It’s beginning to look a lot like Phishing Season
POSTED BY NEAL HUMPHREYAs I awoke this morning and my security-based paranoid brain kicked in after some coffee, I realized that Thanksgiving is in just a couple of days. Added to that realization is the amount of holiday decorations already out at stores. Rather than bemoan the lack of celebration we currently have for the family holiday of Thanksgiving, what came to my addled mind was: “It’s that time of the year to talk with the wife and extended family about opening tracking emails again.”
That’s right. It’s almost Package Tracking Phishing Season!

So, it’s time to crank up those employee education campaigns. Get them thinking before they click – as best you can.
But despite our best efforts, we know that people are still going to get hit, because it’s simple: People are going to make mistakes. It’s the first rule in security and it’s the reason that spear phishing is so effective.
With that being said, let’s talk a bit about how we are dealing with our security reality.
To me, security today has been impacted by:

SQUIRRELS!!!
We keep looking to find that magic solution, the security philosopher’s stone.
It’s our obsession with the latest and greatest tools out there on the market. We are all guilty of it: “If we just had this new, wonderful gadget, doodad, or earth-shattering widget I could get so much more done.” Vendors obviously don’t help with this situation, and yes this is coming from a vendor. But I am trying to make a point. We have built out our tool suites in security to get better at protecting ourselves, and we have succeeded at that. However, I feel we have lost our way a bit in how to start the security process.
Now is a perfect time to step back and look at where it all begins. It starts with people and education. Our users need greater awareness of the virtual environment they are wading into on a daily basis from their corporate assets: phone, laptop, desktop or all of the above.
I first heard the KISS (Keep it Simple Stupid) process when I was a kid. It impressed me then and it impresses me now. When we apply it to security we should start looking at the basics:
- People
- Endpoint Controls, AV/Malware
- Patching
- Vulnerability Management
- Logging and Log Management
I put these points in this order for a reason. I humbly present the Pyramid of Problems:

Simply put, in security, people are our primary problem. They are the ones clicking on kitten videos and package tracking spear phishing emails or reading PDFs that they should have thought twice about before opening. They are the largest and most effective attack vector today.
Next is the endpoint. Do you have enough protection on the endpoint to attempt to mitigate any user or people problems that may be caused on it?
Our old friend patching usually presents your next batch of issues. Are you aware of all the patches available for the endpoint in question? Did you attempt to standardize on a gold build for your users? Did you go down the virtualized desktop route? Perhaps an even better question, are you 100% aware of all the different endpoints that are on your network today?
If you are able to know all the endpoints and have a good patch process how often does it run? In other words, are you able to act quickly and effectively to address new vulnerabilities as they become known? How are you dealing with Microsoft Tuesdays? Or Android day? Or Apple day? These all come at random times with random severities and have differing effects on your security posture.
Finally, we come to logs. That indicator of something being amiss, but what/how/why we just don’t know yet. So, we have to pull logs from everywhere we can, collect them in a single place to view them, and then have enough wide=ranging industry experience and deep enough local company or network knowledge to make sense of them all.
Oh, and I didn’t even go into cloud or remote access. We touched on BYOD, but didn’t go deep there either.
You can take the pyramid and look at it on the x axis as being the prevalence of Discovery of the problem, and you can take the y axis and look at it as complexity of Determination.
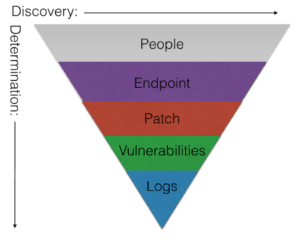
Or in simple terms: How likely am I to be notified of a problem and how often is that issue truly a problem?
People are going to create trouble tickets, and most of the time they have a legitimate issue. It may not be a security issue, but normally there is a problem. Logs can be all over the place and trying to determine an unknown issue simply from forward-leaning detection methods along with determination of it being a true positive or a false positive is incredibly hard.
So where does this lead us?
In security we can get lost walking around, simply by not seeing the forest for the trees. Time is precious but if we could just spend a little more time at the beginning – educating our users – it would pay big dividends. Then we need to work our way forward. Validate endpoints and try to get the best information you can on what is active and what isn’t. Get those systems patched and determine an ongoing process for keeping them up to date. Make sure you are scanning all the pieces of the network that need to be scanned. Keep up to date on the vulnerability announcements and use the data collected for internal information broadcasts. Logging needs to be on, it may not help you determine an outbreak every time, but it can help, and forensically it will allow you trace back through how something went wrong when it does happen.
Security is not, and in my opinion never can be, simple. But it can be made simpler and more effective by focusing our efforts on where we can get our biggest bang for the buck: our users, family, friends and education.
Don’t forget to wish your family Happy Package Tracking Phishing Season!
In the next piece I want to talk to you about how to get the simpler concepts off the ground and build a simpler security plan with the tools you already have in hand.

0 Comments