Leveraging NSFocus to Categorize Threats and Pinpoint Valuable Connections
It is no surprise that everyone, including organizations, are vulnerable to a large amount of threats on a daily basis. In Q3 of 2016 alone, Panda Labs captured 18 million new malware samples; that is not including samples detected by other companies. Furthermore, in a study done by Friedrich-Alexander University (FAU), 78% of participants stated in a questionnaire that they were aware of the risks of unknown links. That said, using a mock spear phishing email, 45% of the participants clicked on the link, even though only 20% reported that they had done so. Unfortunately, while malware developers are becoming smarter and more crafty, the average person and organizations are not detecting threats and adapting fast enough. According to Barkly (December 2016), after experiencing a cyber attack, only 31% of organizations made changes to their security plan while 52% had not planned any changes and 17% were “not sure.” Clearly this is not ideal. To help more organizations take a proactive stance, the ThreatQ threat intelligence platform along with NSFocus provide a solution to more effectively identify and fight these threats.
Using NSFocus’ feeds and enrichment endpoints, ThreatQ is able to more accurately categorize and prioritize indicators. ThreatQ’s NSFocus Integration allows indicator types such as URLs, domains, and hashes to be pulled in and added to your ThreatQ instance. Following that, you can use ThreatQ’s NSFocus Operation to enrich those indicator values with important details such as related CVEs, hashes, emails, domains, and other valuable information.
On top of the related indicators, WHOIS information, hash information, and vulnerability information, NSFocus provides categorical and ranking attributes. When paired with the ThreatQ threat intelligence platform, they provide a powerful tool to analyze threats. As seen in Figure 1, NSFocus’ 80 categories for URLs as well as 10 more categories for threats can be effectively incorporated into the ThreatQ scoring system to prioritize certain categories and threat types based on these attributes.
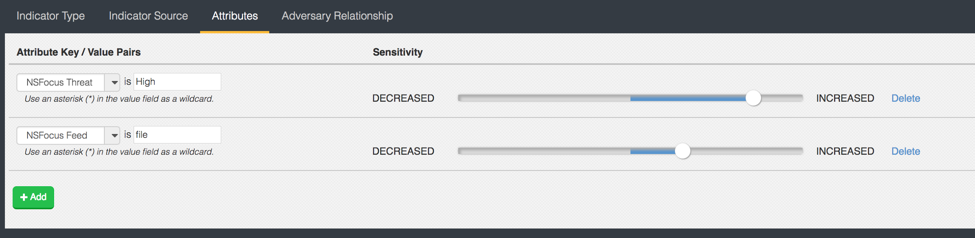
Figure 1: Scoring NSFocus attributes using ThreatQ’s Scoring System
Initially, the NSFocus feed shows indicators and their threat level. These indicators can be further populated using the NSFocus Operation within the ThreatQ threat intelligence platform. The operation will reach out to NSFocus’ API, and pull more information into ThreatQ, providing more context on the given indicator. In Figure 2, you can see a URL which was returned from NSFocus’ URL feed along with the attributes and related indicators from the operation. The API returns attributes on the URL’s reputation, score, and category. These attributes can then be added to the indicator in ThreatQ.
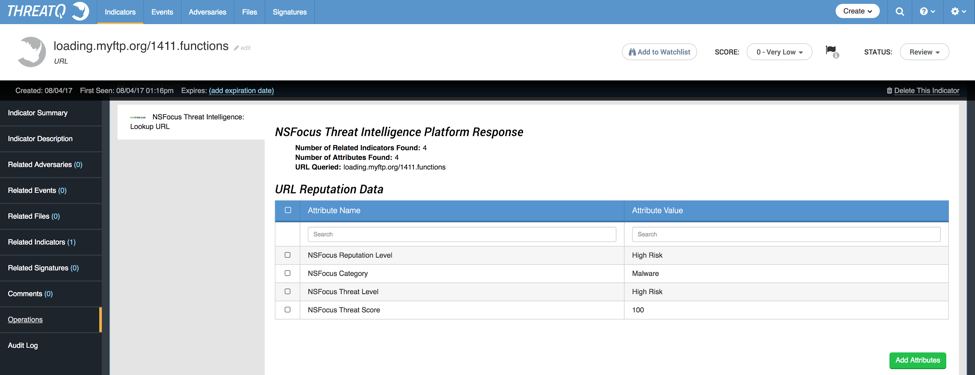
Figure 2: Returned attributes from NSFocus’ Operation for URL
The Operation also returns related indicators, as shown below in Figure 3. For example, this URL returned two related files consisting of four hashes. You can add these to the ThreatQ Threat Library by checking off the indicator values you want to relate, and clicking the ‘Add Indicators’ button. Once added, you can pivot to that indicator, and then run the operation again to retrieve more information on that indicator.
