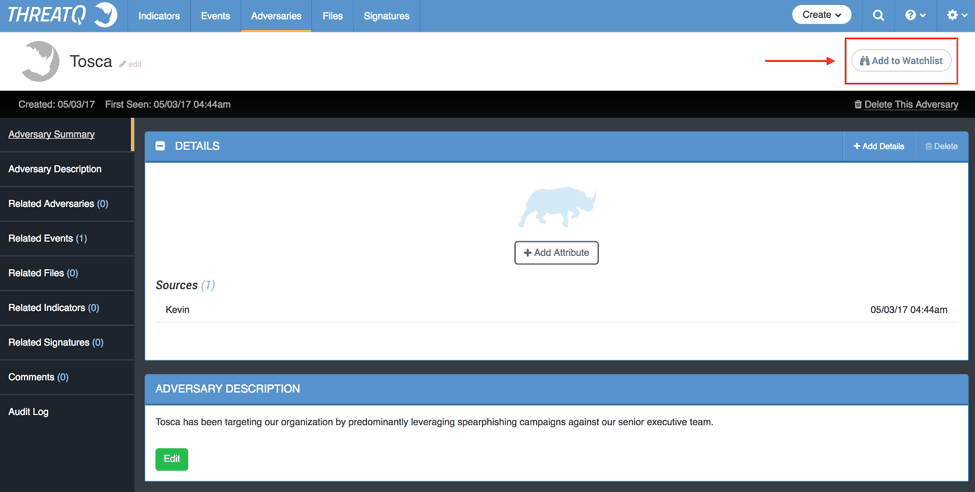
Figure 1: ThreatQ interface
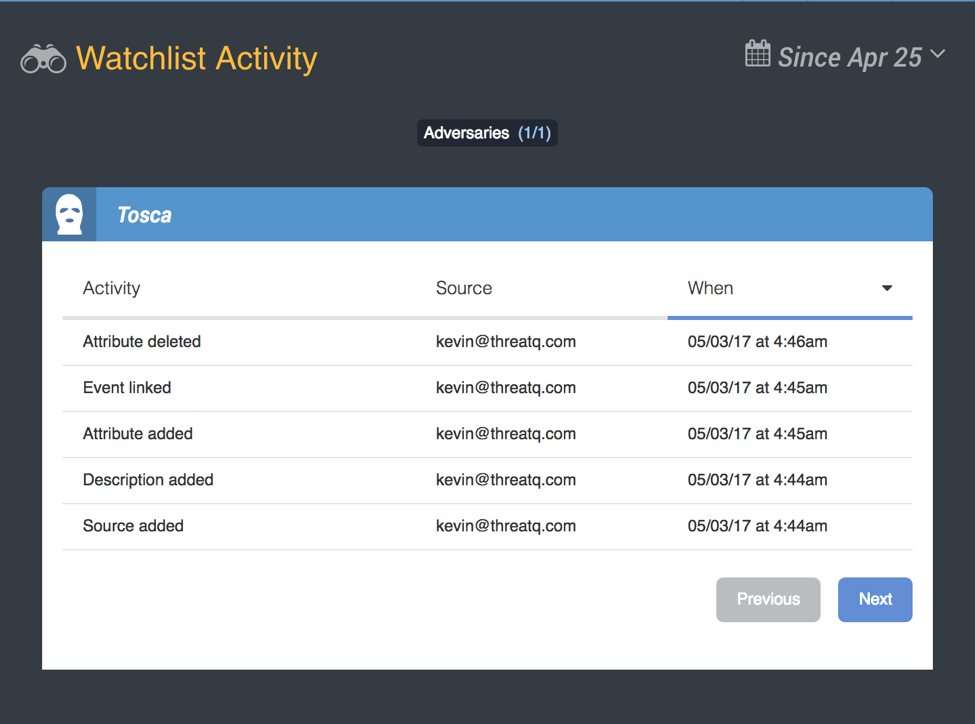
Figure 2: Active ThreatQ Watchlist
When I return to my desk, I log into the ThreatQ User Interface and am able to see any recent activity related to this adversary.
As other analysts automated threat intelligence feeds, integrate messages, and contribute to the data within the Threat Library, any alterations to Tosca are immediately added to my watchlist, visually notifying me of the change.
In addition to adversaries, the Watchlist is also able to track other object types, including: attachments, events, indicators, and signatures.
An API endpoint makes it easy for analysts to interact with their watchlists through any custom integrations or scripts.
To learn more about watchlists and the ThreatQ Threat Library, request a free evaluation.

0 Comments