Taking Action on GRIZZLY STEPPE Data with ThreatQ
POSTED BY MIKE CLARKIn early October, the DHS’ NCCIC and the FBI released a Joint Analysis Report (JAR) detailing a campaign they attribute to Russia. The campaign target was the Democratic National Committee and is alleged to have resulted in numerous data leaks. Not only was the attack attributed to Russian nationals, but the Russian Intelligence Services (RIS) were also implicated. The JAR was provided in multiple files and formats. A PDF describing the event for human analysis, a STIX file that provided technical indicators, and also a csv for systems that aren’t able to work with STIX. ThreatQ’s threat intelligence platform can parse and ingest all three file formats, and in this blog post we will demonstrate how to use this information in ThreatQ and your security infrastructure.
Before we import the data, let’s create a new Adversary so we can easily attribute all of this data. The report uses the term GRIZZLY STEPPE for the adversary name, so we will as well. Other Intelligence Providers use different names such as APT28. If they already exist they can be linked to this new Adversary. Creating an Adversary is easy and once the Adversary is created, we can easily link Indicators to it.
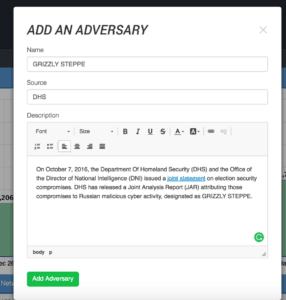
Importing
ThreatQ can handle STIX in two ways: using a TAXII endpoint for automated download and ingestion, and importing a single STIX file on demand. Since the report was released as an XML file, we will use the manual import process. To start, you bring up the Create Indicator window, drop the report in and select the STIX parser.
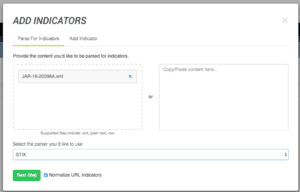
After this step, we have the opportunity to add more context, save the file, set the a status for any indicators status, and add any additional attributes from the report. Finally, we will have a chance to review all of threat data that was extracted from the STIX file. Here an analyst can prune and massage the data as they’d like before the final import. The TQ Platform will also inform you at this step if an Indicator is already present in the system.
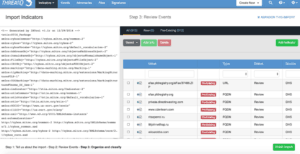
As seen above, all the Indicators in the STIX file will be related to the GRIZZLY STEPPE Adversary. We can also set a confidence level about this relationship – we’ll go with a value of 25%. This is completely up to the analyst. I have chosen a lower value due to the prevalence of TOR nodes and the lack of context surrounding many of the Indicators.
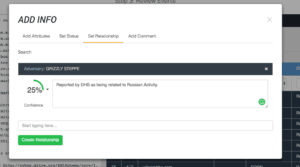
Now we save the import and all of the Indicators are created and the relations made. We can also relate the JAR STIX file to the Adversary by clicking on the Link File button under the Related Files section. There has been a bit of industry blow-back on the quality of some of the indicators so we’ll play it safe and set the indicator status to Review, so they will not automatically be sent to our security infrastructure potentially causing major problems. This is an important thing to consider when working with intelligence, the consumer should be able to make their own decisions and assessment of how to apply the information provided. ThreatQ aids in this process. The Adversary we made now looks like this.
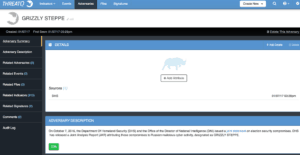
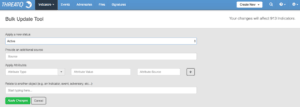
Alternatively, after you import the indicators if you have a change of heart and want the GRIZZLY STEPPE bundle to deploy to your infrastructure, you can use the Bulk Modification tool to change all of this Adversary’s Related Indicators status to Active.
Hunting
One of the first questions we want to answer is: Have we seen any of these Indicators? There are a number of ways we can go about this, for example, we can Export them in a format that our SIEM can perform a search, but an alternative approach is to check our logging devices for them. We can run a historical search based on an Adversary.
This would allow a Threat Intelligence team to more easily report on the activities of a specific group against their organization. This is especially helpful when an Intelligence Provider released a report on a newly discovered Adversary. Using ThreatQ’s threat intelligence platform, the Threat Intelligence team can show its value by quickly responding to the report and informing the proper stakeholders.
Leveraging Operations, such as a SIEM query, we can automatically perform a ‘Rear View Mirror’ search (aka historical search) against all of the Indicators related to an Adversary. The result of which is an Event with all the Indicators which were seen as relations. An analyst can then pivot to them and take a closer look at the logs.
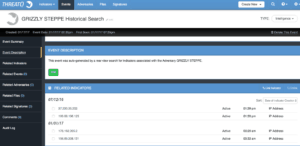
This can be the basis of a report to management or to your customers on how the latest revealed Adversary whitepaper is related to their organization.
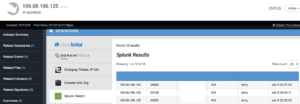
In the above example the Indicators shown were seen in our SIEM. This search and event creation can be launched with a single action, making it very easy to get started. This approach, based on an Adversary or other Entity, allows for focused reporting as they are all related to that top level subject. Threat Intelligence is much easier to understand and act on when organized in such a way as it provides a clear objective. In this case, to see if GRIZZLY STEPPE made any attempts against an organization. An analyst can then pivot into the Indicator and run a SIEM Operation to see the specific log entries which were seen from the Adversary.

0 Comments