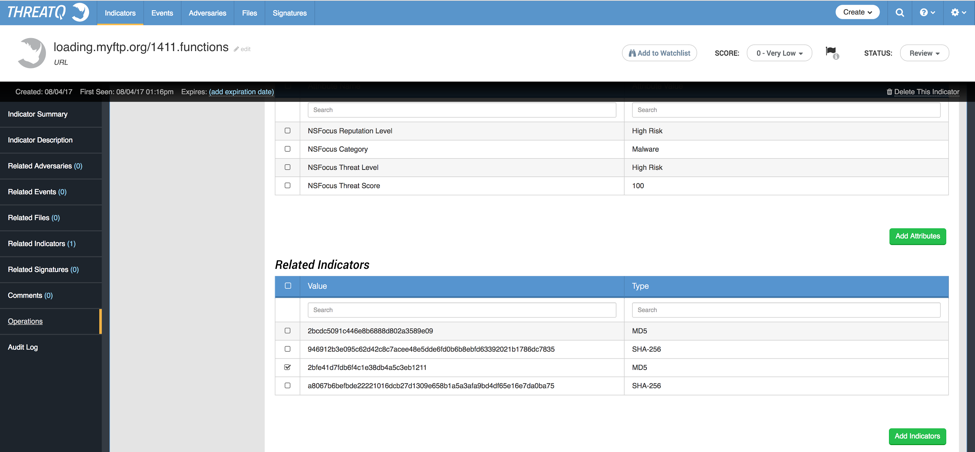
Figure 3: Returned related indicators from NSFocus’ Operation for URL
For this related indicator, the operation did not provide any additional valuable information as attributes, as seen in Figure 4. However, looking at Figure 5, the MD5 hash brought in an IP Address indicator that the URL indicator did not bring in.
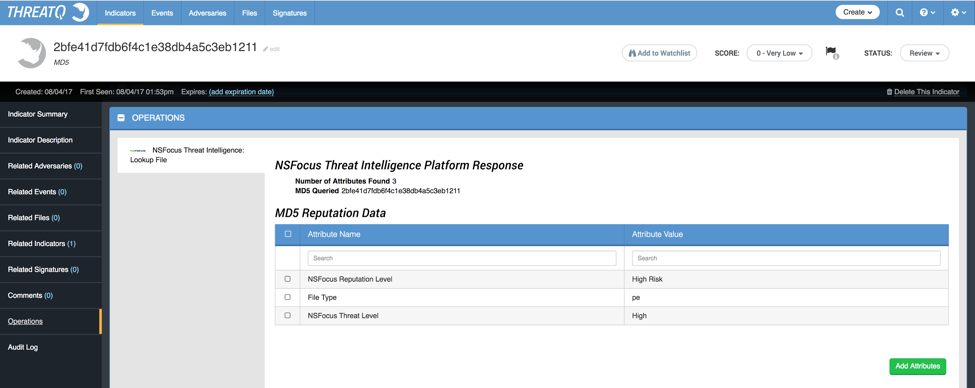
Figure 4: Returned attributes from NSFocus’ Operation for MD5 hash
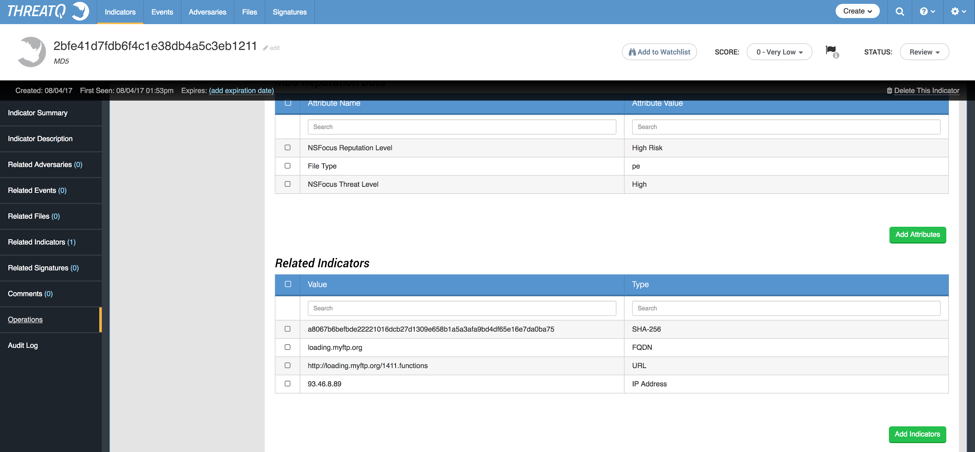
Figure 5: Returned related indicators from NSFocus’ Operation for MD5 hash
After adding this new IP Address as a related indicator, we can pivot to that indicator and run the NSFocus Operation again. The Operation brought in many more attributes as shown in Figure 6 as well as many more related indicators as shown in Figure 7. These attributes will be useful for analyzing threats.
