Scoring: "Trust but Verify"
POSTED BY RYAN TROSTEvery security provider publishes a risk score…BUT NOT US! Instead of adding to the data noise – we allow teams to be more efficient with scores! A lot of consumers of intelligence take vendor scores at face value but that is ‘noob’ mistake #1 – you always need to “trust but verify” especially when it comes to risk scores because they are so subjective and often times are accompanied with little supporting justification!! Why verify? Because providers must cater to all customers across all verticals, and therefore, they need to distribute their intelligence in a “least common denominator” vantage point, which dilutes the relevancy to the 85% of their customers that might not be directly affected.
Lots of intelligence providers and “blackbox” TIPs include a threat score but those scores aren’t industry or vertical specific but rather a generic global risk score. This leads companies to a false sense of risk management because that adversary, attack or indicator might not even be launched against your industry but yet it steals cycles from your team because the provider scored it high. And even worse is the provider doesn’t provide ANY supporting justification to their reasoning.
We sat down with a wide range of customers, both with mature and less mature programs, and developed a multi-tiered scoring model.
As you can tell from my expiration blog there’s a running TQ theme about incorporating a maturity model for core features as we realize not all teams or workflows are identical and as a platform we need to allow customers to dictate their own comfort levels. Sidenote: in my operational SOC days, this was a monumental pet peeve of mine as a vendor would release a new major feature and my SOC team was forced to comply with how “they” built it…even when it broke several of our workflows and data handoffs! These approaches, though exponentially more difficult to build, allows customers to self-assess internal capabilities, select the tier most appropriate for them, and mature the feature and the team in unison – if they even want to enable the feature!
The underlying premise of our scoring methodology is to:
1) Allow customers to control their own destiny through weights and prioritization
2) Allow customers to select which elements are core to their defensive posture – because nobody knows your environment better than you
3) Accurately reflect the risk posed against the customer’s specific company
4) Find middle ground – too few elements does not accurately reflect the risk, whereas, too many elements overwhelms customers and is ignored
5) Incorporate machine-learning so TQ can automatically enhance risk scores or notify analysts of needed adjustments
6) AT ALL TIMES display how the score was calculated! …much like my 5th grade math teacher lecturing us that we need to “show our work” and not just the answer
7) And most importantly, ensure the score reflects local environmental variables (i.e. sandbox results, ticket results, observed dates, etc.)
Let’s dive slightly deeper on 2 very practical and critical use cases revolving around #1 and #3.
1) Allow customers to control their own destiny through weights and prioritization:
The calculation of the intelligence score is important…but the constant re-evaluation of that score ensures situational understanding of that intelligence . As your team and defenses continue to augment existing intelligence it is paramount the score reflect the new elements of intelligence – increment or decrement. So if a pre-existing indicator “re-enters” the system the fact that a second (or third or fourth) source is reporting it provides a need to re-evaluate the threat score of that indicator.
…but this is threat intelligence and threat intelligence is NEVER “that” easy! The reverse can also be true. The innovative and likely a bit of a controversial vantage point to additional sources is when an additional source could pose a negative effect on the risk score. This begins to peel off layers of the onion to a more mature capability allowing customers to control their own destiny through weights and prioritization.
3) Accurately reflect the risk posed against the customer’s specific company:
As mentioned above threat intelligence providers are offering “global” risk scores based on their research and visibility…but that is NOT a 1:1 parity and shouldn’t always be taken at face value. In order to really maximize your threat intelligence you need to automatically re-calculate it (when applicable) during the ingestion process. For instance CrowdStrike and iSIGHT Partners include a “Target Industry” attribute in their feed – if an indicator’s target industry is Energy with a risk score of HIGH does that (or should that) translate evenly if my company is Retail?! Absolutely not! Does the indicator still pose a threat – ABSOLUTELY BUT NOT at the same threat level as the industry being targeted.A TIP needs to allow customers the ability to refine the incoming scores based on their own vantage point as seen in Figure 1.
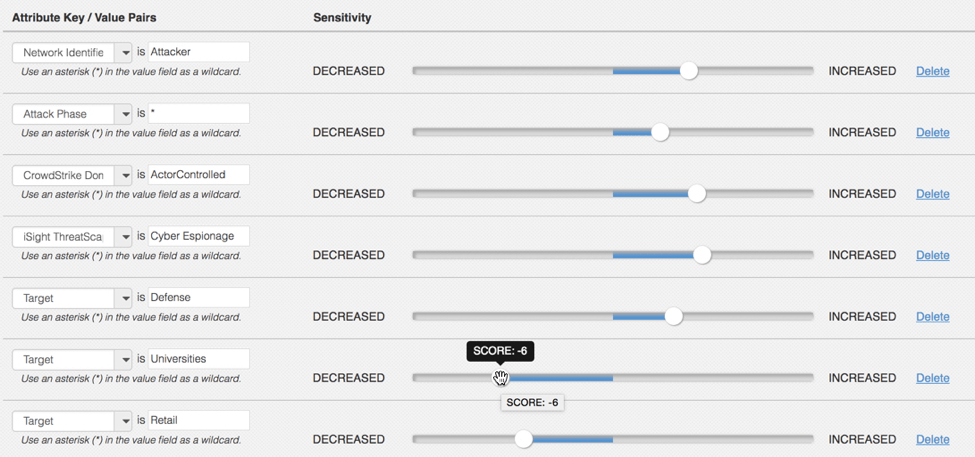
Figure 1 – a snippet of the scoring configuration highlighting negative scoring and robust customization
A TIP needs to allow customers the ability to refine the incoming scores based on their own vantage point.
…keeping in mind when we blog about Aging…we leverage the same dataset/approach.
Regardless of which intelligence score your company tests as ground-truth, whether internally designed or externally relied upon, ensure it provides an overarching umbrella approach providing ample supporting datapoints!

0 Comments