Act on Security Reports in Just a Few Clicks
POSTED BY MIKE CLARKEvery day, security reports or bulletins are released by intelligence providers, researchers and other organizations. Most often these reports come in PDFs or other formats that are not machine readable, resulting in a time-consuming process for cyber security professionals as they try to use all of this incoming information. The normal process goes something like this: Read the report, extract indicators of interest, log into your SIEM, and run ‘rear-view mirror’ queries on those indicators. Of course, this process will vary slightly across different organizations and analysts.
The ThreatQ threat intelligence platform makes this process much quicker by consolidating the workflow into a single tool. Not only can these reports be ingested and indicators extracted by simply dragging and dropping the file, but you can then search your SIEMs with a single click. This search can be run against a single SIEM, or better yet, multiple technologies at the same time. This functionality is especially useful for organizations that have to support multiple different SIEMs, such as MSSPs.
For our example, we will use a report from DHS which came out recently, entitled “Intrusions Affect Multiple Victims Across Multiple Sectors.” They provide their data in multiple formats but we will use their STIX file.
Import
Ingesting the STIX file is as easy as dragging the file into the import window and selecting the STIX parser.
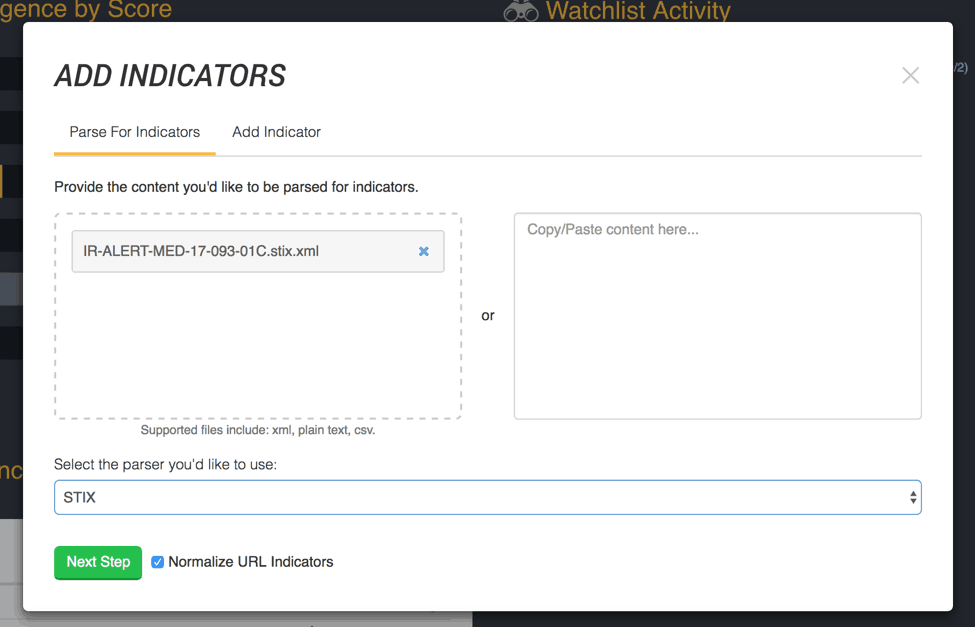
Figure 1: Import a STIX file
Once we complete the import process, the file is automatically saved in the Threat Library along with all of the indicators related to it.
