TIP vs. SIEM vs. Ticketing System – Part 2
POSTED BY RYAN TROSTIf you read part 1 of this post you understand why funneling threat intelligence directly into a SIEM isn’t a viable option if you want to get the most from your external data feeds and your analysts’ time and talent. Now let’s take a closer look at the limitations of ticketing systems to handle threat intelligence and why a threat intelligence platform is a better alternative.
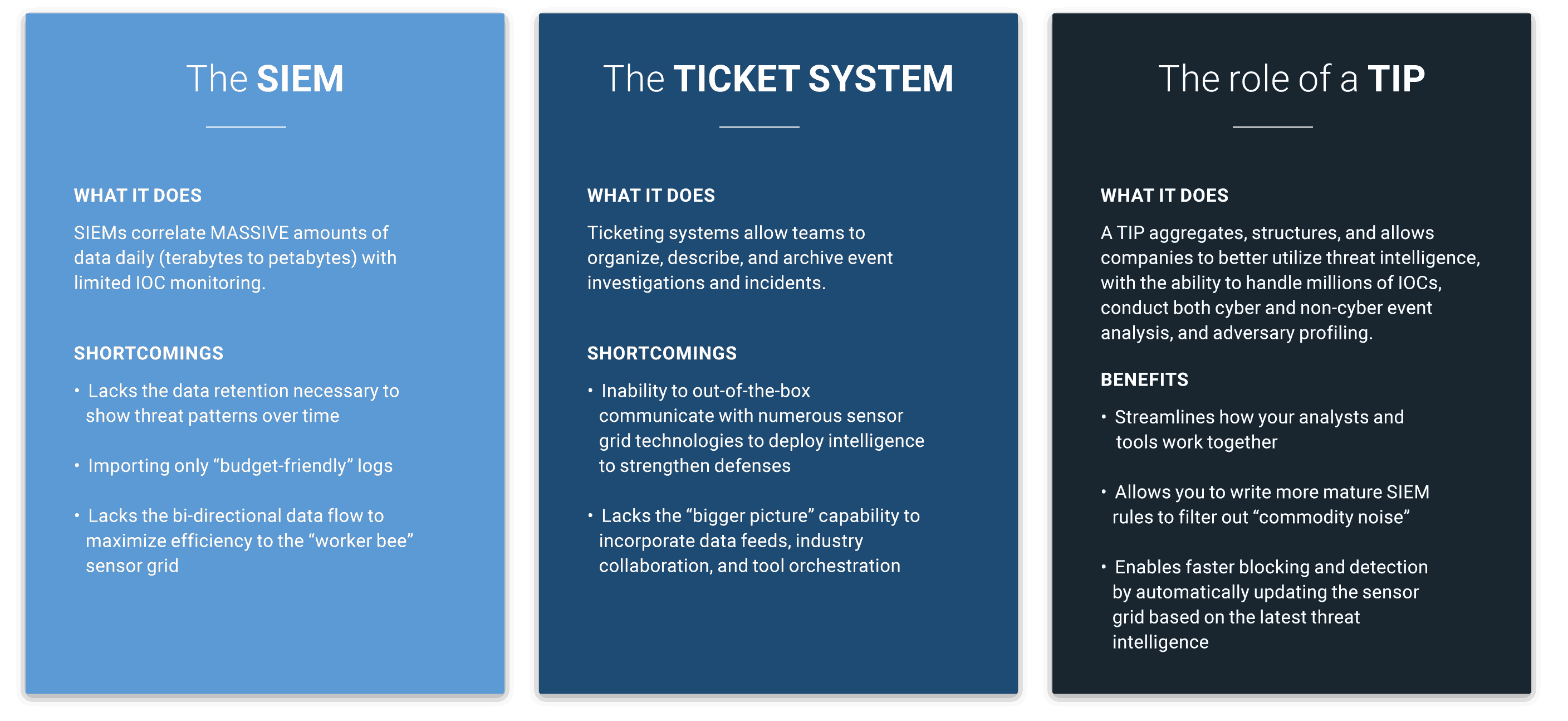
The Role of the Ticketing System
Ticketing systems allow teams to organize, describe, and archive event investigations and incidents. They focus on fact or fiction during incident response activities as analysts reverse the trail of breadcrumbs of an intrusion. Their gap in supporting a threat intelligence program lies in their current inability to “out-of-the-box” communicate with numerous sensor grid technologies to deploy intelligence to strengthen defenses.
This limitation is due to the fact that ticketing systems historically rely on either manual entry or pulling information from the SIEM – where the alerts are being correlated and triaged. They aren’t designed to relay policy changes out.
The Role of the Threat Intelligence Platform
If it isn’t obvious by now, threat intelligence platforms (TIPs) are purpose built for “threat intelligence” – a term practitioners and consumers alike are starting to understand and shape to overall industry needs. There are several TIP vendors and it is amazing how different each one is based on the background of each of the TIP’s founders.
At the bare minimum, a threat intelligence platform aggregates, structures, and allows companies to better utilize threat intelligence, with the ability to handle millions of IOCs, conduct both cyber and non-cyber event analysis, and adversary profiling.
A threat intelligence platform allows organizations to engage in the level of teamwork and collaboration required to identify which IOCs are relevant to your organization and hone in on advanced threats.
For example, IT security and IR professionals have the capability to comment on indicators; build adversary tactics, techniques, and procedures (TTP) profiles; and overlay selected “events” over a longer period of time to look for and identify patterns.
Streamlining how your analysts and tools work together, threat intelligence platforms are ideally suited to trigger the team’s internal intelligence workflow and finish that workflow with a feedback loop. By funneling threat intelligence into a TIP and then allowing the TIP to distribute the information to multiple systems within your environment, you can enhance your threat intelligence. TIPs complement SIEMs by allowing customers to overcome these limitations by maintaining a tactical strategy but extending to a more strategic adversary focus. This includes feeding information into the SIEM to enrich the alerts inside the SIEM with additional context (i.e. malware family, kill chain stage, IR ticket #, score, etc.). This allows folks to write more mature SIEM rules to filter out “commodity noise”. A TIP also enables faster blocking and detection by automatically updating the sensor grid based on the latest threat intelligence.
Both SIEMs and, ticketing systems play a key role in the threat intelligence lifecycle because by feeding data and indicator-rich tickets back into the TIP, organizations can understand which sources of intelligence provide higher fidelity alerts for detecting and preventing future incidents. TIPs can also query ticketing systems with newly created indicators to enrich whether or not that indicator has been seen before and, if so, what steps did that previous analyst take in triaging the alert.
Just like Lucy and Ethel couldn’t keep up with the volume of chocolates coming down the conveyor belt, your SIEM and ticketing system can’t keep up with the volume of intelligence available today while still maintaining their own daily efforts. By pushing intelligence into a threat intelligence platform and then working in concert with your SIEM and ticketing system you can maximize the value of external feeds, enhance your overall threat intelligence, and increase the effectiveness of your detection systems to stop threats faster.

0 Comments