ThreatQ Cyber Forum Recap: Expert Insights on CTI Sharing in the Finance Industry
Celine GajnikAs the times change and the threats evolve, financial institutions face relentless cyber threats from an ever-expanding number and variety of attack vectors. While individual resilience is important, the heavily interconnected nature of today’s financial services industry demands a unified approach to defense where all participants actively engage in Cyber Threat Intelligence (CTI) sharing for the greater good.
In a recent ThreatQ Cyber Forum session, “The Evolution of Sharing CTI in the Finance Industry,” ThreatQuotient’s VP of Worldwide Sales, Gigi Schumm, moderated a panel discussion exploring how collaborative CTI can strengthen cyber resilience at the strategic, tactical, and operational levels. Experts included Rob Dartnall, CEO of SecAlliance, Rebecca Gibergues, Regional Director at FS-ISAC, and Yann Le Borgne, VP Threat Intelligence Engineering International at ThreatQuotient.
Live audience polling provided real-time insights into attendees’ current focus, benefits, and challenges with respect to CTI sharing.
Following are some key takeaways from their conversation. We encourage you to watch the session on demand for all the details.
Strategic Aspects of Threat Intel Sharing
The financial services industry is at the forefront of threat intelligence sharing, but what is shared, how it is shared, and for what purpose continues to evolve. Beyond sharing indicators so organizations can better defend themselves, other drivers now include compliance and strategic business objectives.
Threat intelligence sharing enhances the ability of financial institutions to comply with legislation including the General Data Protection Regulation (GDPR) and the Digital Operational Resilience Act (DORA), and rules and regulations from the Swiss Financial Market Supervisory Authority (FINMA) and the Saudi Arabian Monetary Authority (SAMA). It also helps to leverage threat intelligence-based frameworks like TIBER.
CTI sharing is also being used as a strategic tool by financial institutions as they look to expand into new markets or regions. Participating in information sharing networks with other organizations that have experience in those areas can provide valuable insights and enable enterprises to proactively put defenses – technologies and processes – in place to mitigate risk.
However, there’s a more fundamental strategic benefit to threat intel sharing: the herd immunity that results. Financial institutions’ supply chains and financial market infrastructures are interwoven, so sector resilience is a prerequisite for individual financial institution resilience. Expanding from machine-to-machine sharing of IoCs to community sharing that also includes best practices improves sector resilience.
Poll Results: When asked how confident they are in their organization’s current level of CTI sharing, 50% said they were somewhat confident, but a concerning 17% said they were very unconfident.
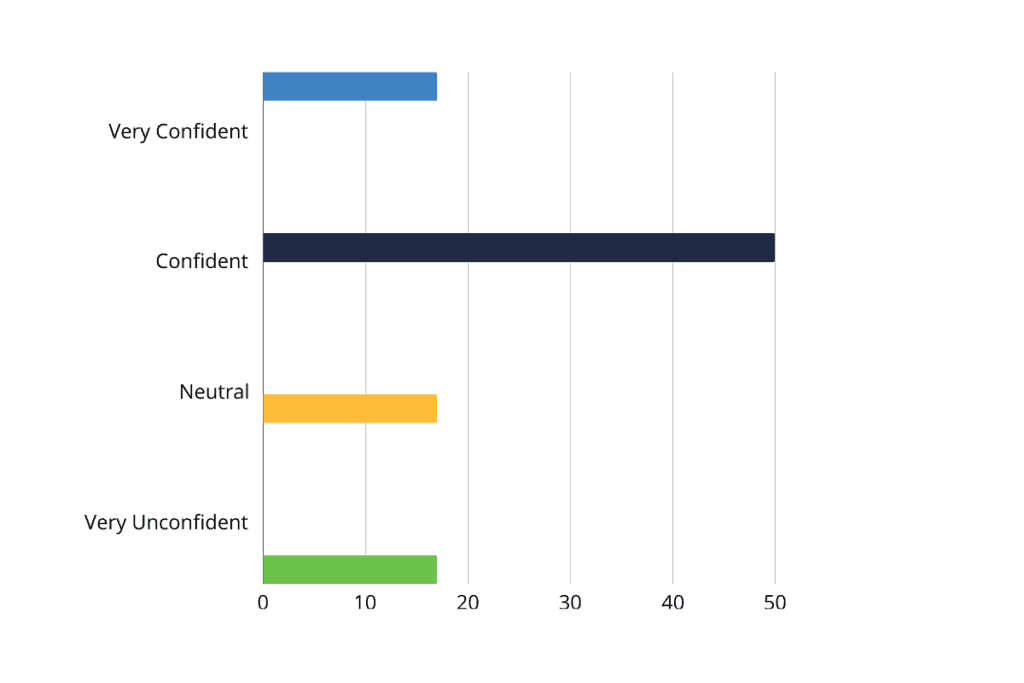
Poll Results: Confidence level in CTI sharing.