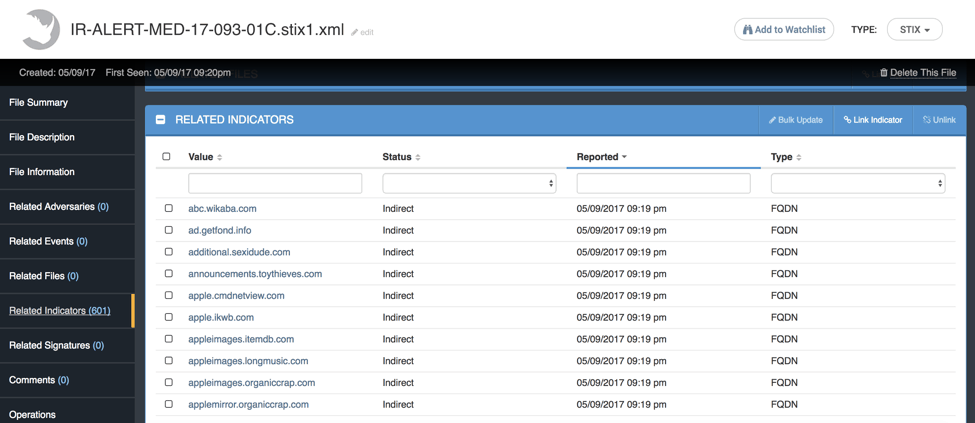
Figure 2: The indicators which are parsed are then related of the file
Over 600 indicators were extracted from the report. Here is where the real fun begins. Let’s say we support two different SIEMs in our environment: Splunk and QRadar. As an analyst supporting several customers, I need to check both SIEMs for any of the indicators seen in the report. With the ThreatQ threat intelligence platform RearView Operation I can do this with a single click.
RearView
First, let’s install the Operation. All you do is drag the Operation file into the window and ThreatQ take care of the rest. These Operations are simple Python scripts and can be created by anyone, not just the ThreatQ threat intelligence platform.
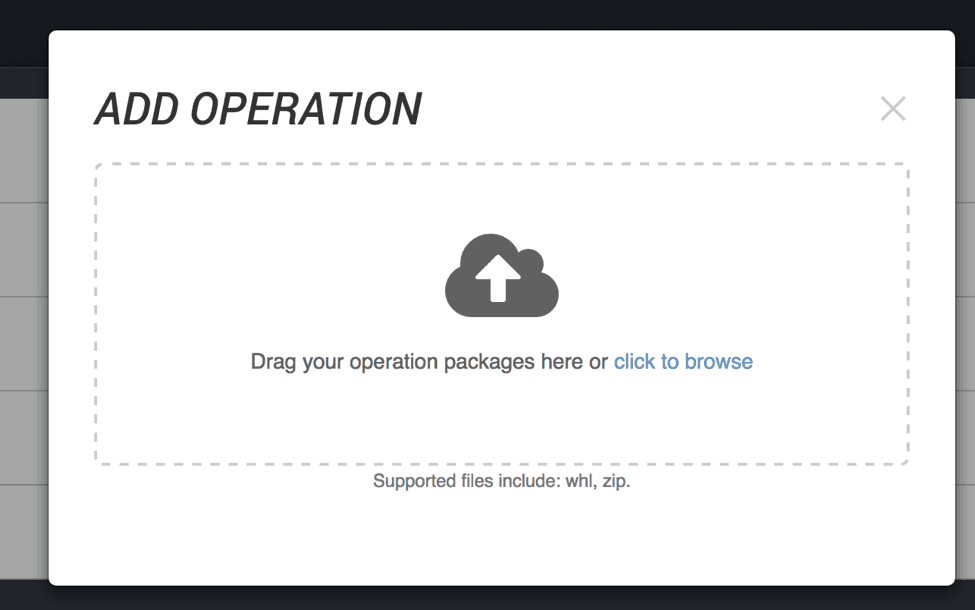
Figure 3: Just drag and drop an Operation to have it installed
Once added, the Operations configuration screen is brought up. This RearView Operation actually leverages two other Operations: Splunk Search and QRadar Search. So in this configuration we are just going to tell it to use those. It is configurable, so if you are an HP ArcSight ESM user or a McAfee Nitro user it can search either, both or ALL of those.
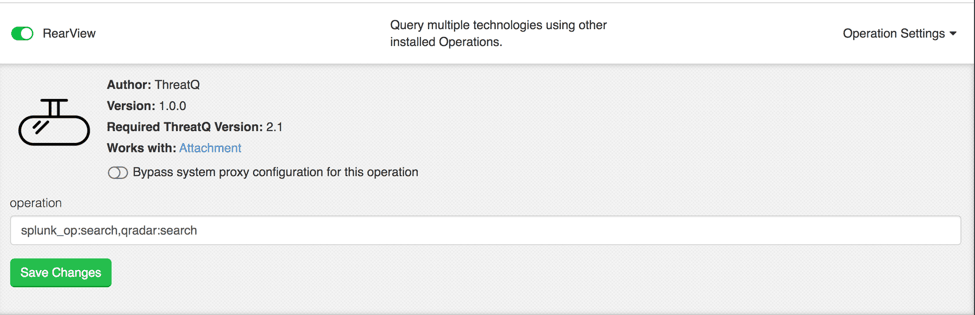
Figure 4: RearView Operation Configuration
As you can see above, this Operation works with Attachments. If we go back to the STIX file we imported we can now see it in the Operations list. Click on it and ThreatQ will reach out to your pre-configured SIEMs and query for each indicator related to this file. Click again and the Operation will respond with links to the Indicators it saw.
