An Up-Close Look at How to Increase Threat Hunting Efficiency
POSTED BY LIZ BUSHThreat hunting, the act of proactively searching for the existence of indicators of compromise within your environment, is a hot topic. Security teams engage in threat hunting when they learn of a threat from an external source, believe they might have missed something in the past, or receive a call from management about the latest attack in the news.
Time is critical when it comes to threat hunting because the costs of a data breach escalate the longer it takes to detect and respond to an attack. Several different studies find that mean-time-to-detection (MTTD) is in the hundreds of days and the average cost of a data breach is now at $3.86 million, up from $3.62 million last year according to the 2018 Ponemon Cost of a Data Breach study.
While the definition of threat hunting is simple, actually engaging in threat hunting is quite complex and can be very time consuming. Many security teams are wondering how to get started. In a recent webcast, “Leveraging Threat Intelligence for Efficient Threat Hunting,” ThreatQuotient’s Anthony Stitt and Robert Streamer show how ThreatQ can help.
After the initial compromise and before the point of detection is the threat hunting zone where you’re trying to catch things as quickly as possible. This is where ThreatQuotient’s threat-centric platform comes in. It supports multiple use cases including threat hunting and serves as a threat intelligence platform to bring automation, prioritization and collaboration to the threat hunting process – a powerful combination of capabilities.
Working up the Pyramid of Pain, Anthony and Rob show how ThreatQ leverages these capabilities to make your threat hunting operations more efficient. 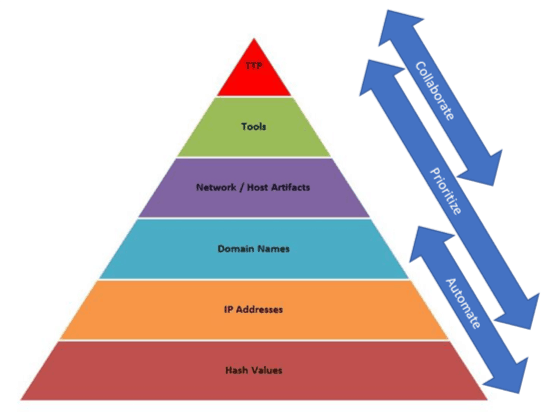
It is easy to search for atomic indicators like hash values and IP addresses, but it is also easy for attackers to change these indicators and repurpose the same campaign. However, as you move up the Pyramid of Pain looking for artifacts that attackers have left on your systems, and are able to understand their tactics, techniques and procedures (TTPs), you can more successfully thwart attacks because these elements are more costly and time consuming for attackers to change.
Watch the webcast below and see the 20-minute demo of how to:
- Automate the search for atomic indicators like hash values, IP addresses and domain names as well as higher level indicators like rules and signatures.
- Prioritize data points and information stored it the Threat Library to ensure the team is focused on high risk indicators, using the ThreatQ customized scoring capabilities.
- Collaborate efficiently across tools and teams through integration and by sharing relevant, prioritized intelligence to guide the hunt as analysts move up the Pyramid of Pain.
Traditionally threat hunting has been a very manual and time-consuming task that requires very skilled analysts who have sufficient time to work on complex problems. By automating some of the more mundane aspects, prioritizing for relevance, and enabling collaboration across teams and tools, ThreatQ allows analysts to move through the threat hunting zone more quickly and reduce the impact of an attack.

0 Comments