To help address strategic concerns around what to share with whom, breaking down communities into smaller groups of interest can lead to more fruitful discussions. Conversations around lessons learned for dealing with attacks, conducting assessments, and other best practices build trust and a multidirectional exchange of information and insights that helps raise maturity levels and improve collective defense.
Tactical Aspects
A lack of confidence in CTI sharing may also be a result of tactical challenges. Taking a closer look at the tactical aspects of intelligence sharing, specifically the how and what, our experts shared advice, including:
- There has been a substantial movement towards integration to enable machine-to-machine sharing including compatibility with standards like STIX/TAXII and normalization of the CTI itself. These advances are helping to make data sharing easier.
- Context makes threat intelligence relevant. So, organizations should focus on threat intelligence tools and platforms with built-in automation capabilities that look for the signal and strip out the noise.
- Trust is a key component of sharing and FS-ISAC and SecAlliance have extensive experience in leveraging technology and processes to help build trust within sharing communities. For example, rules around the classification and use of intelligence, the traffic light protocol, provide trusted and well-established ground rules for the exchange of intelligence. Additionally, the ability to anonymize sensitive, organization-specific data helps reduce tactical barriers to compliance challenges and further fosters sharing.
- Private initiatives like the sharing community ThreatQuotient recently announced are gaining traction. The ThreatQ Community already includes over 100 fully vetted members who are contributing to crowdsourced security intelligence. Once admitted, participants have the option to access intelligence as well as upload contributions that are analyzed and anonymized before being shared to maintain the privacy of those involved.
Operational Aspects
Poll results: When asked which types of threat intel sharing they believe are most beneficial for the financial industry, 80% of the audience said a combination of communities of interest, private initiatives, and public initiatives provides the most value.
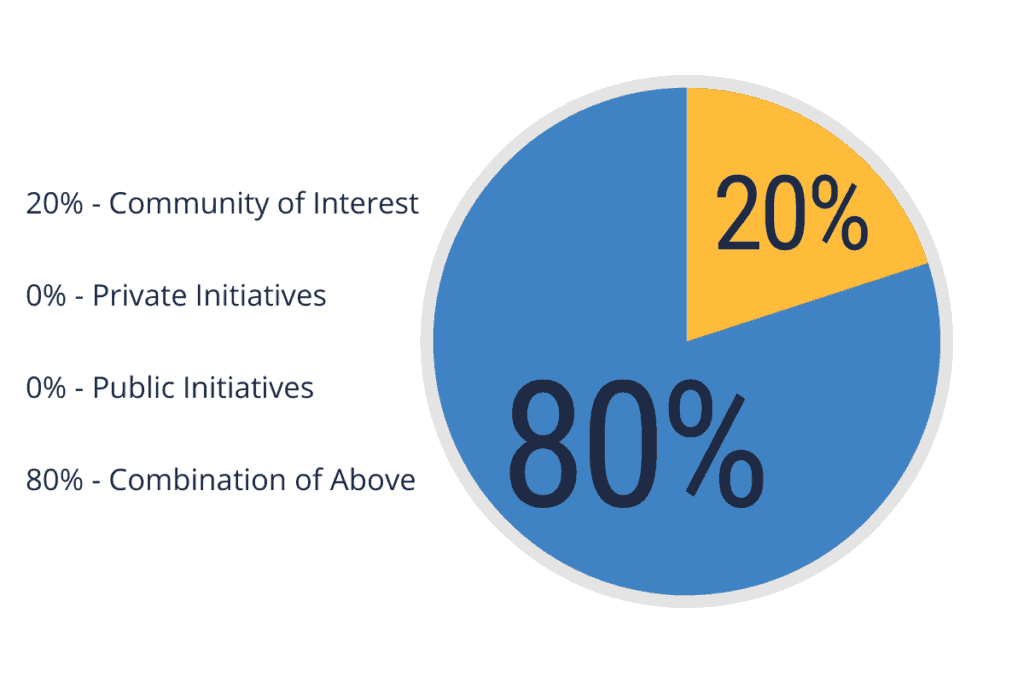
Poll Results: Which types of threat intel sharing respondents believe are most beneficial for the financial industry.
