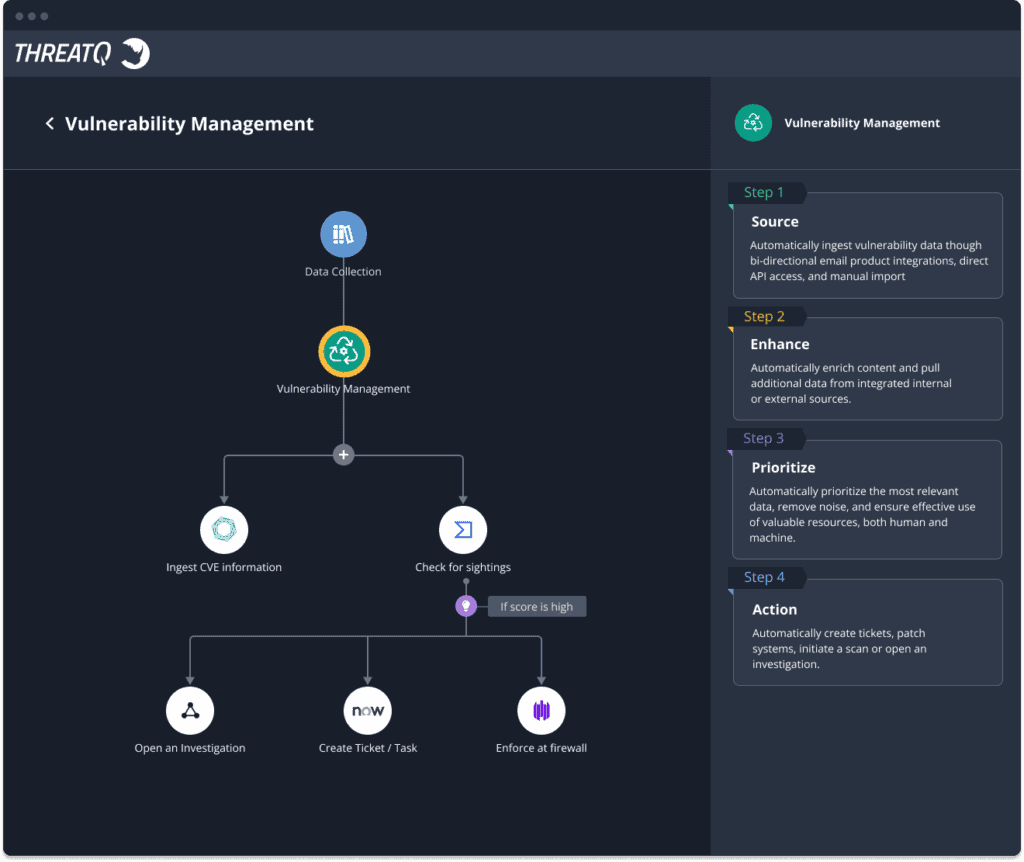
Vulnerability Management & Prioritization
What is vulnerability management?
Vulnerability management and prioritization involve the systematic identification, assessment, and mitigation of weaknesses or vulnerabilities in an organization’s systems, applications, and networks. This process includes scanning and monitoring for vulnerabilities, assessing their severity and potential impact, and prioritizing remediation efforts based on factors such as exploitability, criticality, and exposure. By prioritizing vulnerabilities based on risk and business impact, organizations can focus their resources and efforts on addressing the most critical threats first, thereby reducing the likelihood of successful cyber attacks and minimizing potential damage to their assets and operations.
The challenge:
It is simply impossible to patch and mitigate every software vulnerability present in an enterprise network. Historically, organizations would prioritize mitigation based on limited and inward-facing data:
- Server versus workstation
- Employee role
- Asset criticality
- Vulnerability score
- Patch availability
Despite this level of prioritization, patching remains one of the most time-consuming vulnerability management tasks. This approach also has limited effectiveness because it does not take into account knowledge of how that vulnerability is actively being exploited in the wild, and the risks associated by those adversaries leveraging it to a company’s specific environment.