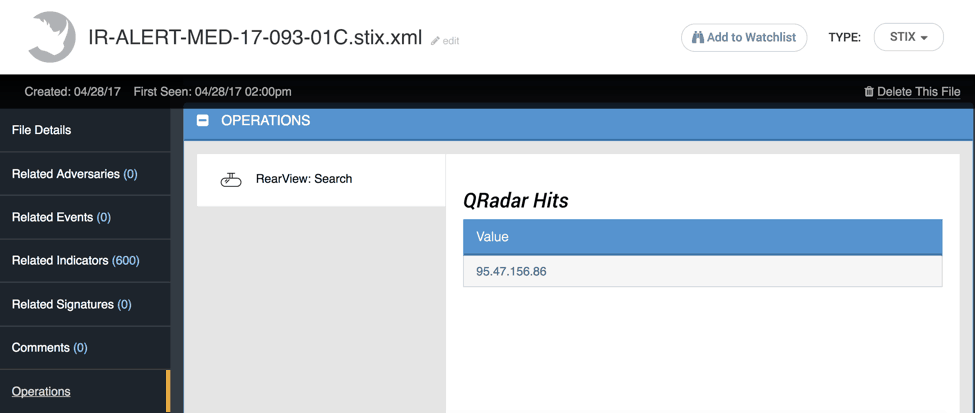
Figure 5: Results of the RearView Operation
Looks like one of the IP Addresses in the report was seen in QRadar, however, Splunk came up clean. Let’s drill down into the Indicator and grab the logs for this IP specifically.
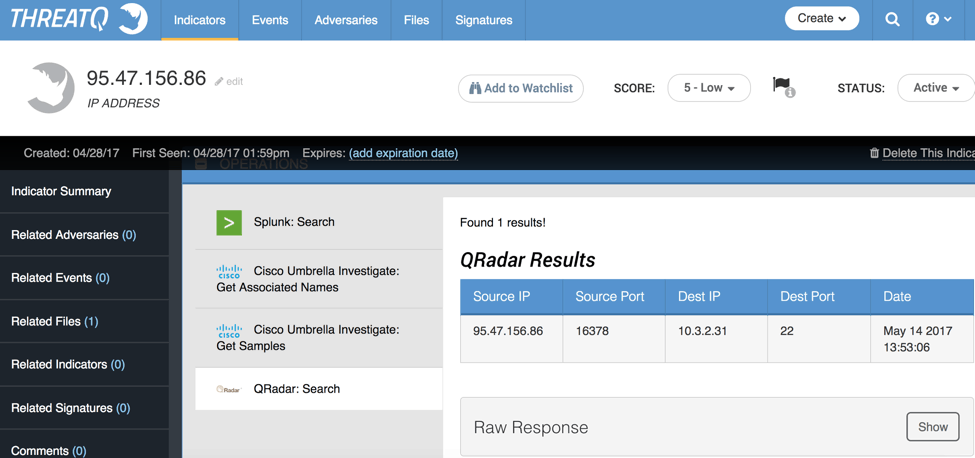
Figure 6: Results of the QRadar Operation
Looks like there was a successful connection to a SSH service on our network. This is certainly something we will want to investigate further.
As you can see, with the ThreatQ threat intelligence platform and RearView Operation, we took a rather large report full of Indicators and in just a few clicks checked our security infrastructure – including 2 different SIEM technologies — for any signs of them.. ThreatQ makes it possible for analysts to quickly and easily make use of security reports and let stakeholders know if and how they are affected by them.

0 Comments