With so many sources of threat intelligence, some of which may be conflicting, how do organizations make the most of it and operationalize it? Our experts recommend the following:
- With respect to consuming threat intelligence, identify your priority intelligence requirements: what do you really need to know and the format you need to use it effectively. Then, grade the source based on criteria including quality and accuracy. Consider only those with high scores and put the others aside and revisit them later as sources do evolve over time.
- Sharing is a two-way exchange. So, before adding a new source, organizations also need to think about what they want to share and with whom. In today’s legal and competitive environment, be sure to think about what to share in the event of a breach and what level of context you can and should provide. Setup processes internally first before you put operational resources (people and tools) behind the new source.
Final Remarks
Poll results: When asked about their organization’s primary focus when sharing threat intel, answers were evenly split between technical details (33%), contextual information (33%), and a balanced mix of both (33%).
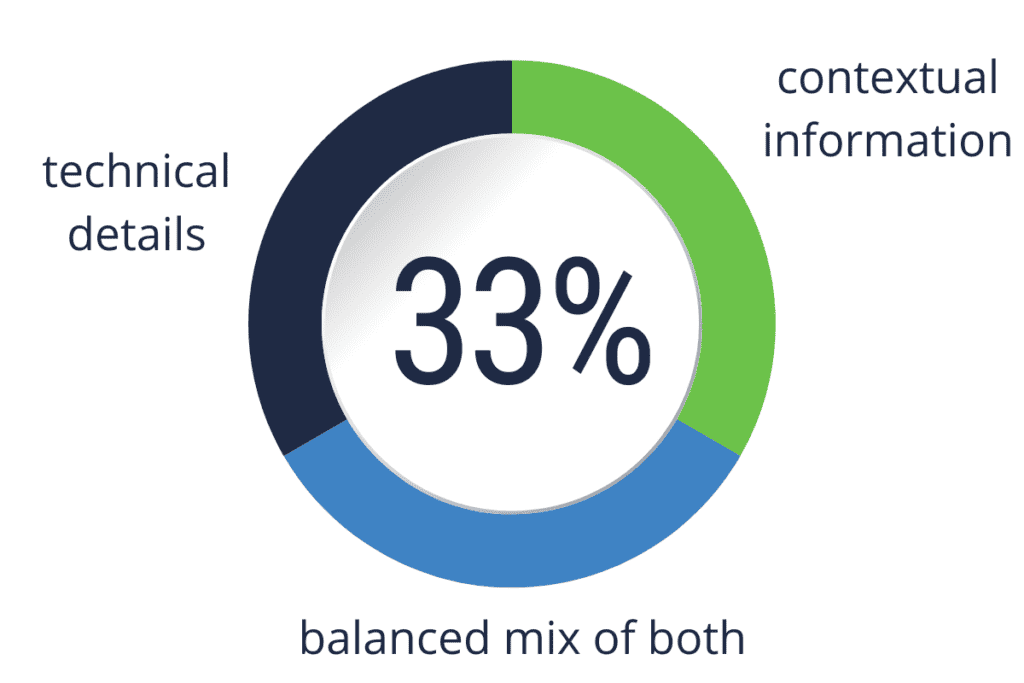
Poll results: Respondents reveal their organization’s primary focus in sharing threat intel.
We can all agree that sharing remains foundational to strengthening the financial services sector’s defenses, but clearly there are challenges that get in the way. Processes, policies, and tools are great, but people are essential. These experts can serve as a great resource to help you continue to mature your level of community sharing in a way that meets your requirements and advances the greater good.
Watch the session for more insights and to better understand how they can help.

0 Comments