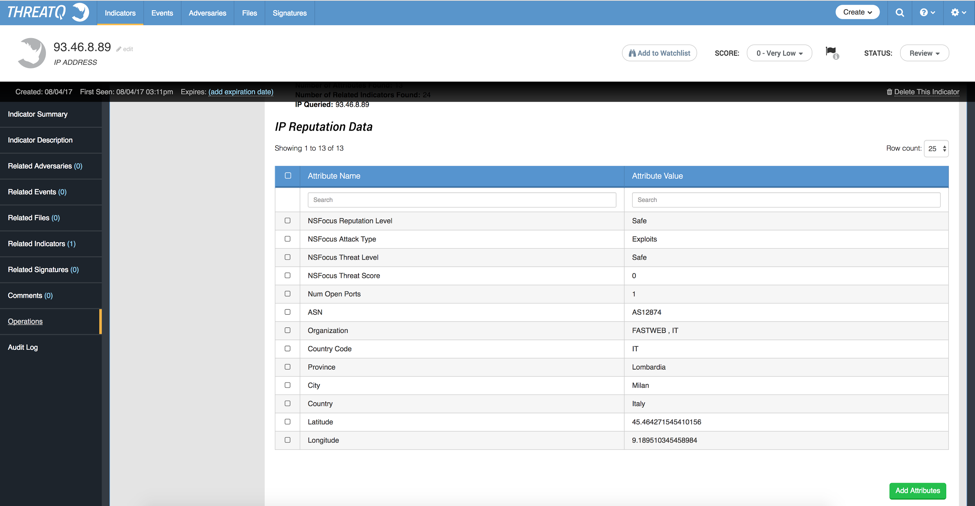
Figure 6: Returned attributes from NSFocus’ Operation for IP Address
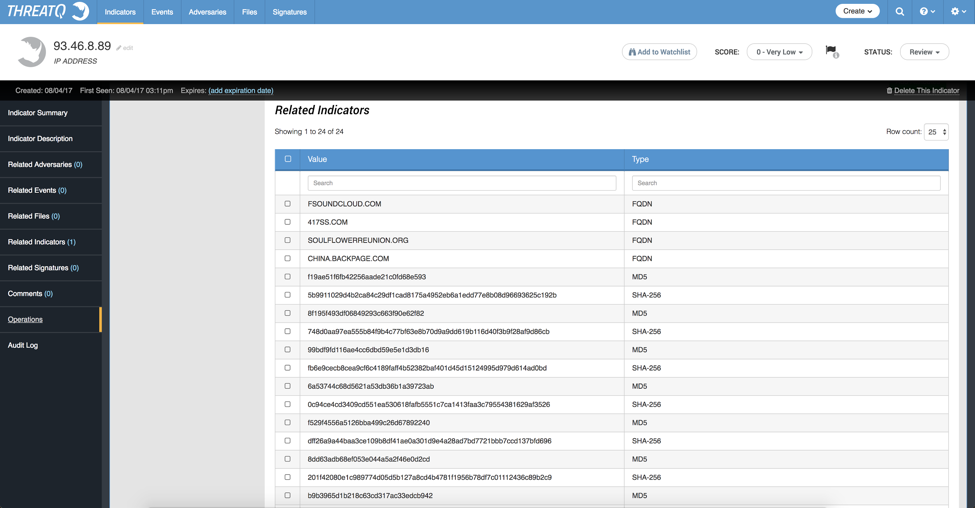
Figure 7: Returned related indicators from NSFocus’ Operation for IP Address
If an analyst wants to, they can keep adding the related indicators, and digging deeper and deeper into the chain of threats. Instead of manually using the operation for each indicator, the NSFocus integration includes an ‘auto enrich’ feature which will automatically enrich the immediate indicators with information seen from the operation. This will increase the runtime of the integration, but could save you time during your analysis.
NSFocus provides valuable categorical data, along with other useful metadata. When paired with the ThreatQ threat intelligence platform, it offers a very powerful intelligence analysis system. Not only will you be able to rank threats by NSFocus’ attributes, but you will also be able to dig very deep into indicator relationships. This will help analysts better understand the connections between indicators, and ultimately, be able to use that information to better protect against these threats.

0 Comments