Know More about the Impact of the SolarWinds Breach on your Environment with ThreatQ
ROSS HAMMERWith the recent compromise announcement from SolarWinds and FireEye, a lot of information and preventative measures have been provided to, and by, the security community. As information continues to come in from a variety of sources, security teams around the globe are trying to answer the following questions for themselves and their executives – What do we know about the compromise? Were we impacted? If so, what do we do now? If not, how do we protect ourselves going forward?
ThreatQ Threat Intelligence Engineers have been helping our customers answer these questions by advising them on how to use available information to build a foundation of knowledge that goes beyond Indicators of Compromise (IOCs). From the initial report from FireEye, they can parse out the information that includes Mitre ATT&CK techniques, IOCs, Yara rules, and Snort signatures to organize and build relationships with additional information as it comes in. Additionally, it’s important to understand the appropriate context of the available information. Given an organization’s environment, technology stack, network architecture, and risk profile, what is the most relevant and the highest priority information that should be leveraged for better protection?
This is an excellent example of the collaborative nature of the ThreatQ Platform. Many different individuals or teams can bring information from various sources into the Threat Library and build out a “what do we know” framework that benefits others within the security organization. Considering the context of the information and assigning a priority on the IOCs makes the information actionable so that it can be used proactively for threat hunting and to strengthen defenses, or reactively for detection and response. This is possible because the information brought into the platform includes not only IOC’s but attack patterns, reports that are both internal and external, malware association, tools leveraged, etc. and provides relationships between the different objects within ThreatQ. This information can be filtered and sorted to create collections that can be leveraged in a variety of ways. Below is just one example:
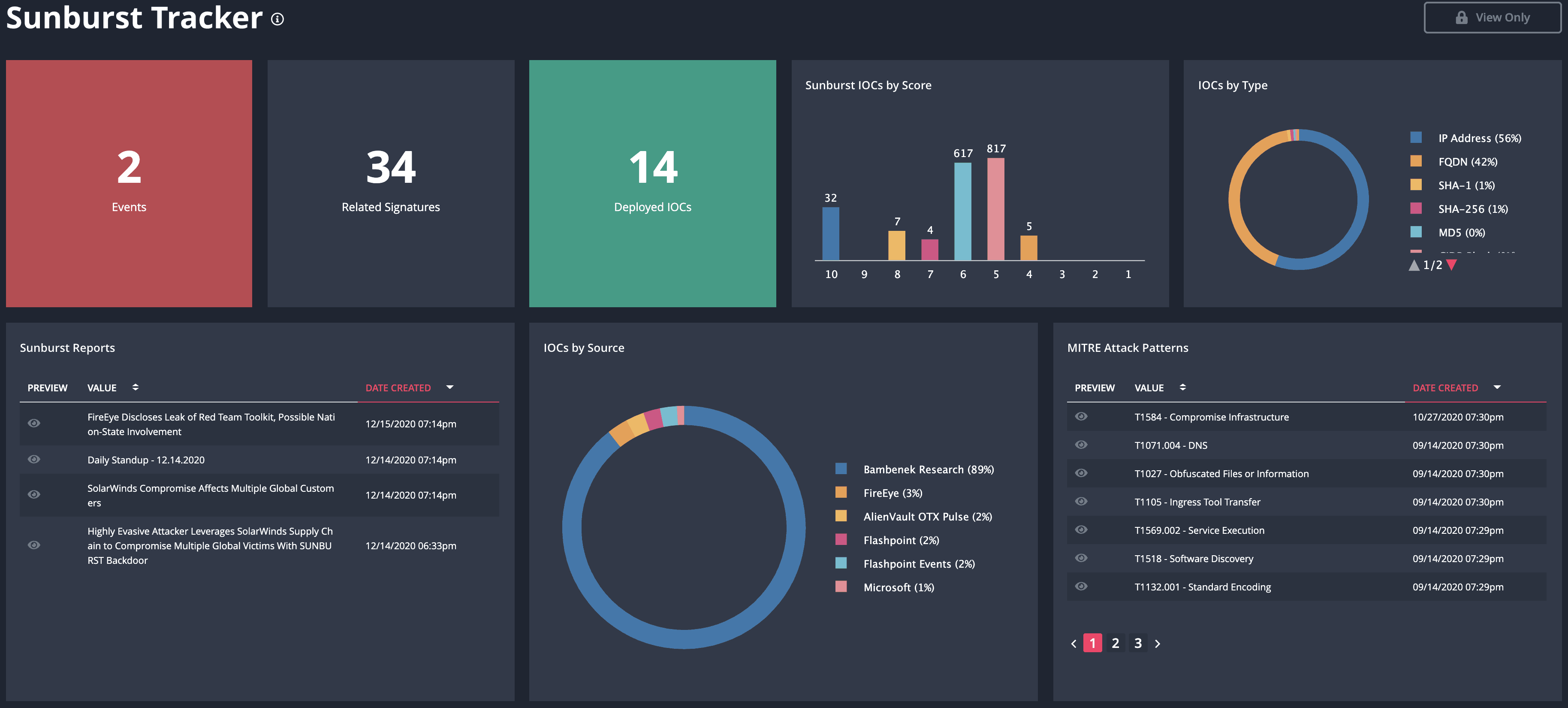
Solarwinds Sunburst Hack Tracker Dashboard Example
Not only can you bring in this information from a multitude of sources, but because of the ThreatQ Open Exchange, you can export this information to a variety of security tools within your organization (firewalls, IPS/IDS, routers, web and email security, EDR, etc). Additionally, you can export this information externally from your organization. This can be done through sharing platforms like a MISP, but also between ThreatQ systems to provide relationships of not just IOCs, but related malware, threat actors, and shareable analysis reports. This integration and information sharing is very useful for service providers charged with protecting other organizations or large organizations with multiple business units, each with their own security teams.
ThreatQ provides a location for security teams to aggregate and distribute information they have learned and collected. The collected information could include blog posts or GitHub repositories; linking IOCs, malware, or threat actors with the aim of creating a “what do we know” report for executive leadership. The same information will be available for analysts to reference or make decisions on and indicators can be distributed directly to systems your teams already know and use. For example, the IR team uses forensics and case management tools. The malware team uses sandboxes. The SOC uses the SIEM. The network team uses network monitoring tools and firewalls. The endpoint team uses EDR tools. Analysts can also add reports and information from the work they are conducting and instantaneously share the latest information with other teams.
With knowledge that is continuously updated with new data and context, teams can stay focused on priorities, deal with an incident faster, and make more informed decisions. From tactical intelligence that can be used to create block lists or deploy signatures, operational intelligence on what techniques are used and what to be on the lookout for such as tools, to strategic intelligence for identifying possible threat actors and what they are after. When news of a widespread compromise breaks, the ThreatQ Platform helps understand and focus on what’s relevant to your organization, and operationalize that intelligence quickly to strengthen security posture.

0 Comments