Automate vulnerability management with ThreatQ TDR Orchestrator
The ThreatQuotient data-driven threat intelligence platform helps to balance between human & machine focused approaches ensuring that teams always have the best tool for the job.
Learn more about ThreatQ TDR Orchestrator, the industry’s first solution to introduce a simplified, data-driven approach for no code/low code automation of the visibility and prioritization needed to remediate the most critical vulnerabilities first.
How ThreatQ meets the vulnerability management challenge
| 1 | Connect to disparate systems and sources |
|---|---|
| 2 | Ingest and aggregate external and internal data to visualize the threat related to the vulnerability |
| 3 | Normalize and correlate threat data with internal vulnerability scanning data |
| 4 | Curate and analyze data for decision making and action |
| 5 | Prioritize vulnerabilities for remediation |
| 6 | Export a prioritized data flow across the infrastructure translated for improved threat detection, investigation and response |
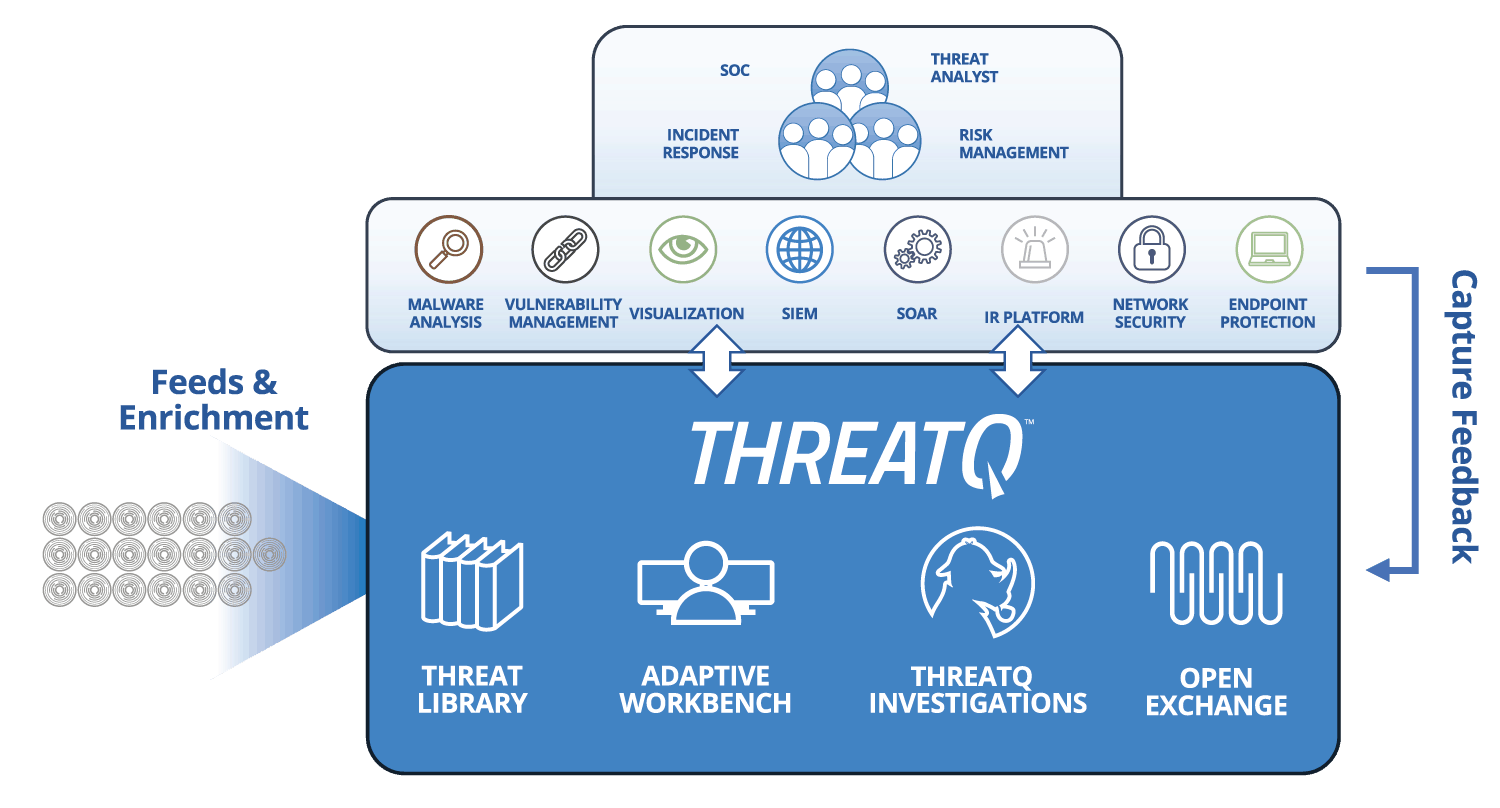
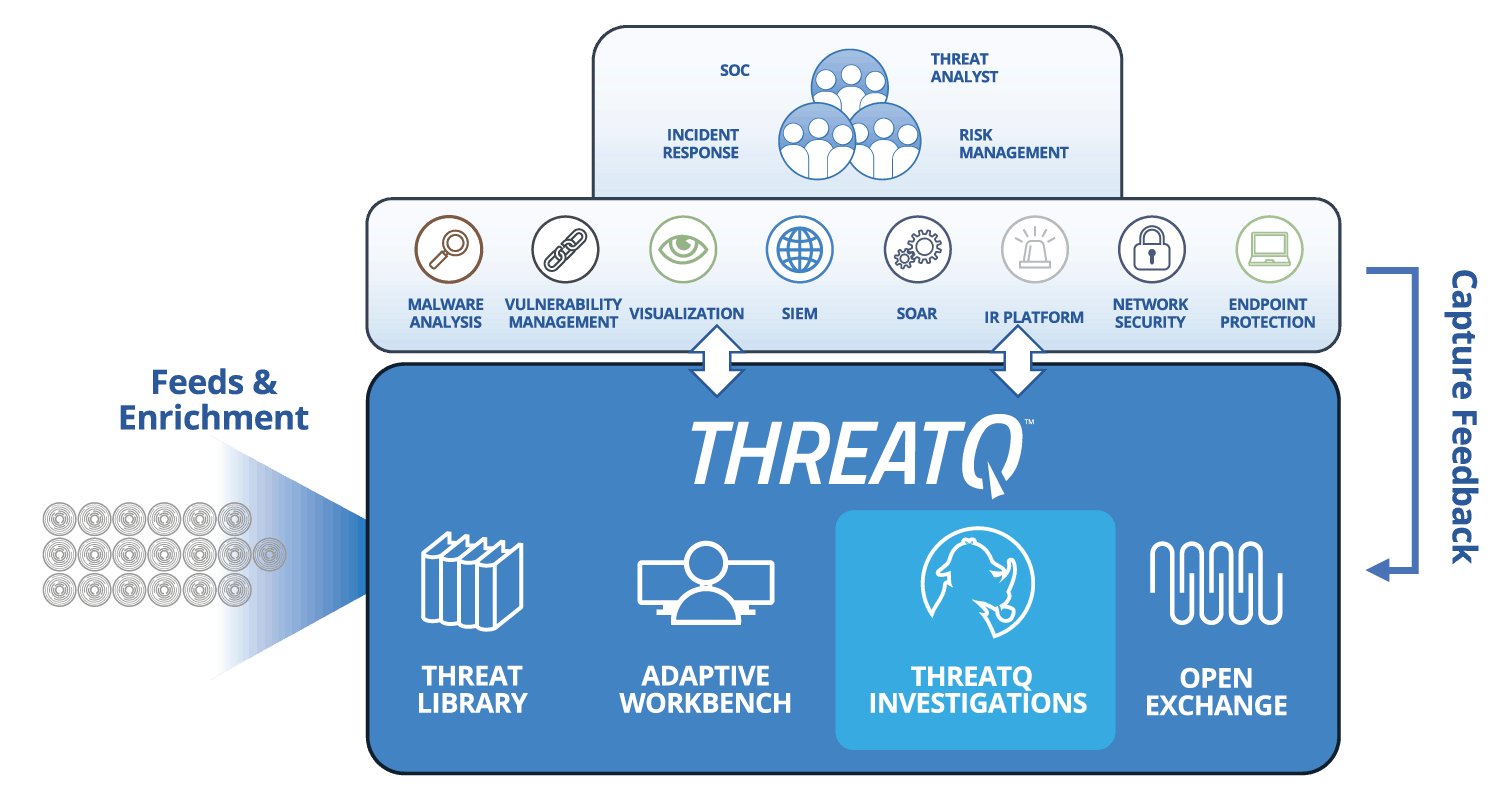

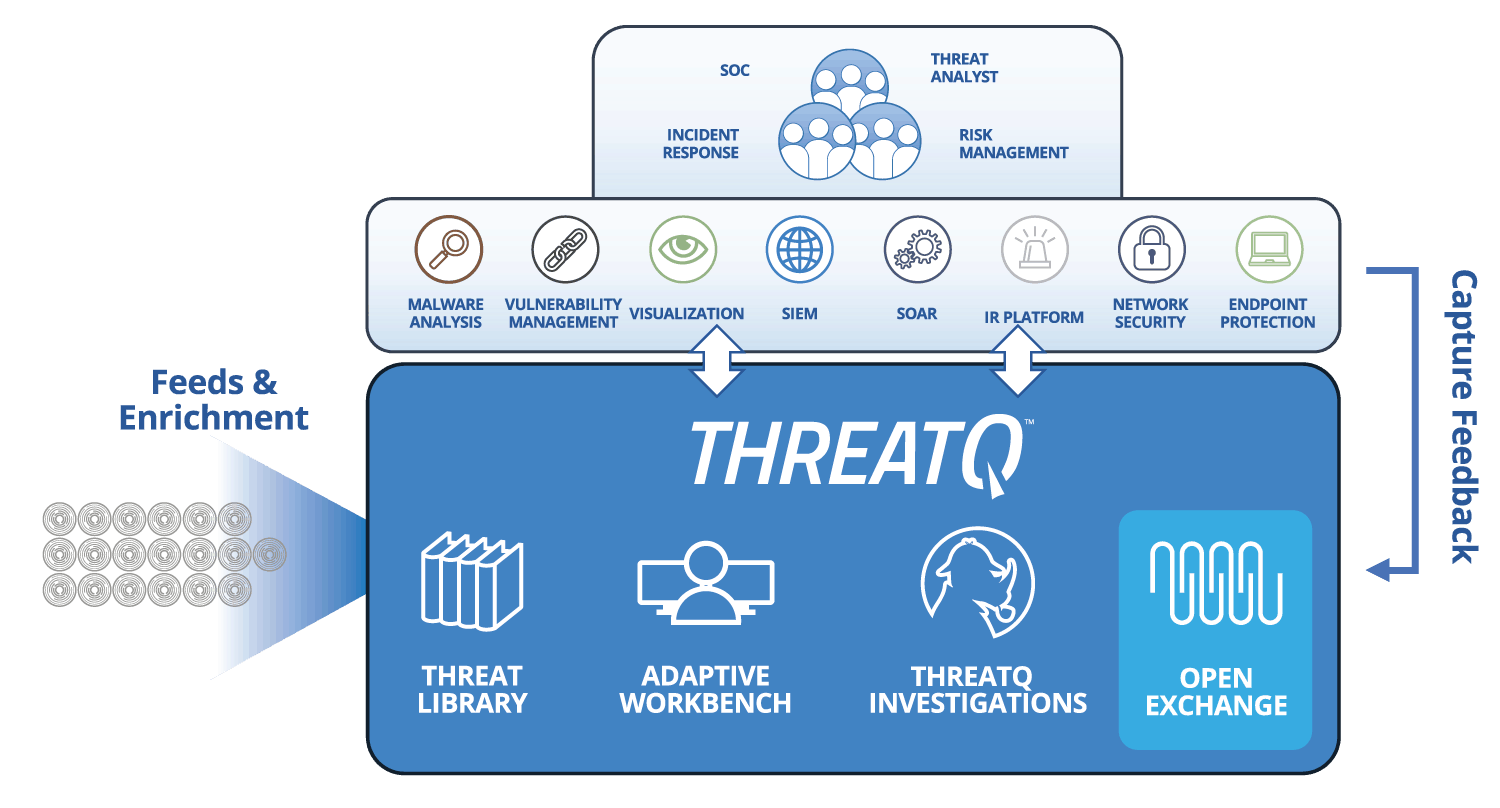
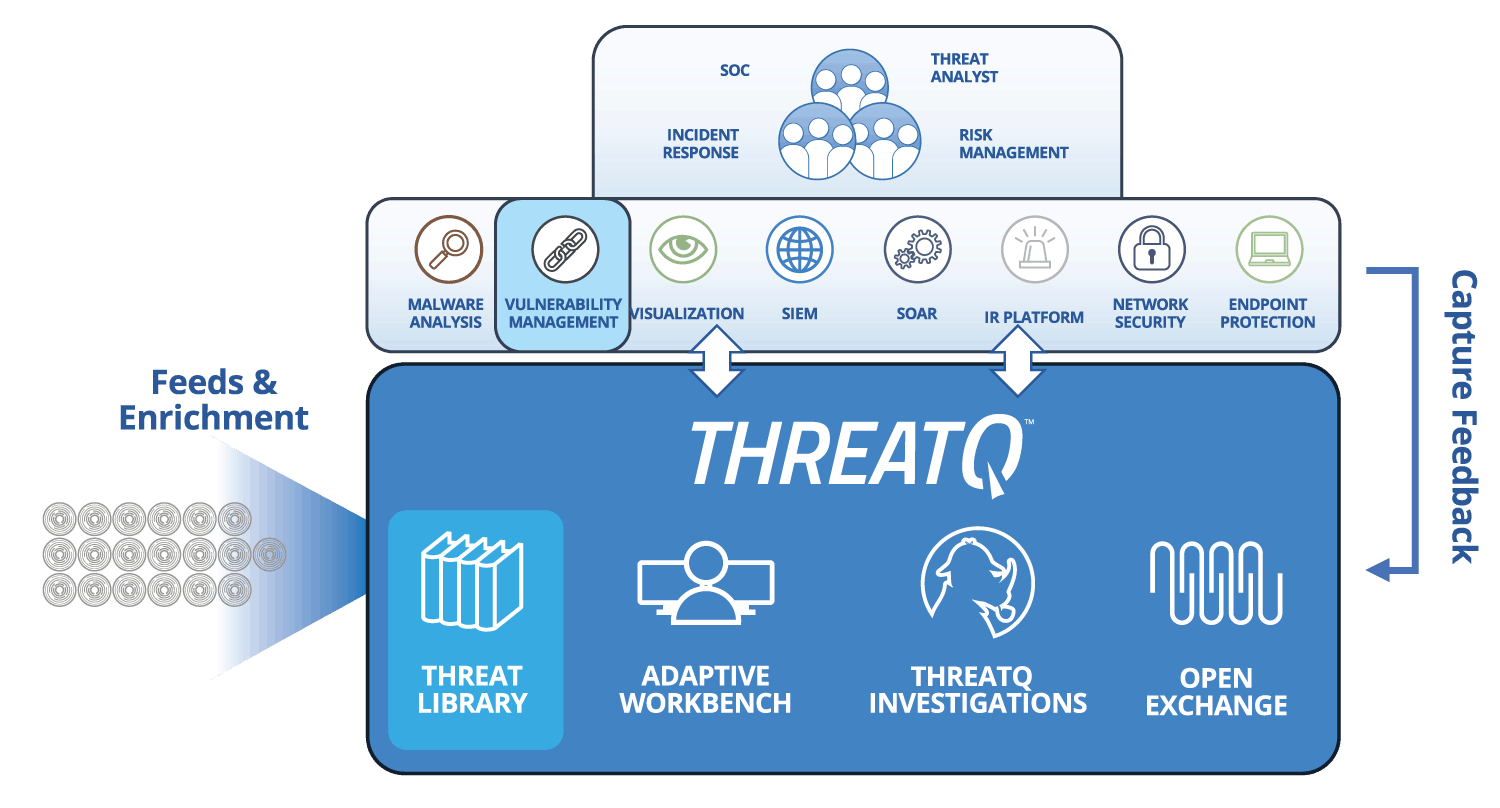

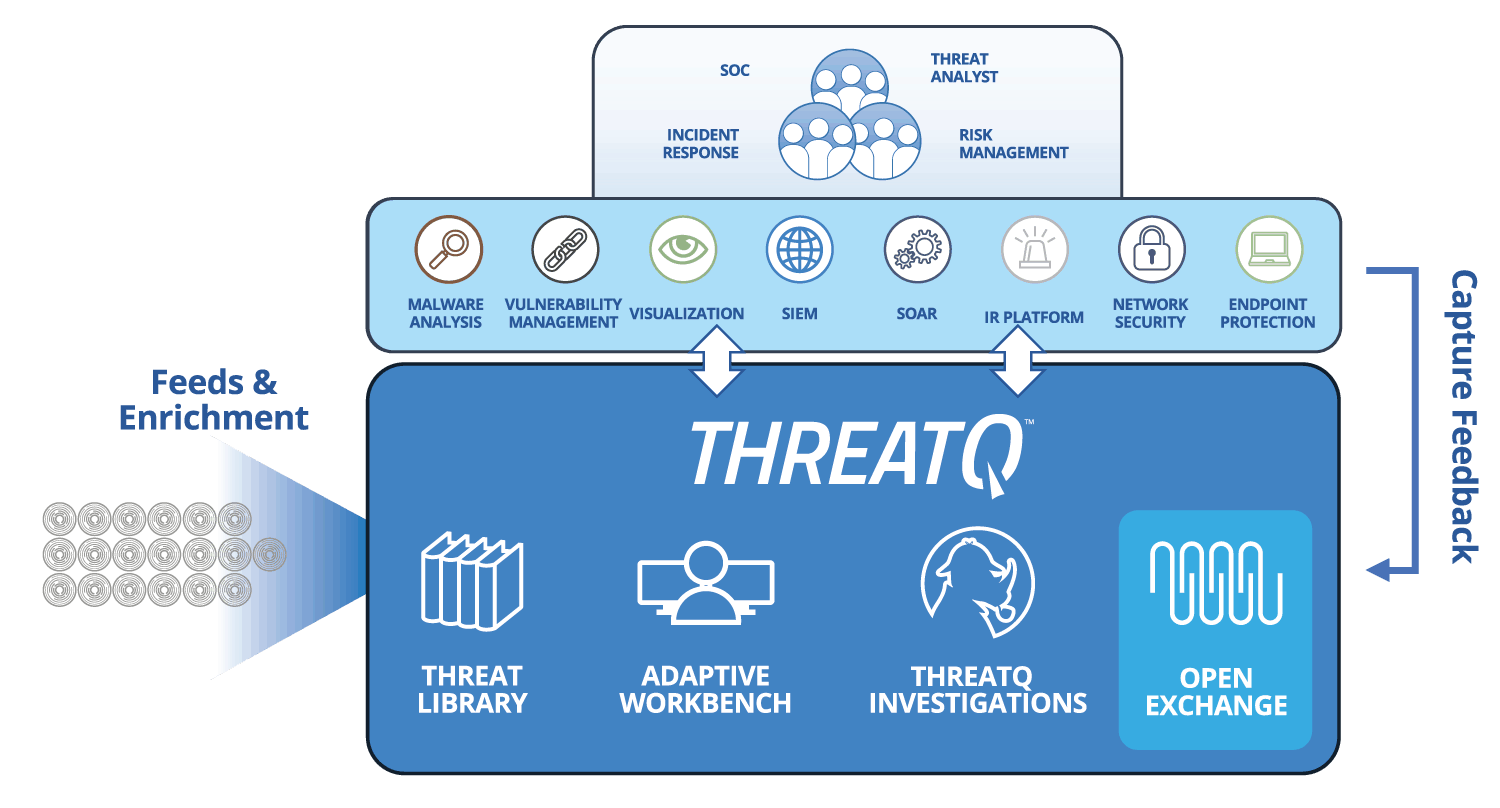

| Threat Data Aggregation | Create a single source of truth based on correlated, normalized and de-duplicated intelligence data and events across all tools and sources. Learn more > |
|---|---|
