Examining Ricochet Effects of Spear phishing Campaigns
POSTED BY MIKE CLARKThere are many ways your organization can be affected by a spear phishing attack beyond the obvious – being the direct target. For example, a doppelgänger of your domain could be used to send the malicious email. Another way, and the focus of this article, is when your company or employee information is used to register malicious domains that attackers use to host content. We call this a ‘ricochet’ attack as your organization may not even be an intentional target. But intentional or not, the attack could be incorrectly attributed to your organization.
In this post, we will discuss the ways you can investigate these types of attacks using the ThreatQ platform. We will use a new feature introduced to the platform called “Operations” to facilitate the investigation process. Operations are custom tools and workflows, written by ThreatQ or the community, which integrate into the platform and allow more advanced integrations.
Now on to the fun stuff…catching the bad guys!
Notification
As with most criminal activity, learning that something malicious is happening generally starts from a tip. An outside organization may contact you about a new DNS registered which they discovered through a Brand Protection service. The registration details of the offending site include information on one of your employees. For this scenario, the site involved is: threatqq.com. Note the extra ‘q’, which is easy to overlook if someone is just glancing at it. To start the investigation we will create an FQDN indicator for this site.
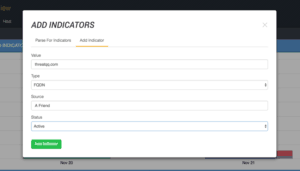
With the doppelgänger indicator in the system, we can now commence our hunt. Like any hunt, one of our primary goals is to avoid sending any traffic to the potentially malicious domain from any of our systems. Not only is it dangerous, it could tip off the threat that we are actively investigating.
The next step is to perform a simple WHOIS on the site. For this, we have an Operation which leverages DomainTools. The Operation will query DomainTools for WHOIS information, and allow us to extract Indicators such as the e-mail address of the registrant. While most of the other WHOIS information can be faked (i.e., street address, contact information, etc.), the e-mail address is generally real, albeit a throwaway created by the threat actor just for this campaign.
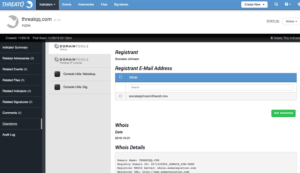
As we can see from the screenshot, someone calling themselves Socrates Johnson registered this domain using an e-mail address of socratesjohnson@bandt.mov. We can easily add this information as a new Indicator. ThreatQ will also automatically relate it to the threatqq.com Indicator. The next step is to pivot to the new Indicator and run further Operations to gather more context in hopes of finding more pieces of the puzzle.
DomainTools offers a service called Reverse WHOIS. This lets us search all of DomainTools’ records for pieces of information, such as Registrant E-mail. With this at our disposal, we can discover what other websites were registered with this e-mail address. Our DomainTools Operation supports this search as well, as seen below.
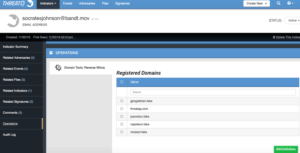
All of the domains Mr. Johnson registered can also be added as Indicators for further pivoting and data enrichment. They too will be related to the parent Indicator which is the e-mail address in this case. With this information, we can get an idea of common themes and potentially who may be the next target – to warn them. It is important to point out that ThreatQ does not automatically associate the first domain [threatqq.com] to the new domains identified but rather associates all the domains through the common link – the e-mail registrant.
The next step of the investigation is to determine how this threat is using the malicious domains. For that, we will use additional Operations tools. It could be that these domains have not had a server assigned to them yet, or they could be live. We can use the Dig Operation to get more detailed information on the status of the domain.
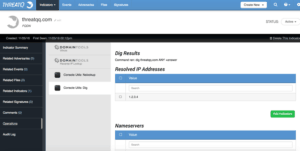
With the Dig command, we can uncover interesting information about the domain. This includes the IP it is resolving to, nameservers, mailservers, and more. Here we see that the malicious domain threatqq.com is resolving to is 1.2.3.4 (fake, of course). We can now add that as an additional Indicator which will be related. Now that we know that the domain has an IP address, is it actually up and able to be contacted? For that, we can use another Operation called IsUp which makes use of the site “Down For Everyone or Just Me?” (http://downforeveryoneorjustme.com/) Remember, to avoid tipping off the threat actor or engaging with them we don’t actually want to send traffic ourselves so this site will do it for us.
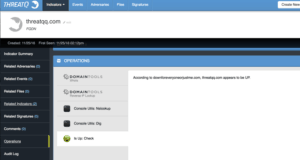
According to the IsUp Operation, the site is accessible. This could mean the adversary’s campaign has started and malicious content is being served to the targets. The next step of the investigation is to discover what kind of content the site is serving. Knowing whether it is delivering malware or just a simple fake page Phishing site is important. We don’t want to visit the site, so we will leverage a very valuable tool in Operations, the URLQuery (http://urlquery.net) sandbox. URLQuery will visit the site and run a comprehensive analysis on it for malicious content.
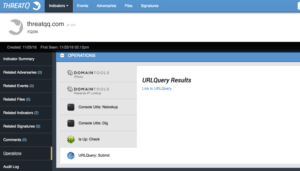
The URLQuery Operation submits the URL or FQDN to the URLQuery service and provides a link in return. With the information from URLQuery, we discover the site is serving up a malicious Microsoft Word document. From here we can retrieve the document and feed it to a malware sandbox to gain a deeper understanding of …. But I will cover that process and how to conclude the investigation in another post.
Conclusion
While this post may have been a little long, in actual time it only takes a few clicks to confirm if your organization or an employee is being used as part of a ricochet attack. The Operations feature speeds up an analyst’s workflow greatly by allowing them to stay in the same interface to conduct the entire spear phishing investigation. If a piece of your workflow is not available as an Operation, it is simple and quick to add your own.

0 Comments