Behind the Mystery Nation
POSTED BY NIR YOSHANorth Korea Hackers and the Bangladesh Bank Robbery
Have you ever seen a satellite image shows North Korea compared to its neighbors when pieced together? North Korea is so secretive you can’t even see it from space!

NASA Satellite Image
Just like North Korean leader Kim Jong-un, the North Korea hackers are aiming their attacks against its adversaries in the West.
In this blog I will get into the indicators of compromise associated with about the SWIFT attack of the Bangladesh Bank. Kim Jong-un’s hackers got away with $81 million in that heist.
This was just another incident in what I call a “series of unfortunate events” including:
- Attack in the Philippines in October 2015
- Attack Tien Phong Bank in Vietnam in December 2015
- Attack on Bangladesh Bank in February 2016
Researchers believe it is the first time a state had used a cyberattack not for espionage or war, but to finance the country’s operations. North Korean hackers’ fingerprints showed up in a series of attempted attacks on so-called cryptocurrency exchanges in South Korea, and were successful in at least one case, according to researchers at FireEye.
Let us review step by step the Bangladesh Bank attack and expose relevant indicators and tactics to help protect from similar attacks.
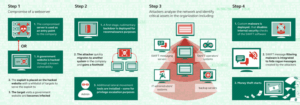
SECURELIST, Lazarus Under the Hood
Watering hole
The attackers compromised the legitimate sites sap.misapor[.]ch and eye-watch[.]in. Some hashes of the backdoor have been provided after technical analysis:
85d316590edfb4212049c4490db08c4b
c1364bbf63b3617b25b58209e4529d8c
1bfbc0c9e0d9ceb5c3f4f6ced6bcfeae
Malware and C2
The malware variant, found in the Bangladesh Bank incident, has been seen as part of North Korea’s campaigns in other cases over the past year.
Once the data is decrypted with two RC4 rounds, the dropper checks the decrypted data contains a valid 4-byte signature:
0xBC0F1DAD
When analysing the malware it shows connectivity to the following C2 IP addresses:
125.214.195.17
196.29.166.218
Lateral movement
After the initial breach the attackers pivoted from infected hosts and emerged to migrate to a safer place for persistence. A backup server was chosen as the target host. Techniques used for that purpose were:
Privilege escalation
Scheduled tasks
Execution
One of the central hosts in the bank, which was running SWIFT Alliance software, contained a fully-fledged backdoor with the following MD5:
2ef2703cfc9f6858ad9527588198b1b6
The platform hardcoded the bank’s SWIFT resources into a malware program that successfully sent fraudulent SWIFT messages. To avoid detection, attackers learned that bank protocol involved printing SWIFT messages for review. Therefore, the malware program was designed to hide fraudulent messages from digital logs and delete them from printed lists of transfers. Techniques used for that purpose were:
Command-Line Interface
Execution through API
As you can see, all the steps above involve tactics, technique, procedures (TTPs) and indicators of compromise (IOCs). ThreatQ threat intelligence platform helps threat intelligence analysts enrich and expand the above, which is only a piece of the big picture.
In the case of the SWIFT compromise, various leading security research organizations and law enforcement agencies joined forces to investigate and stop the attack. But this example does reinforce the value of IoCs in pointing to malicious behavior. Your system logs are full of IoCs. With a threat intelligence platform like ThreatQ you can tie IoCs together and make sense of all the output from all your different security tools to build a bigger picture. You can use external global threat intelligence sources to pivot to TTPs and the adversaries themselves to gather more conclusive evidence that your organization has been compromised. And with a deeper understanding of the methods the adversary employs, you can stop malicious activity more quickly and prevent similar attacks in the future.
After hackers stole $81 million from the Bangladesh Central Bank via SWIFT in 2016, SWIFT the SWIFT Customer Security Controls Framework went into effect January 1, 2018 requiring all 11,000 SWIFT member banks in more than 200 countries to comply with 16 mandatory controls – including multifactor authentication, and continuous monitoring – or face regulatory and economic consequences.
Nevertheless, while writing this blog I got a news notification on yet another hack stealing $6M from Russian central bank via SWIFT system.
North Korea has reportedly set up a 6,000-strong hacking unit and is strongly suspected of being behind a number of cyberattacks on South Korean banks, media companies and infrastructure, including nuclear power plants, in recent years.
The world once laughed at North Korean cyberpower. No more.

0 Comments