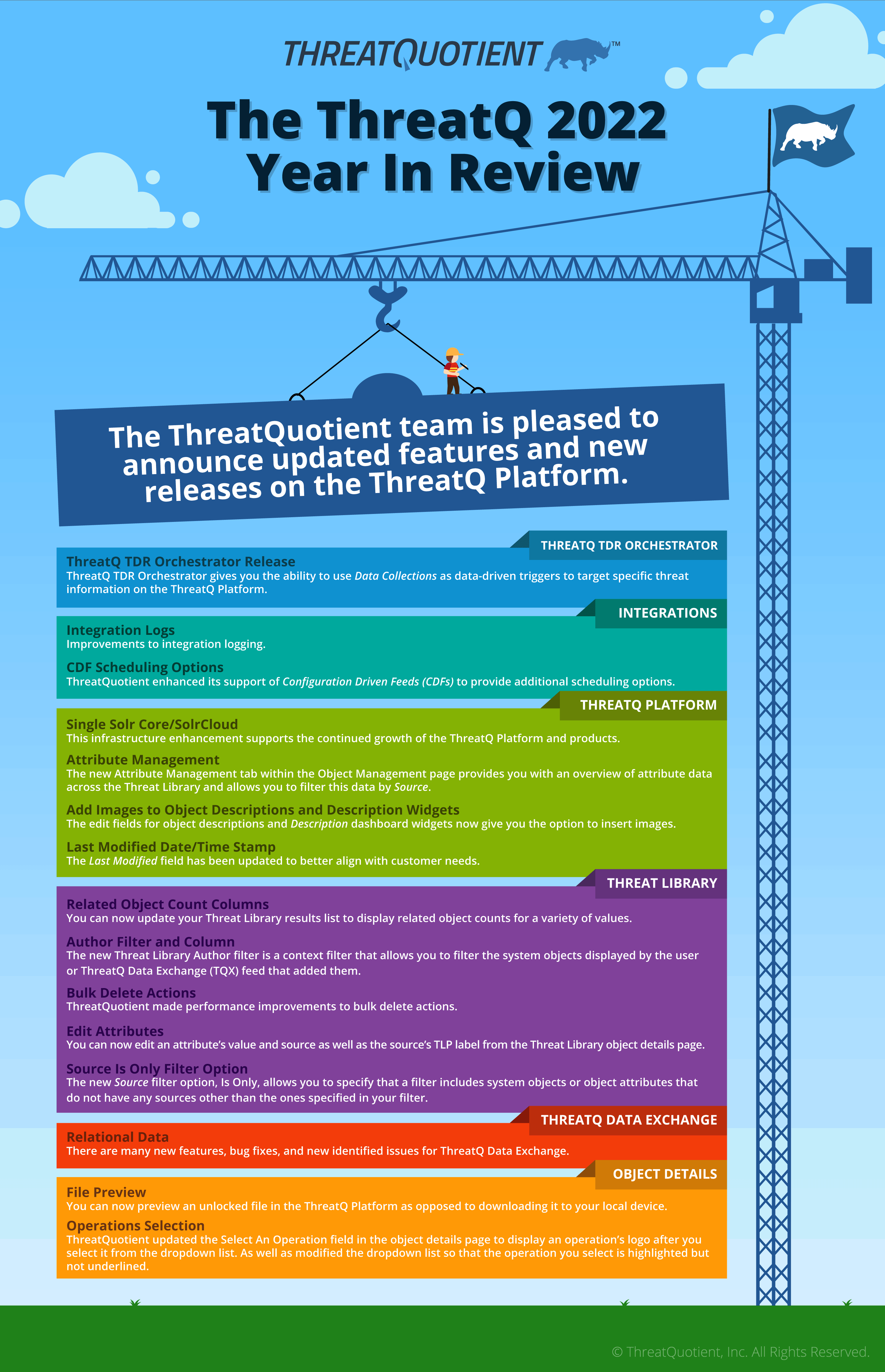
Is Cybersecurity Automation on Your List of New Year’s Resolutions? 6 Tips to Help
Leon WardEvery year, millions of people make New Year’s resolutions, both personally and professionally, and we all know how difficult resolutions can be to keep. One of the top workplace resolutions cybersecurity professionals are making this year is to pursue security automation initiatives.