| Threat Library™ | Store global and local threat data in a central repository to provide relevant and contextual intelligence that is customized and prioritized for your unique environment. Learn more > |
| Open Exchange™ | Integrate ThreatQ with existing security tools, teams and workflows through standard interfaces to extend their value, knowledge and efficacy. Learn more > |
| Dynamic Scoring | Prioritize threat data automatically, understand why it is relevant and take action faster and with greater confidence. Learn more > |
Learn how ThreatQ can help with
vulnerability management
Take a quick look at vulnerability management using ThreatQ.
If you like what you see, schedule a demo for a deeper dive.
Our approach to vulnerability management
A vulnerability is only as bad as the threat exploiting it and the impact on the organization. Security teams must take a risk-based approach to prioritizing vulnerabilities with knowledge about how vulnerabilities are being exploited.
ThreatQ allows security teams to focus their vulnerability management resources where the risk is greatest through the following three steps:
- Understand the threats and which vulnerabilities threat actors are leveraging to determine relevance to the organization’s environment and prioritize which vulnerabilities to address first. For example, a vulnerability related to a specific adversary campaign and IOCs that have been seen in an organization’s SIEM and/or ticketing system should be addressed immediately. A vulnerability that has related threats and IOCs but they have not been known to target the organization’s specific industry should be watched but is a lower priority. A vulnerability with no known adversaries using it or associated IOCs may indicate it is not being exploited in the real world yet, and can be deprioritized for now.
- Overlap adversaries that target the company with CVEs the adversaries use, historical victimology targets and vulnerability scan results for those targets to create a superior risk profile.
- Reassess and re-prioritize on a continuous and ongoing basis as adversaries change tactics, techniques and procedures (TTPs), systems and applications evolve, and their usage within the organization’s environment does as well.
Outcomes:
- Better situational awareness of attackers, their motivations and one’s own environment.
- Clear priorities on what actions to take first to address which vulnerabilities.
- Ability to focus on the vulnerabilities that are the most relevant based on the organization’s risk profile.
- A superior risk profile based on deeper insights into adversaries, their tactics, techniques and procedures (TTPs) and relevance to the organization.
- Better investment and resource decisions.
LET’S GET STARTED!
Join the ThreatQ Community, a private group with hundreds of experienced cybersecurity pros sharing intel to level-up threat detection and response. Partner with ThreatQuotient to learn how we can help you focus on the threat!