Integrating Qualys with ThreatQ to Correlate Vulnerabilities with Threat Intelligence
POSTED BY NIR YOSHAAs we discussed recently, the ThreatQ Threat Library now supports the inclusion of vulnerability data using the Common Vulnerabilities and Exposures (CVE) standard. This allows defenders who are doing both vulnerability assessments and deploying the ThreatQ threat intelligence platform to easily identify vulnerabilities within their own environment that are being used for known exploits and better protect against such attacks.
Our recent integration with Qualys is a great example of how this works.
Defenders who map their vulnerability assessment results to CVEs and Qualys IDs, can link common attack patterns to specific common weaknesses, using the ThreatQ threat intelligence platform in order to focus their efforts where the risks are greatest.
Configuration
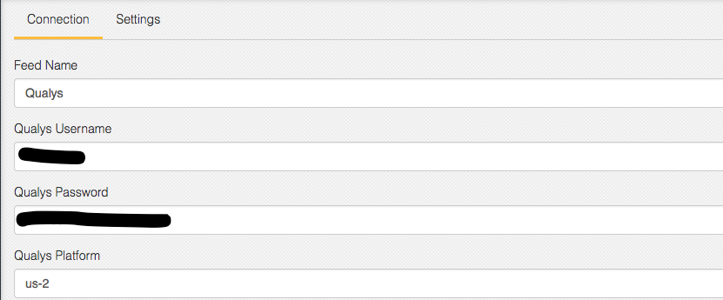
Configuration
Setting up the Qualys connector is easy in the ThreatQ interface. Simply add the credentials in the configuration page (Figure 1).
Qualys ID
Qualys maps the Qualys ID (QID) with CVEs whenever possible. The QualysGuard Vulnerability KnowledgeBase is updated on a daily basis with the latest vulnerability and CVE mapping information from a variety of sources.
The scanning results per QID can include multiple CVEs and hosts that are vulnerable to the specific QID (Figure 2).
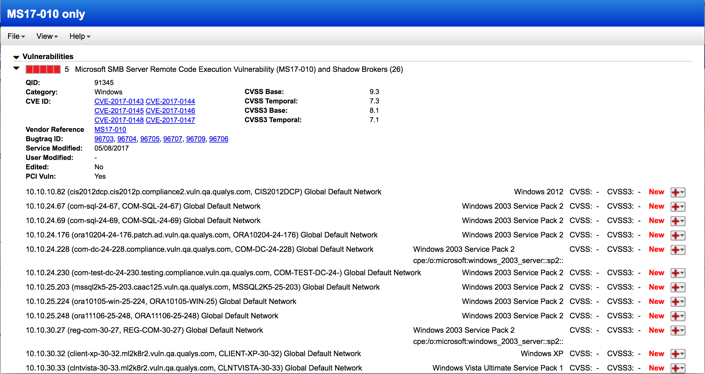
Qualys search results per QID
ThreatQ CVE mapping with Qualys scanning results
ThreatQ interacts seamlessly with Qualys scanning results and identifies CVEs that match ThreatQ known threats.
As shown in Figure 3, the Qualys “source” is added to the CVE indicator in addition to the original threat intelligence sources and attributes (e.g., CrowdStrike, iSIGHT etc.).
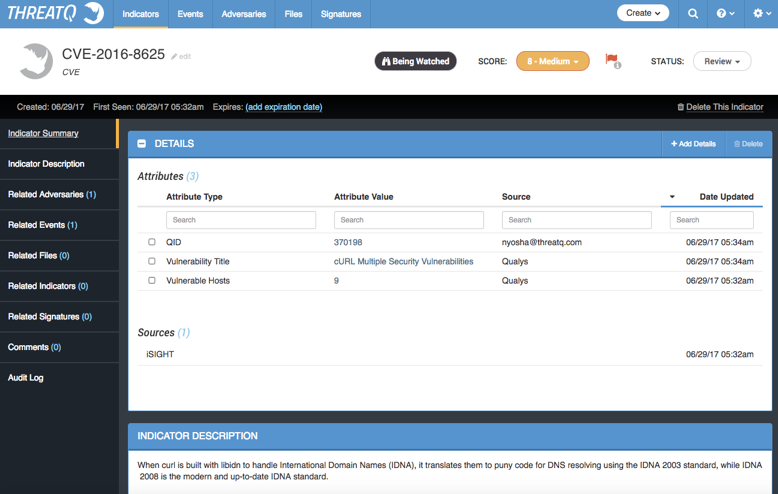
Qualys attributes within ThreatQ
Use Case and Future Integrations
Leveraging Qualys scanning results and ThreatQ intelligence can help teams prioritize the patching list based on current threat information.
In addition, it allows teams to identifying event within the ThreatQ threat intelligence platform to include CVE-related activities. For example, a specific actor weaponizing a Word document to compromise a vulnerability within MS-Office. If this event is relevant to an unpatched version within a company, addressing this vulnerability would take priority. If this patch is already installed, this threat is less relevant to the organization and can take lower priority.
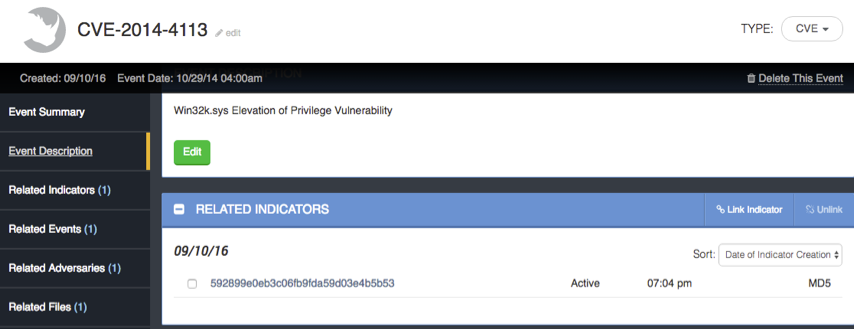
CVE event within ThreatQ
Summary
Threat Intelligence is really the information behind adversaries and their campaigns. The tactical details of their attack includes indicators of compromise such as exploits and vulnerabilities.
Using the Qualys integration, the ThreatQ threat intelligence platform can help organizations to identify the potential exploit targets and attack vectors within their environment. This integration helps security and patching teams to prioritize and resolve both the action required to mitigate risk and the underlying vulnerability that allowed the attack to occur in the first place.

0 Comments