In our 2022 State of Cybersecurity Automation Adoption report, 98% of the 750 senior cybersecurity professionals surveyed told us their organization has increased their automation budget with the objectives of improving cybersecurity efficiency and effectiveness, as well as helping to address the skills shortage and compliance demands. However, 97% are experiencing problems with their automation initiatives. The most common challenge is technology complexity, but lack of expertise and management buy-in are also preventing automation adoption.
Given these findings, chances are that some sort of security automation initiative is on your priority list for 2023. So, we’ve put together six tips to help you on the path to success.
- Prioritize interoperability. Standardize on a cybersecurity automation platform with an open versus closed architecture, such as the ThreatQ Platform, to ensure interoperability across the widest range of cybersecurity tools and extensibility. When disparate systems and sources that talk in different languages and use different formats can communicate, you can gain a comprehensive understanding of the threats you are facing and know what you must defend. This will also ensure you have the right foundation in place for working with emerging approaches such as extended detection and response (XDR).
- Remember context is king. Interoperability and a data-driven approach ensures automation is focused on relevant and high priority events. you can start to apply automation to a basic but high-value use case, such as contextualization of data, automatically augmenting and enriching internal data with threat data from the multiple sources you subscribe to – commercial, open source, government, industry, existing security vendors – as well as frameworks like MITRE ATT&CK. Combining and correlating internal and external data gives you context to understand what is relevant for your organization and enables further analysis and continuous improvement.
- Choose the right use cases. You can build on that contextualized data to expand your implementation of security automation, adding discrete tasks based on triggers and thresholds you set and defined by the use cases you select. Choose use cases that are proven to show value by saving time and/or improving the effectiveness of security procedures. Popular choices include threat intelligence management, incident response, phishing analysis, and vulnerability management.
- Adopt cybersecurity automation platforms with low- or no-code interfaces. Solutions that provide choice of no code through a simplistic playbook builder, as well as the option to code using standard formats like JSON or YAML for more advanced requirements help to simplify complexity and address skills shortages. We’ve built this level of flexibility into ThreatQ, allowing you to make automation accessible to a range of users with varying skill sets. When skills are not available or cannot be developed in-house, look to Managed Security Services Providers (MSSPs) or Managed Detection and Response (MDR) providers who place importance on cybersecurity automation to manage high volumes of data and alerts on behalf of customers and to leverage insights rapidly and effectively.
- Start with simple atomic-level tasks to automate and build from there. Choose a cybersecurity automation platform that offers an easy entry point and at the same time accounts for the full range of use cases and requirements as your program matures. Many ThreatQ users start with automating discrete actions that are executed directly or from a simple playbook, such as the creation of a ticket or an investigation based on certain event criteria or data-driven thresholds being met so that analysts can work more efficiently. When events are not obviously bad, workflows can be adjusted, and multistep play books can be created with decision logic built-in so that an analyst can review the event details and determine which series of actions to take that can be launched automatically.
- Gain management support by defining clear metrics and tracking progress. Automating time-consuming tasks drives measurable security gains. Using spear phishing as an example, quantitative metrics may include time to triage, attribute and protect against spear phishing attacks. However, automation is arguably an equally important benefit for employee well-being, reducing burnout and boredom and thus costly churn. So, balance the quantitative impact with qualitative factors including employee satisfaction and retention to assess the ROI of automation programs.
As you approach the challenge of securing your enterprise in an intense and complex threat and operational environment in 2023, we’d like to help. Schedule a live demo of the ThreatQ Platform now and see how you can incorporate automation into your security operations with confidence and demonstrate value quickly.

0 Comments