From the Trenches, Part 2: Working with Employees to Strengthen Security Posture
Liz BushDuring COVID-19 and the shift to a remote work environment, employees play an even greater role in helping to protect organizations against cyberattacks. In light of this, we’ll conclude our blog series for Cybersecurity Awareness Month with a few more recommendations from Aaron Louks, ThreatQuotient’s Security Operations Engineer, on how to work with employees to strengthen your company’s security posture.
How has an all remote staff changed your security plan?
ThreatQuotient has operated with a hybrid model for some time now, so the transition to all-remote was painless from an operations perspective. Our models take into account that Identity is the true perimeter, so we implement a Zero Trust architecture where appropriate.
How vulnerable are home wireless networks and what are your recommendations for making it more secure?
It depends on which protocol you’re using. WEP encryption can be cracked in about 11 minutes. It’s recommended to use either WPA2 or WPA3, as they are the most difficult standards to crack, though not impossible. WPA2 has a 4-way handshake vulnerability that allows an attacker to intercept the password hash. Depending on the complexity and uniqueness of the password, the attacker could compare the intercepted password hash to rainbow tables (pre-computed hash tables) and get a match to reveal the password.
Recommendations:
- Change your wireless password regularly
- Check your router for any unknown connected devices
- MAC Address Authentication lets you define which hosts are allowed on your network, but anytime you connect a new device, you have to manually input the address to allow it to connect. While definitely not convenient, it helps keep people out and worth the effort.
Generally, home users are not running RADIUS servers to be able to use WPA2-Enterprise, so they can’t take advantage of 2-factor authentication on their home network.
The thing to keep in mind is: A sufficiently motivated and skilled attacker could gain access to your network, but are you a worthy target? If you are, then you should invest in enterprise-grade systems that implement MFA.
What are the three most important things employees can do to help mitigate risk?
- Be mindful of what they’re clicking on. Take a moment to stop and think, inspect the link.
- Report suspicious behavior immediately.
- Follow policy and procedures – they’re designed to mitigate risk.
Any tips for dealing with shadow IT?
Shadow IT emerges to fulfill a need. All I can say is: Listen to your users and accept feedback on what they need to complete their job. Make sure they have an easy way to ask for solutions. If you’re providing the tools they need and they’re satisfied, they won’t seek unauthorized tools and services.
What do you think of password managers?
I mostly have positive things to say about password managers, but like anything, they’re a double-edged sword. It’s great to be able to store all your passwords and generate sufficiently complex passwords for each site without having to remember them all, but all of those credentials are protected with a single master password (and hopefully MFA). It’s still possible for it to be a single point of failure (though unlikely).
On the whole, I highly recommend them and encourage the use of pass phrases. I always think back to this XKCD cartoon:
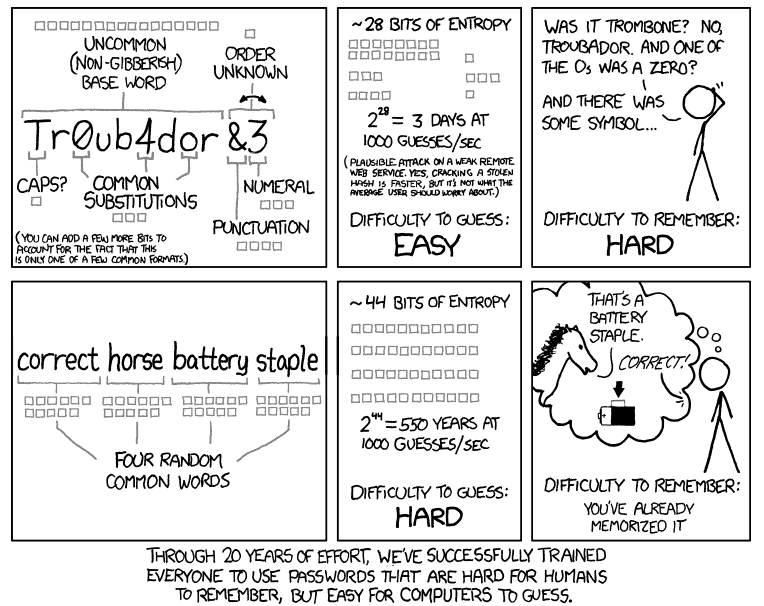
We hope you’ve found our blog series for Cybersecurity Awareness Month helpful. In case you missed any of the topics we’ve covered, here are links for your convenience:
From the Trenches, Part 1: Security Strategy and a Path To Success
It’s Back to Basics During Cybersecurity Awareness Month
Phishing Attacks are on the Rise – Do your Part to Mitigate Risk

0 Comments